Exploit Kit still sharpens a sword
Note: This blog post doesn’t make sense to many
It’s 2021 now. Moreover, the quarter has already passed. I thought Drive-by Download attack was dead four years ago. Angler Exploit Kit has disappeared, pseudo-Darkleech and EITest campaign have disappeared, and RIG Exploit Kit has also declined. At that time, Drive-by Download attack was definitely supposed to die. However, even if in 2021, it will not disappear fire still slightly.
In April 2021, I received some incredible notices. For example, there are the following notifications.
- PurpleFox Exploit Kit has started exploiting CVE-2021-26411
- RIG Exploit Kit has started exploiting CVE-2021-26411
- Bottle Exploit Kit is back, and has started exploiting CVE-2020-1380 and CVE-2021-26411
- Underminer Exploit Kit is back
Repeat again. It’s 2021 now. Not 2017. Internet Explorer was taken away by Chrome and Edge, and Drive-by Download attack was supposed to die. Why are there still Drive-by Download attacks? Here are some reasons, including the opinions of your friends.
- Internet Explorer is still used in some countries/regions including Japan
- Due to the influence of corona, remote work has increased, and the number of users with network security vulnerabilities has increased
- Internet Explorer vulnerabilities still discovered and exploit code published
In reality, these are intricately intertwined, and there may be different reasons.
In any case, Drive-by Download attacks are still being observed. Moreover, it is a little more active. This is irrelevant for most people. Because most people don’t use Internet Explorer. If you don’t use Internet Explorer, a typical Exploit Kit attack is not a threat. A small number of targeted attacks may use Chrome’s 0day, which is not discussed here.
For the few enthusiastic Internet Explorer users that exist, I write this blog post. In other words, as of April 2021, I will introduce the characteristics of common Drive-by Download attacks that you may encounter. Thanks to my friends (@jeromesegura, @nao_sec members) for helping me write this blog post.
Exploit Kit Landscape
As of April 2021, the following 6 types of Exploit Kits have been observed to be active.
- RIG
- Spelevo
- PurpleFox
- Underminer
- Bottle
- Magnitude
nao_sec has been running a fully automatic Drive-by Download attack observation environment called Augma System[1] for three years. The data observed by this is as follows. Some Exploit Kits are not counted because they are observed in different environments.
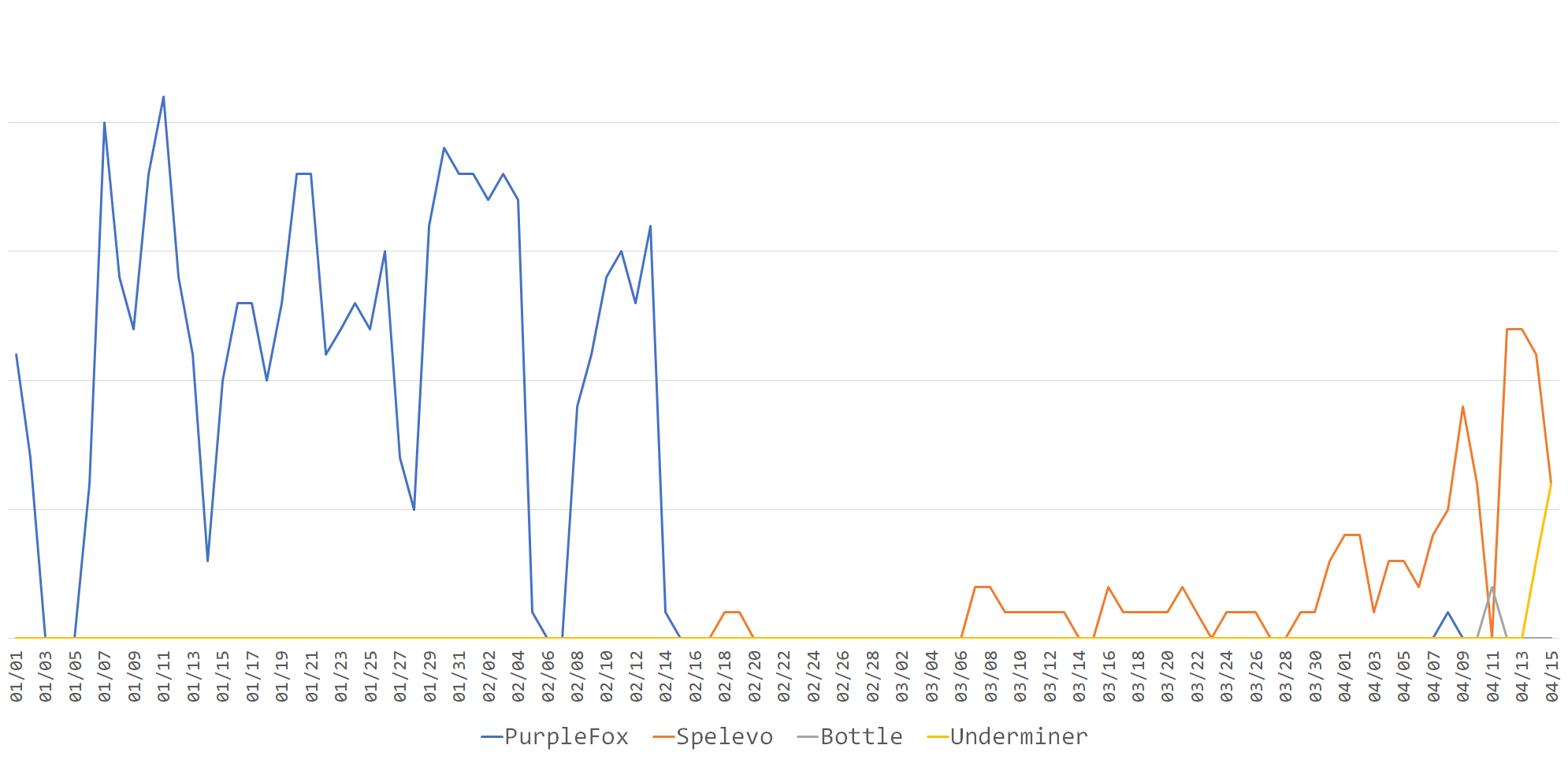
The features of the 6 types of Exploit Kits currently observed are as follows.
| Private | Update | Exploit | |
|---|---|---|---|
| RIG | No | Yes | CVE-2020-0674, CVE-2021-26411 |
| Spelevo | No | No | CVE-2018-8174, CVE-2018-15982 |
| PurpleFox | Yes | Yes | CVE-2021-26411 |
| Underminer | Yes | No | CVE-2018-15982 |
| Bottle | Yes | Yes | CVE-2020-1380, CVE-2021-26411 |
| Magnitude | Yes | Yes | CVE-2021-26411 |
Here is sample traffic for each.
RIG Exploit Kit
RIG is an Exploit Kit that has been active since around 2014. It was extremely active from 2016 to 2017, but then declined with the advent of Fallout and others. However, it is still active in 2021.
RIG started abusing CVE-2021-26411 in April 2021 and are still incorporating changes. Landing Pages are not obfuscated as they used to be. Very simple code. The malware is RC4 encrypted.
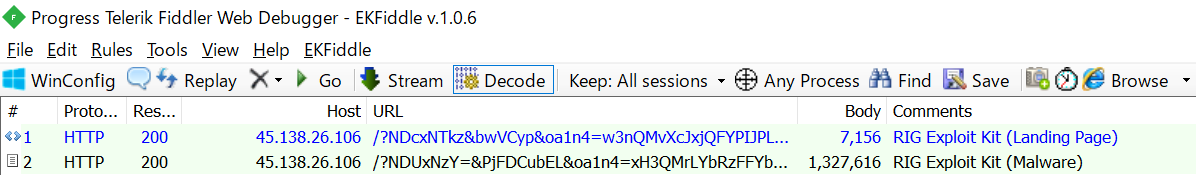
Download sample traffic here.
Spelevo Exploit Kit
Spelevo is an Exploit Kit that appeared in 2019. 2020 was very mature, but 2021 is one of the most active Exploit Kits.
Spelevo hasn’t changed for a long time. Spelevo hides the malware in the image. See this article[2] for detailed behavior.
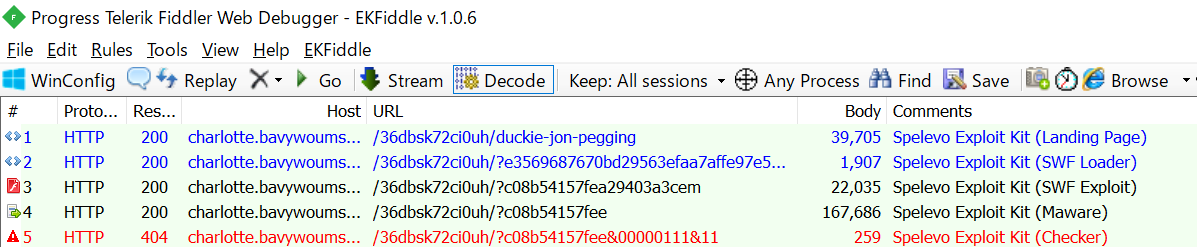
Download sample traffic here.
PurpleFox Exploit Kit
PurpleFox is an Exploit Kit that has been active since 2019. A private exploit kit for sending PurpleFox malware. It’s enthusiastic about exploit and is fairly fast at incorporating new vulnerabilities.
Spelevo has started to exploit CVE-2021-26411 in April 2021. However, the other parts have not changed for a long time.
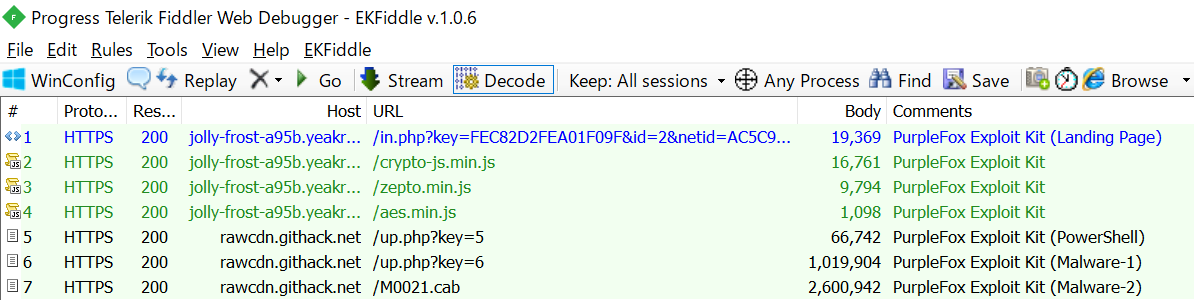
Download sample traffic here.
Underminer Exploit Kit
Underminer is an Exploit Kit that appeared in 2018. It’s a pretty distinctive Exploit Kit. It is known to be extremely difficult to analyze. It is used to deliver its unique malware called Hidden Bee. See this article[3] for more details.
Underminer has a cycle of activity for several months and then silence for several months. It has been silent since the November 2020, but was revived in April 2021. But the essence hasn’t changed at all.
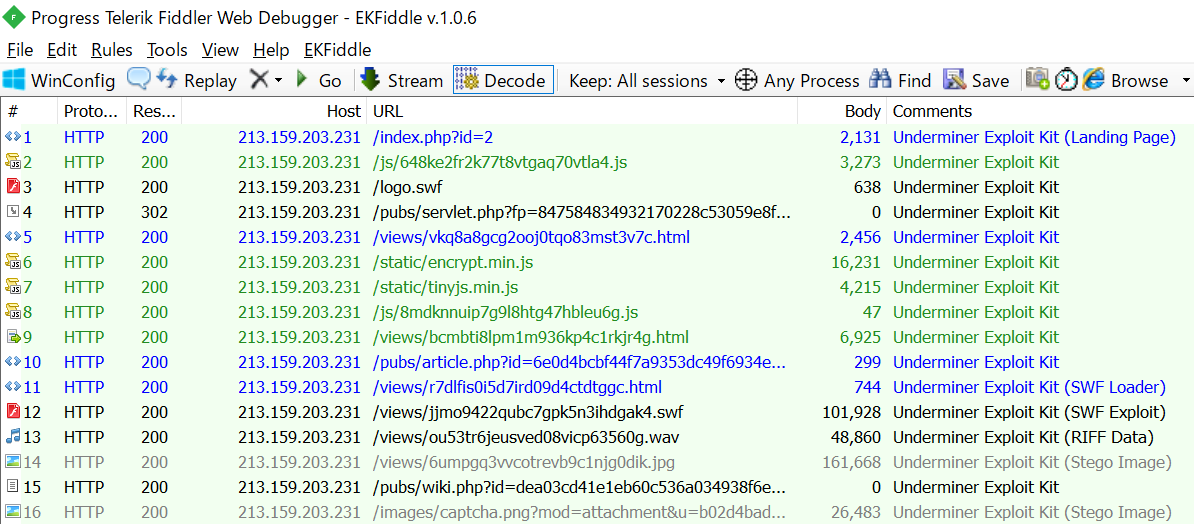
Download sample traffic here.
Bottle Exploit Kit
Bottle is an Exploit Kit that appeared in 2019. An extremely rare Exploit Kit that targets only Japan. It is used to deliver its unique malware called Cinobi.
It is one of the most active Exploit Kits in Japan. It has not been observed since November 2020, but it was revived in April 2021. It’s also worth noting that unlike other Exploit Kits, it exploits CVE-2020-1380 and CVE-2021-26411. It has been pointed out that it is related to MageCart and phishing campaigns. See this article[4] for more details.
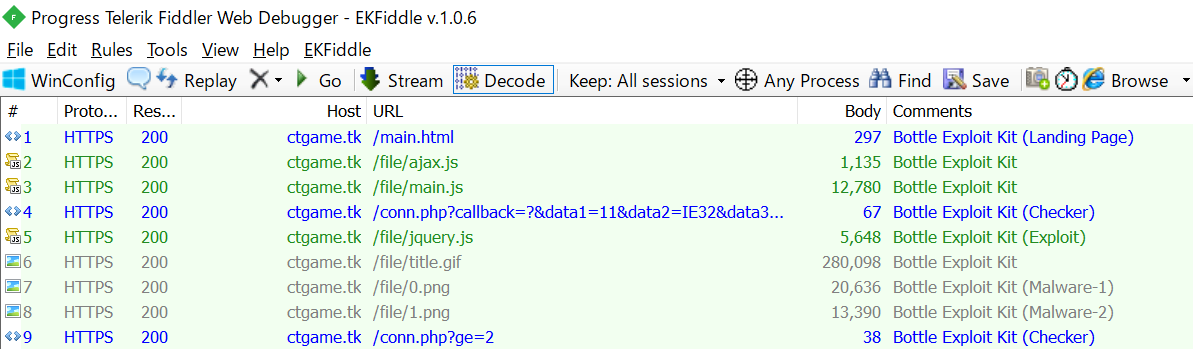
Download sample traffic here.
Magnitude Exploit Kit
Magnitude is one of the oldest existing Exploit Kits. It has been observed only in certain countries/regions such as South Korea and Taiwan, and the details have not been reported much.
Its activity was also reported in April 2021. It exploits CVE-2021-26411 and is still actively evolving.
One more: #MagnitudeEK pic.twitter.com/pOuIZzAPZG
— Jérôme Segura (@jeromesegura) April 14, 2021
Finally
Drive-by Download attacks are still observed in 2021. It has nothing to do with most people. As with Adobe Flash Player, stop using Internet Explorer immediately. That is the simplest solution. Drive-by Download attacks continue to exist with Internet Explorer.
References
[1] https://www.virusbulletin.com/uploads/pdf/conference_slides/2019/VB2019-KoikeChubachi.pdf
[2] https://insight-jp.nttsecurity.com/post/102gsqj/pseudogatespelevo-exploit-kit
[3] https://blog.malwarebytes.com/threat-analysis/2019/08/the-hidden-bee-infection-chain-part-1-the-stegano-pack/
[4] http://jsac.jpcert.or.jp/archive/2021/pdf/JSAC2021_103_koike-takai_jp.pdf
 nao_sec
nao_sec