Royal Road! Re:Dive

Abstract
We introduced the “Royal Road RTF Weaponizer” in our previous blog [1] (and presented at Japan Security Analyst Conference 2020 and CPX 360 CPRCon 2020). Royal Road is a tool shared by many targeted attack groups believed to belong to China. It’s been a year since our previous blog, and Royal Road is still in use. Here, we will introduce the Royal Road-related attacks observed during 2020.
Previous Blog
Let’s briefly review the previous blog. Royal Road is a tool that generates RTF files that exploit the Microsoft Office Equation Editor vulnerabilities (CVE-2017-11882, CVE-2018-0798, CVE-2018-0802). The details of the tool are unknown, but the RTF file generated by it has various characteristics. The definition of “RTF file generated by Royal Road” may vary from researcher to researcher. Therefore, we define a file that meets the following conditions as an “RTF file generated by Royal Road”.
- Exploiting a vulnerability in Microsoft Office Equation Editor
- Containing an object named “8.t”
However, some RTF files are likely to be related to Royal Road, even though they don’t meet the second condition. For classification purposes, we refer to this as “Related Samples”. In reality, this may also be an RTF file generated by Royal Road, but the truth is only known to the attacker. Due to the our research, we have divided these into “Royal Road Samples” and “Related Samples”. However, they are treated the same in the specific case studies below.
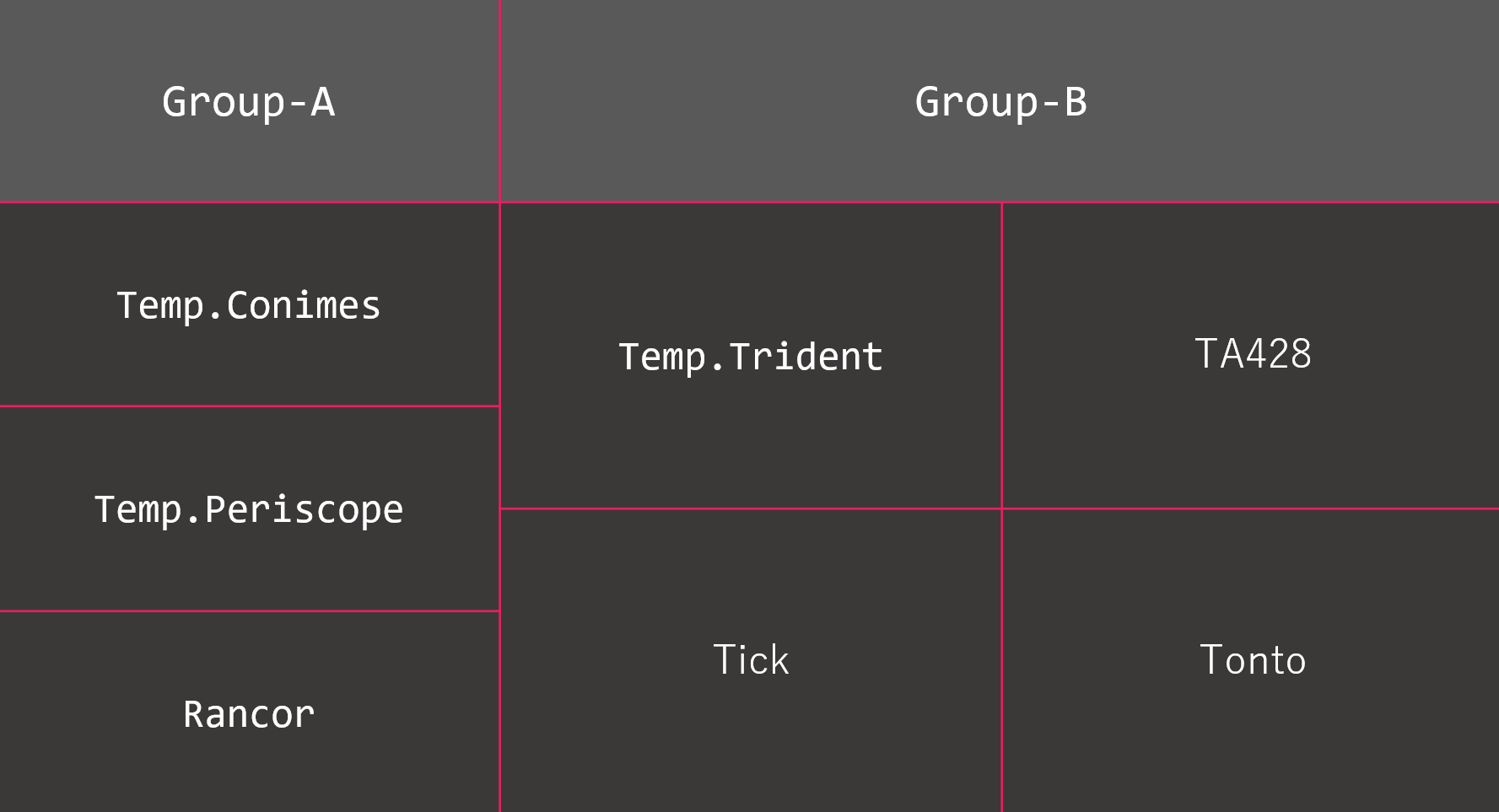
And Royal Road is shared among various attack groups believed to belong to China. Specifically, it is believed to be used by the following attack groups. The attack group alias is written for reference. Strictly speaking, these can be different. For example, TA428 and Pirate Panda are not exactly equivalent.
- Temp.Tick (BRONZE BUTLER, RedBaldKnight)
- Temp.Conimes (Goblin Panda, Cycldek)
- Temp.Periscope (Leviathan, APT40)
- Temp.Trident (Dagger Panda, IceFog)
- Tonto (Karma Panda, CactusPete, LoneRanger)
- TA428 (Pirate Panda)
- Rancor
Also, we categorized the various characteristics of the RTF files used by these groups and showed what they have in common.
Updates
It’s been a year since we introduced Royal Road. In the meantime, the RTF file, believed to have been generated by Royal Road, has been used many times in targeted attacks, and several updates have been observed. First of all, we will introduce the updates.
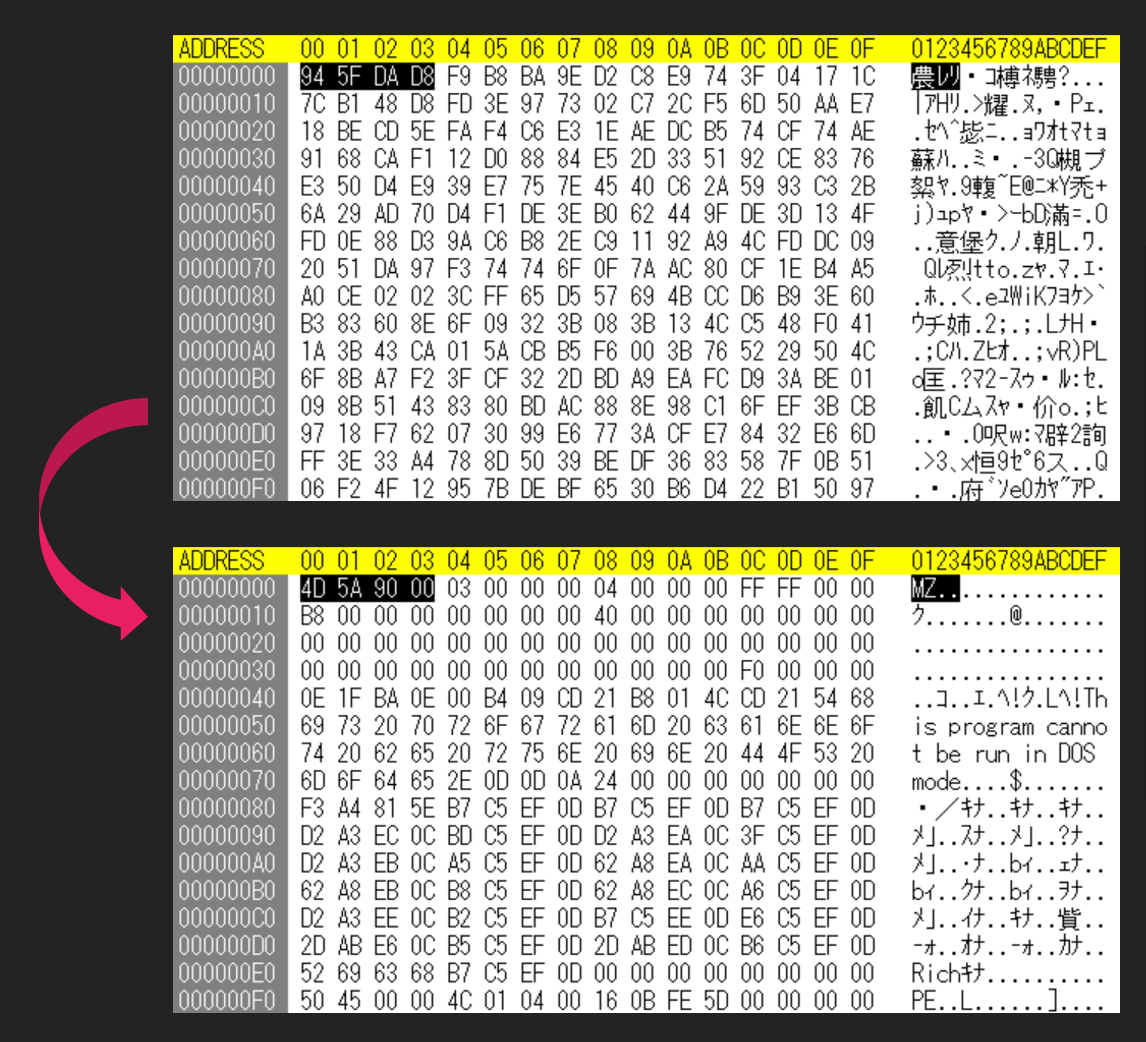
The RTF file generated by Royal Road contains encoded malware. It is decoded by Shellcode after exploit. In our previous blog, we introduced the following 5 encodings.
- 4D 5A 90 00 (not encoded)
- F2 A3 20 72
- B2 A6 6D FF
- B0 74 77 46
- B2 5A 6F 00
Many of the RTF files we observed in 2020 used the 3rd and 4th encodings. However, a few samples used the new encodings. The following 2 encodings.
- A9 A4 6E FE

This encoding can be decoded with code like the following:
dec_data = []
for i in range(len(enc_data)):
dec_data.append(((int.from_bytes(enc_data[i], "little") ^ 0x7b) + 0x7b) % 256)
- 94 5F DA D8
This encoding can be decoded with code like the following:
dec_data = []
xor_key = 1387678300
for i in range(len(enc_data)):
for _ in range(7):
x0 = (xor_key & 0x20000000) == 0x20000000
x1 = (xor_key & 8) == 8
x2 = xor_key & 1
x3 = 1 + (x0 ^ x1 ^ x2)
xor_key = (xor_key + xor_key) + x3
dec_data.append(int.from_bytes(enc_data[i], "little") ^ (xor_key % 256))
Our tool for decrypting Royal Road encoded object is already available on GitHub. It also supports the above new encodings.
https://github.com/nao-sec/rr_decoder
New Attack Groups
As we mentioned earlier, several attack groups use Royal Road. The following eight attack groups have been observed to use Royal Road (including both Royal Road Samples and Related Samples) during 2020.
- Temp.Conimes
- Tonto
- TA428
- Naikon
- Higaisa
- Vicious Panda
- FunnyDream
- TA410
Of these, we have already reported on 1-3 attack groups in our previous blog. Temp.Conimes used NewCore RAT to attack Vietnamese organizations. Tonto used Bisonal to attack organizations in East Asia such as Russia.
And the TA428 was also particularly active, using PoisonIvy, Cotx RAT, Tmanger, and nccTrojan to attack East Asian organizations such as Mongolia. We will not cover these individual cases here, but if you are interested, see the IOC chapter. For TA428, the paper [2] and blogs [3][4][5] are available from NSJ (NTT Security Japan). Please refer to that.
For Naikon, CheckPoint Research reported [6], but unfortunately, we could not observe this. Therefore, in the following, we will introduce attack cases related to Royal Road for four groups (5-8).
Higaisa
Higaisa is an attack group that seems to have been active since at least around 2016. It is primarily targeted at North Korean-related organizations and is believed to be aimed at stealing information using AttackBot, PIZ Stealer, and Gh0st RAT.
The blogs have been written by Tencent and Positive Technologies so far [7][8][9], and are attributed to (South) Korea. However, NSJ’s paper [10] showed a connection with Ghost Dragon [11] and PKPLUG [12], and it was reported that it might belong to China.
We observed an attack by Higaisa on Royal Road in March 2020.

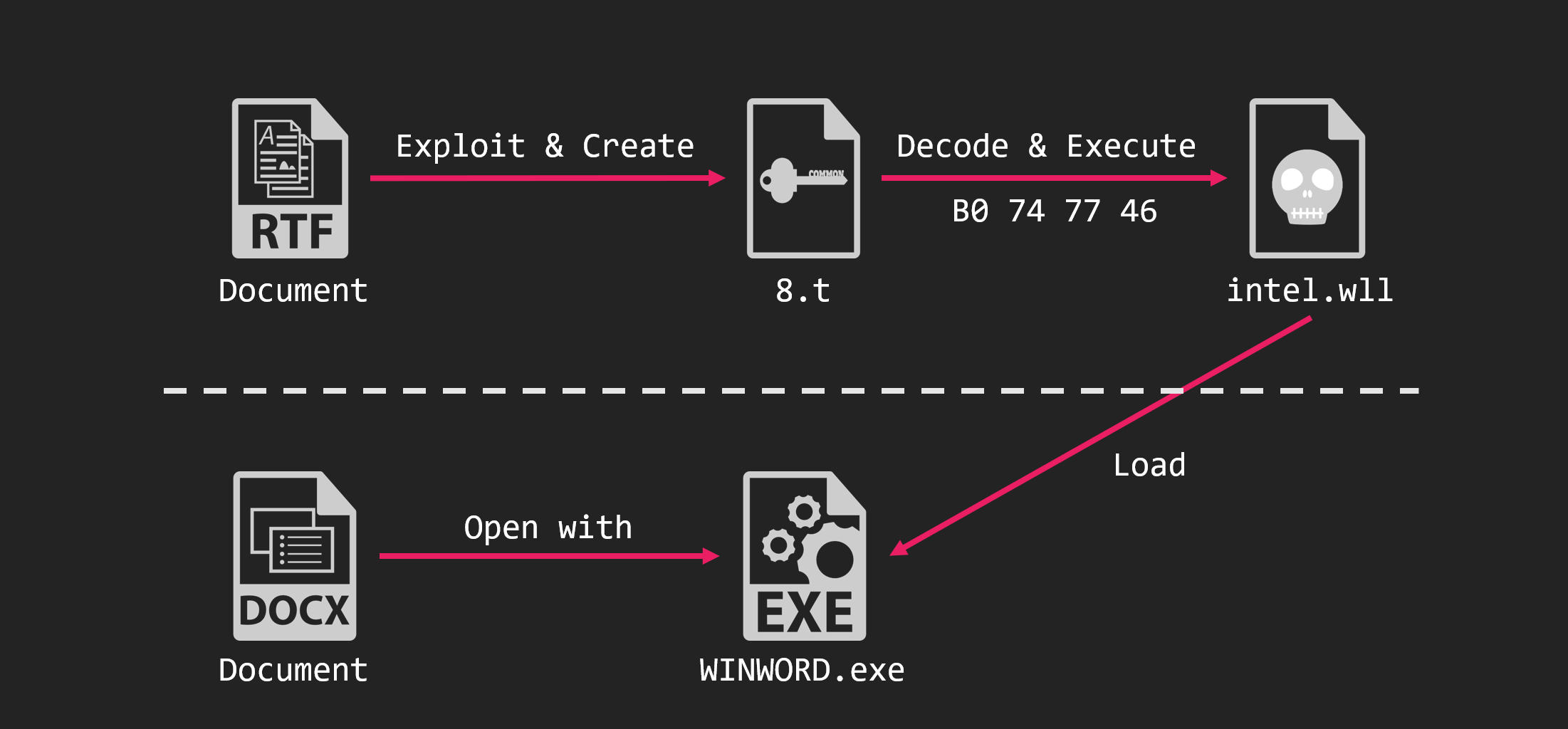
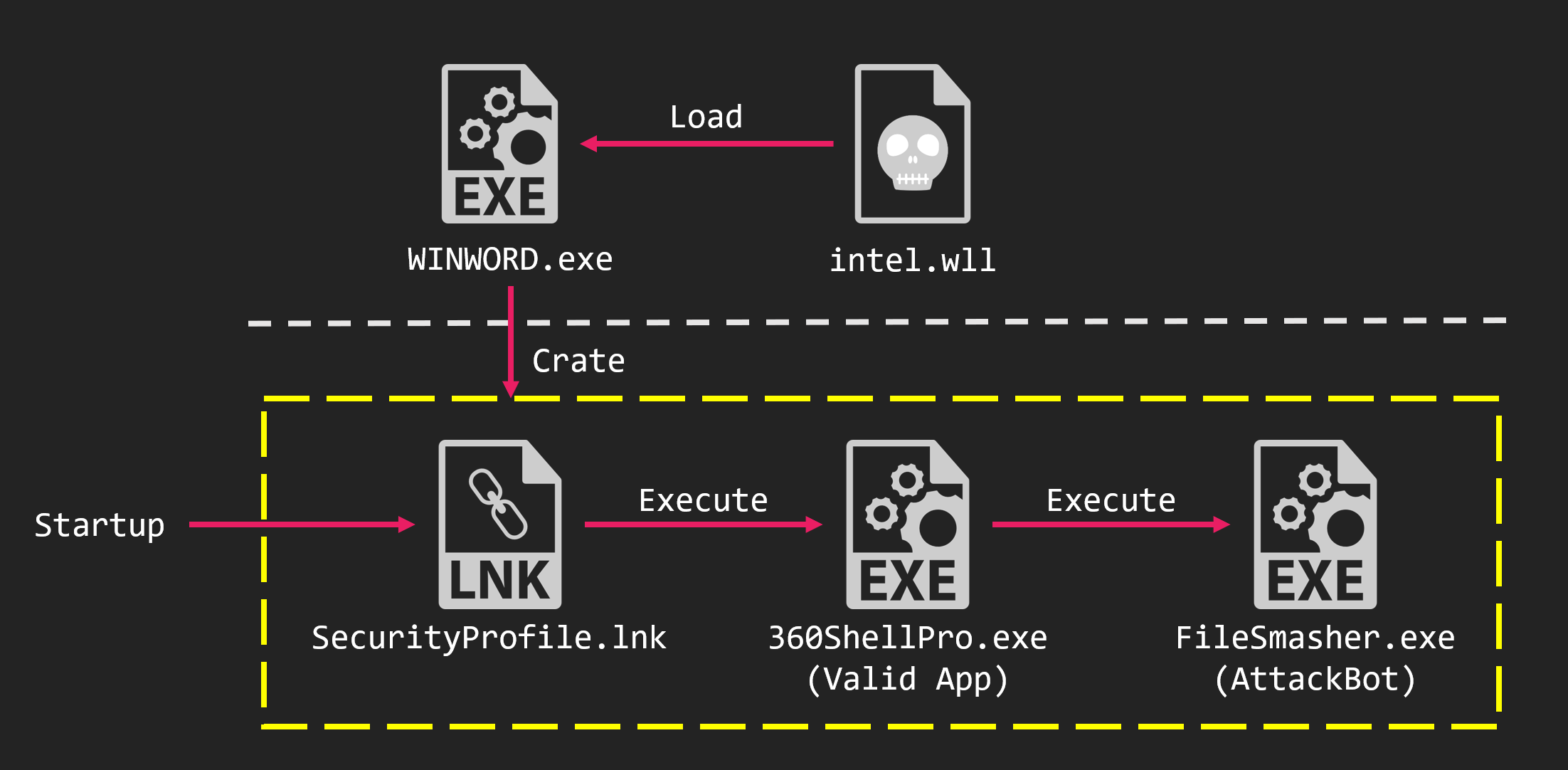
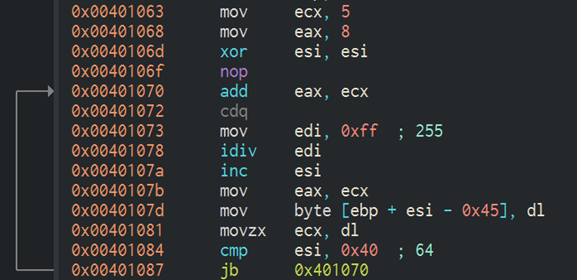
The malware executed by the Royal Road RTF was AttackBot. AttackBot is a downloader that has been used by Higaisa since at least April 2018.
Vicious Panda
Vicious Panda is an attack group reported by CheckPoint Research in March 2020 [13]. It is said to belong to China and targets East Asia such as Russia, Mongolia, and Ukraine.
We observed an attack on the Royal Road by Vicious Panda in March 2020.

It has been reported to execute malware similar to Enfal and BYEBY.
FunnyDream
FunnyDream is an attack group that is said to have been active since around 2018. It is said to belong to China and targets Southeast Asia such as Vietnam and Malaysia. FunnyDream uses Chinoxy and FunnyDream Backdoor. BitDefender has published a detailed report [14] on FunnyDream.
We observed an attack by FunnyDream from March to May 2020.

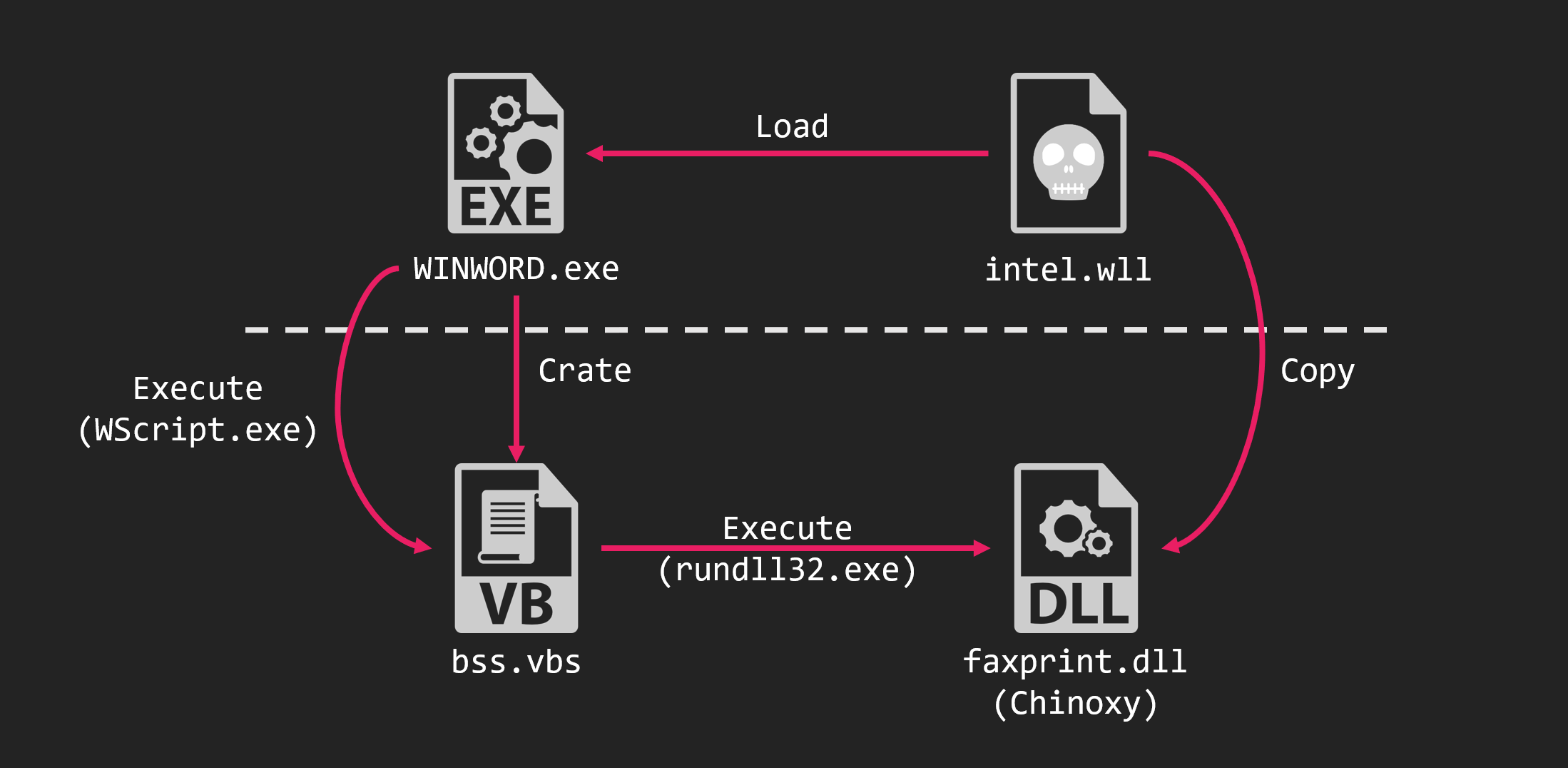
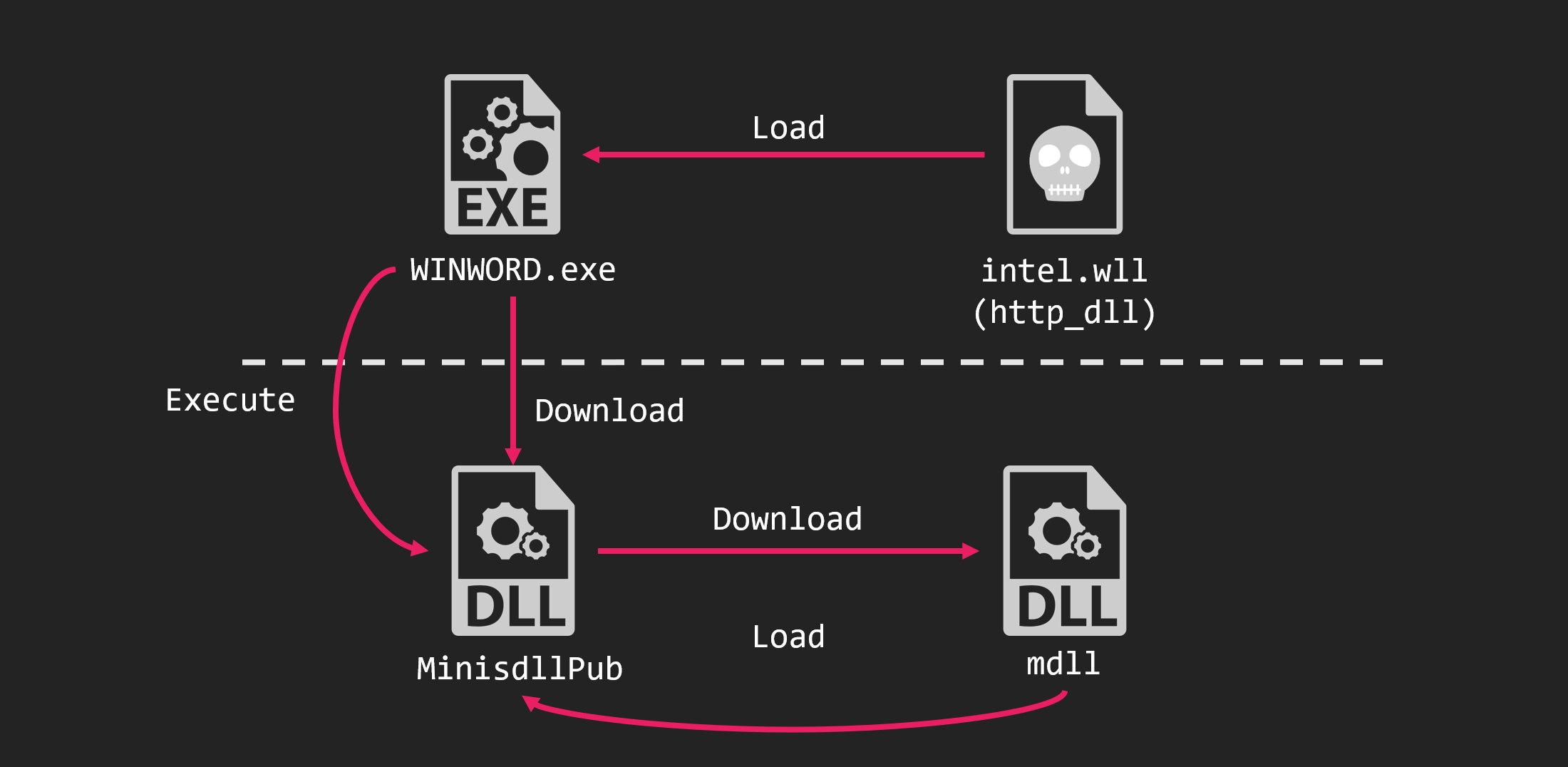
Chinoxy is a RAT that has been used by FunnyDream since around 2018. It decoded the config using two numeric data and communicates with the C&C server using its original protocol using Blowfish.
TA410
TA410 is an attack group that is said to have been active since around 2016. It is said to belong to China and is suspected to be related to APT10. The report has been published by Proofpoint [15][16][17] and is mainly targeted at public sector in the US. It uses malware called LockBack and FlowCloud.
We observed an attack by TA410 in October 2020.

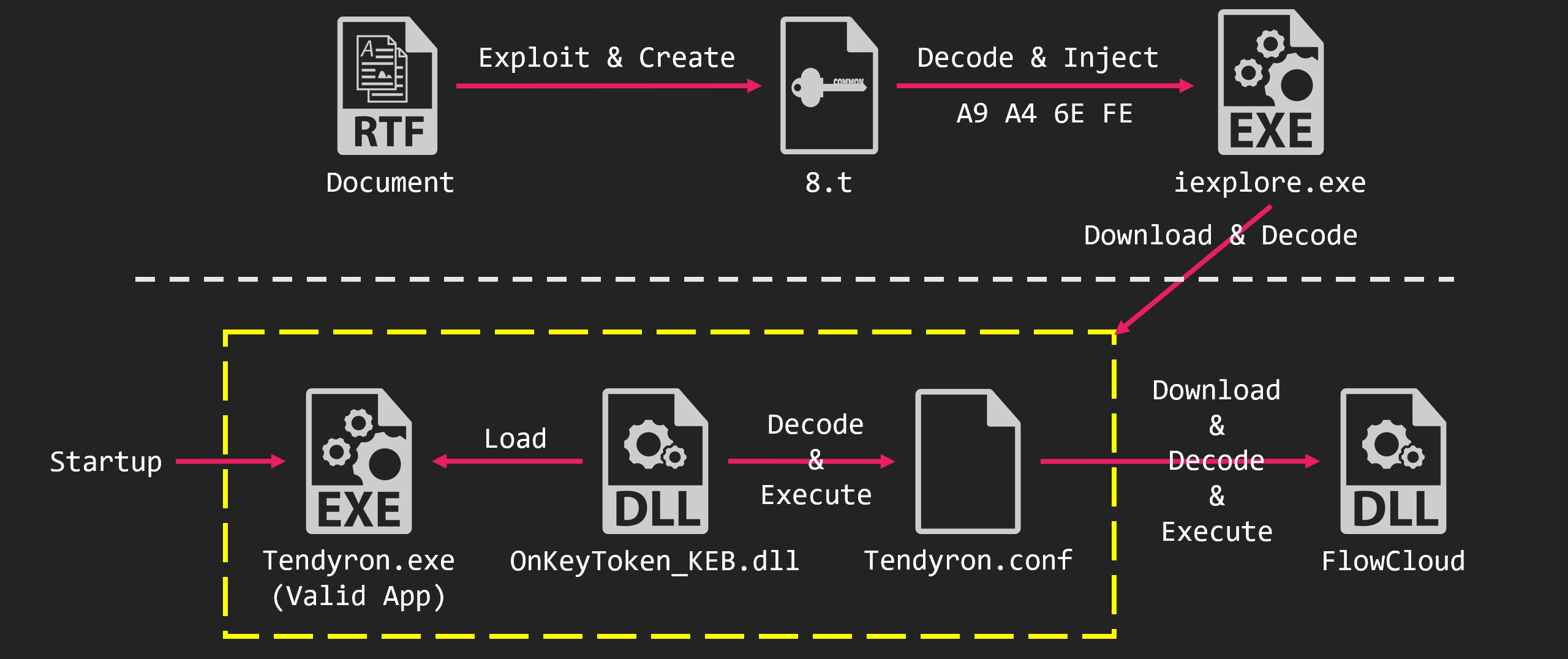
FlowCloud is a RAT reported by Proofpoint in June 2020. FlowCloud has been reported to be v4 and v5, but the FlowCloud we observed at this time was similar to v4.
Attack case against Japan
In addition to the four attack groups shown so far (Higaisa, Vicious Panda, FunnyDream, TA410), attacks that appear to be related to Royal Road have been observed. Among them, we will introduce an example of attacks on Japan. We are not able to identify which attack group made this attack. If you have any knowledge about it, please share it with us…
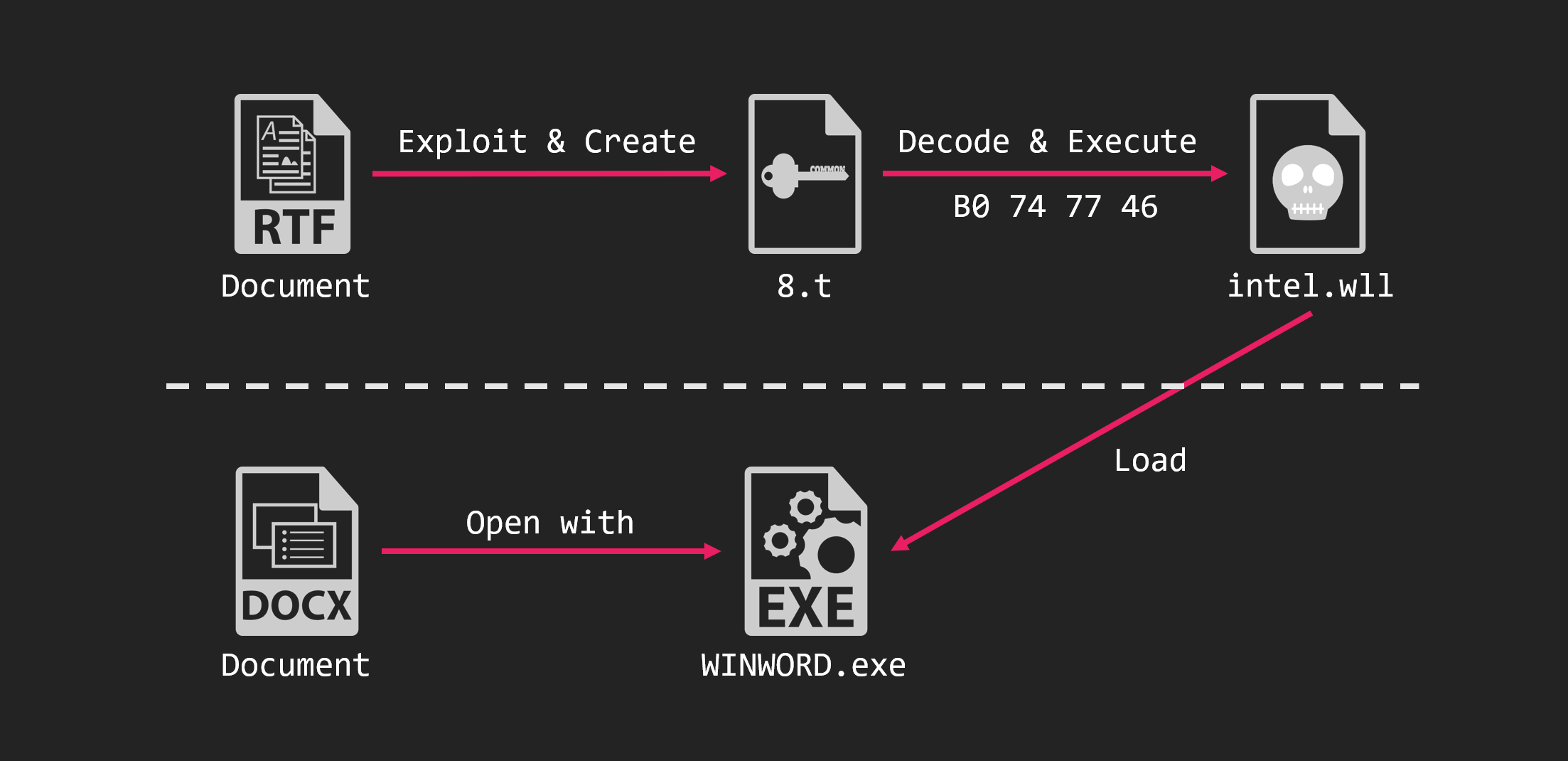
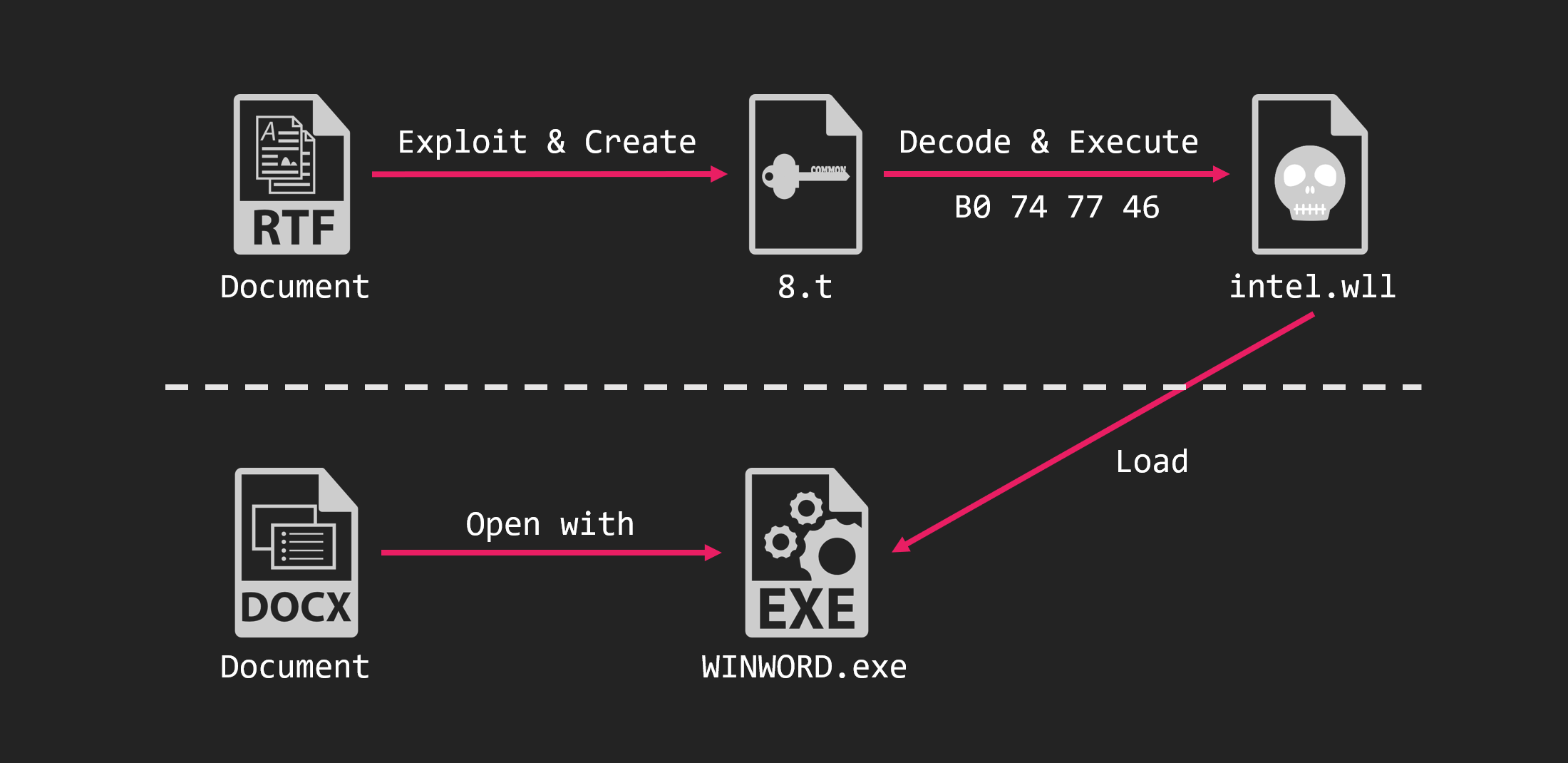
The attack on Japan took place in November 2020. The attack began with 2 RTF files attached to the email.
These RTF files did not contain an 8.t object, however did contain an associated object. This is the malware encoded by the 4th (B0 74 77 46) encoding shown above.
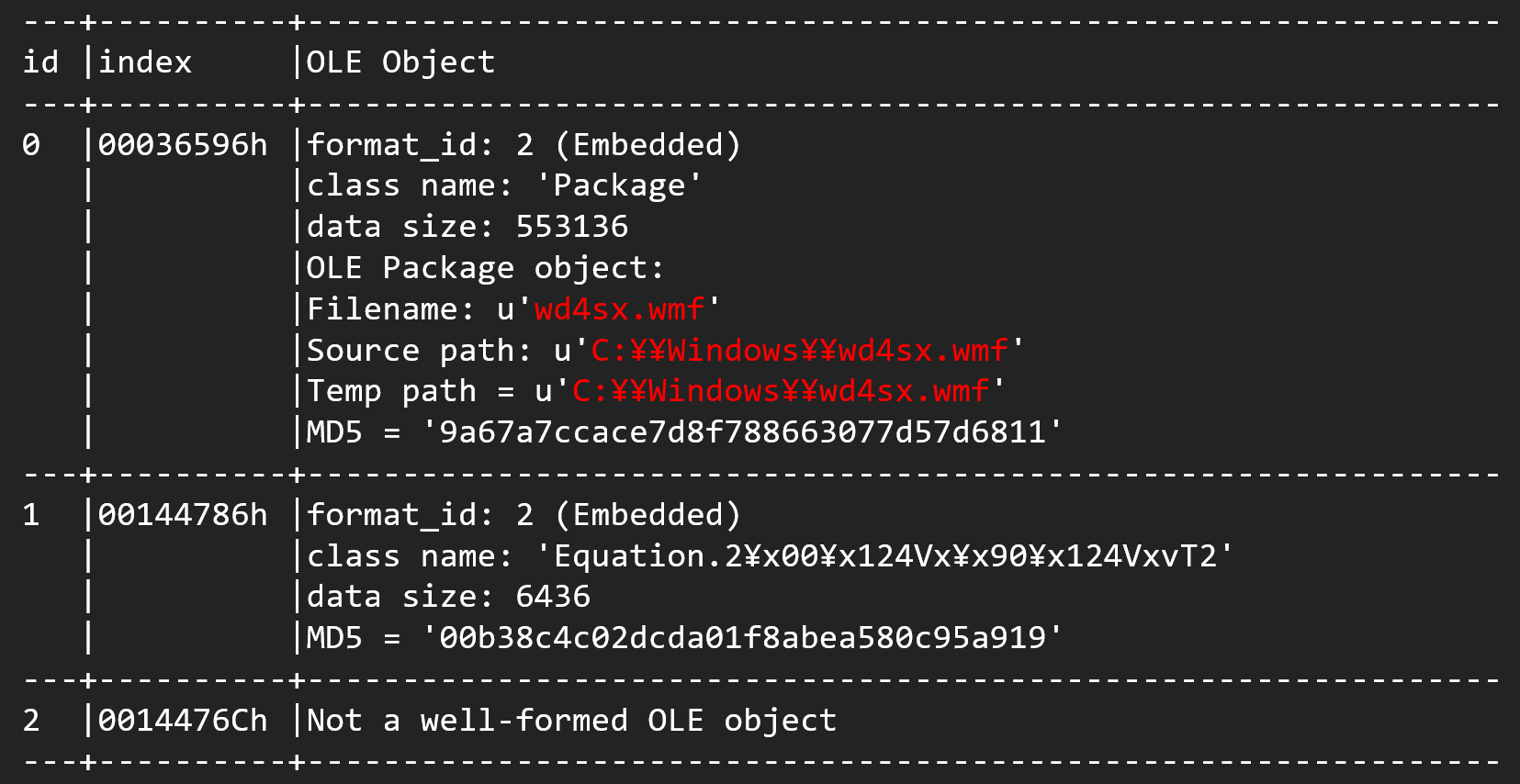
The overall picture of the attack is as follows.
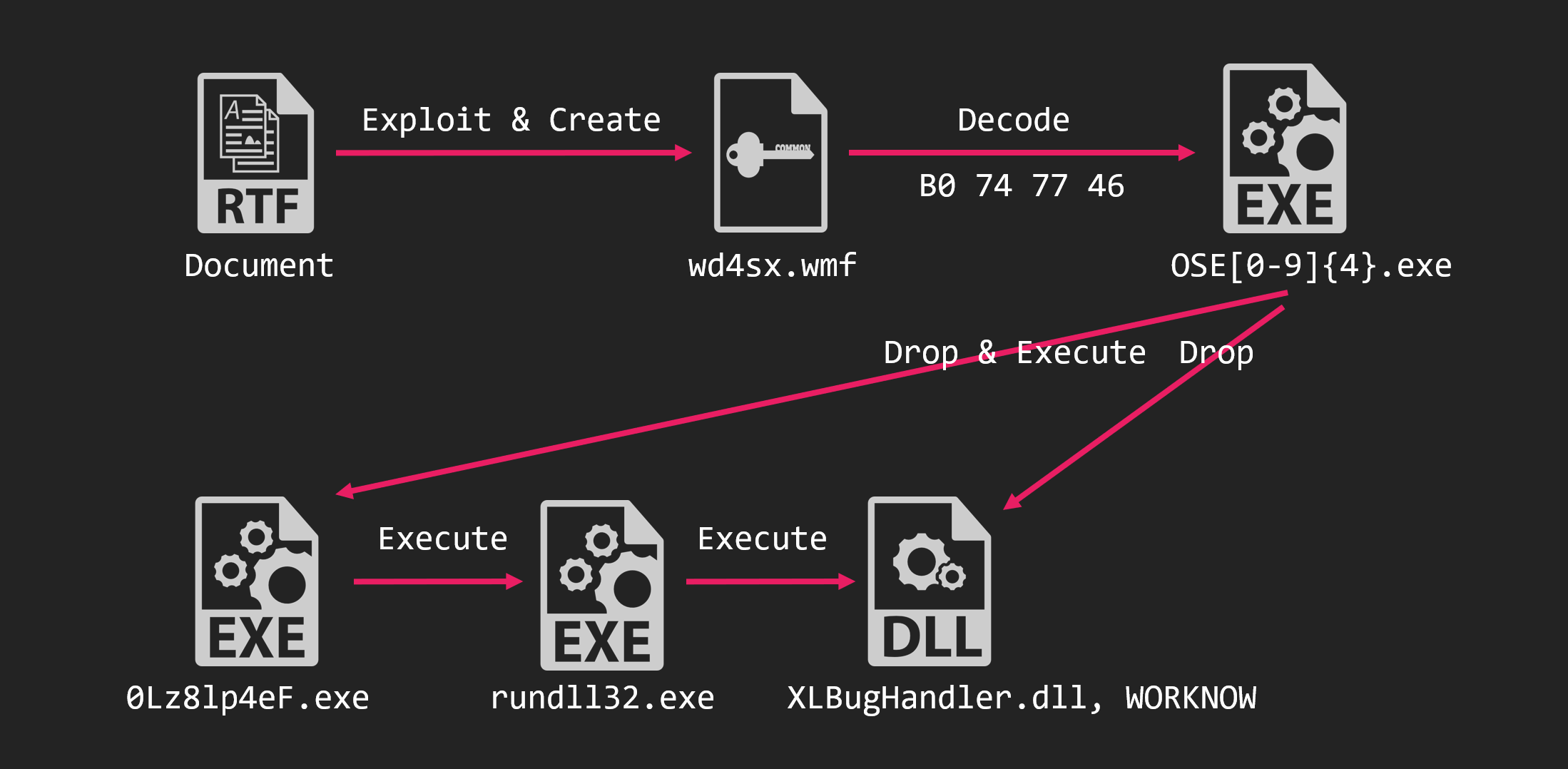
The malware executed was an unknown RAT. We call this XLBug RAT because of the characteristics left in this RAT. The RAT held information such as C&C server encoded by Base64 and XOR.
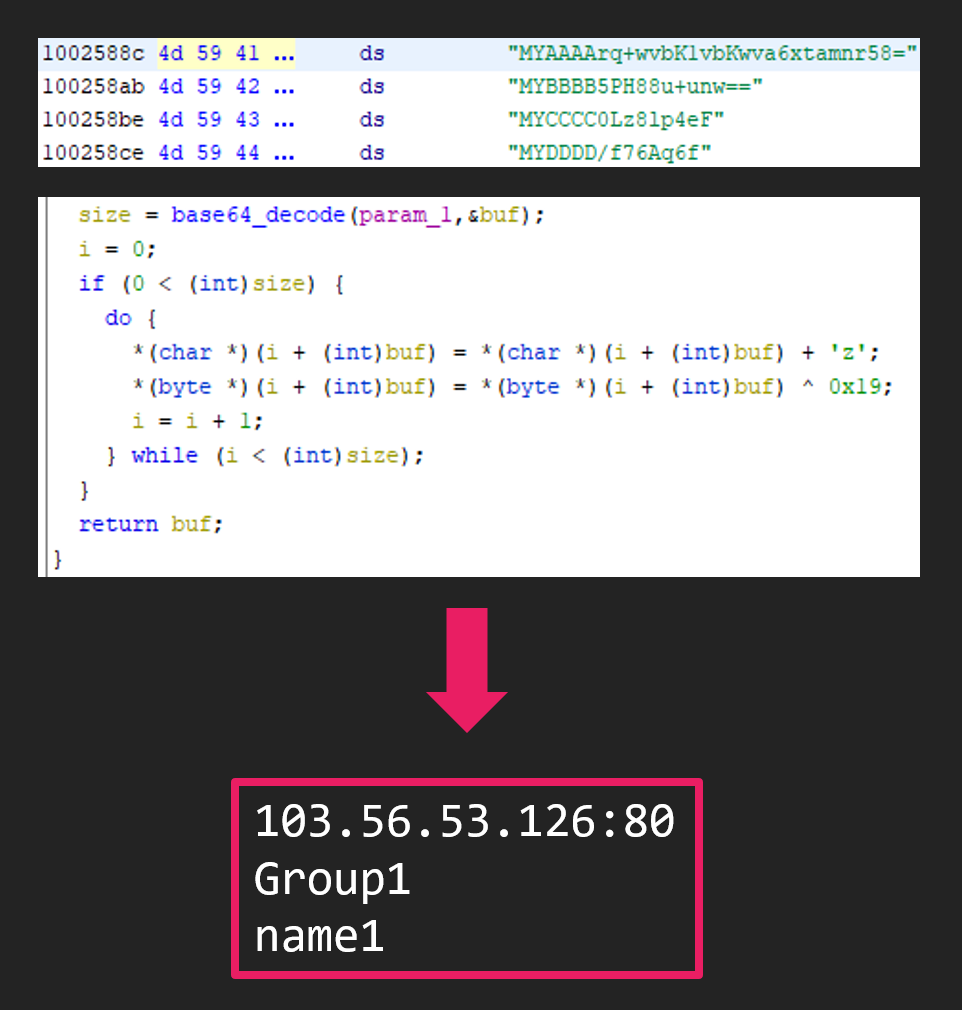
The following commands are implemented in XLBug RAT.
- Get directory information
- Get file information
- Get computer information
- Execute file
- Upload file
- Download file
- Rename file
- Delete file
- Delete itself
The naming convention and encoding of the encoded object contained in the RTF are similar to those of the TA428. However, we could not say that this was a TA428 attack.
Relationship
In the previous blog, we summarized the characteristics of attack groups that use Royal Road. We used it to divide the attack groups into two groups. However, by 2020, those characteristics are almost meaningless. It has been standardized or deleted. It’s not as easy to group as it used to be. In the first place, the groups sharing Royal Road should be close. We do not classify further, but if you have any comments please let us know.
Yara Rule
The GitHub repository we shared in the previous blog is still being updated.
https://github.com/nao-sec/yara_rules
IOC
The IOC sheet shared in the previous blog is still being updated.
https://nao-sec.org/jsac2020_ioc.html
Tool
The tool used by Royal Road to decrypt encoded object is still being updated.
https://github.com/nao-sec/rr_decoder
Wrap-Up
The attacks using Royal Road have decreased compared to 2019, but are still ongoing. There are many cases of attacks by TA428 and Tonto, but other attacks by different attack groups (Higaisa, Vicious Panda, FunnyDream, TA410) have also been observed.
The attacks on Japan have also been observed and we were unable to identify this with a known attack group. The use of Royal Road by these unknown attack groups is expected to continue.
In addition to Royal Road, there are other cases, such as the Tmanger family, that appear to share tools among multiple targeted attack groups. We should continue to pay close attention to these tool sharing cases.
Acknowledgments
“nao_sec” is an independent research team that does not belong to any company. Individuals belong to each company and engage in research, but the activities of nao_sec still maintain their independence from each company. We are grateful to all of you who cooperated with our research activities every day.
References
[1] nao_sec, “An Overhead View of the Royal Road”, https://nao-sec.org/2020/01/an-overhead-view-of-the-royal-road.html
[2] NTT Security Japan, “Operation LagTime IT: colourful Panda footprint”, https://vblocalhost.com/uploads/VB2020-Ozawa-etal.pdf
[3] NTT Security Japan, “Panda’s New Arsenal: Part 1 Tmanger”, https://insight-jp.nttsecurity.com/post/102gi9b/pandas-new-arsenal-part-1-tmanger
[4] NTT Security Japan, “Panda’s New Arsenal: Part 2 Albaniiutas”, https://insight-jp.nttsecurity.com/post/102gkfp/pandas-new-arsenal-part-2-albaniiutas
[5] NTT Security Japan, “Panda’s New Arsenal: Part 3 Smanager”, https://insight-jp.nttsecurity.com/post/102glv5/pandas-new-arsenal-part-3-smanager
[6] CheckPoint Research, “Naikon APT: Cyber Espionage Reloaded”, https://research.checkpoint.com/2020/naikon-apt-cyber-espionage-reloaded/
[7] Tencent, “APT攻击组织”黑格莎(Higaisa)”攻击活动披露”, https://s.tencent.com/research/report/836.html
[8] Tencent, ““Higaisa(黑格莎)”组织近期攻击活动报告”, https://s.tencent.com/research/report/895.html
[9] Positive Technologies, “COVID-19 и новогодние поздравления: исследуем инструменты группировки Higaisa”, https://www.ptsecurity.com/ru-ru/research/pt-esc-threat-intelligence/covid-19-i-novogodnie-pozdravleniya-issleduem-instrumenty-gruppirovki-higaisa/
[10] NTT Security Japan, “Crafty Panda 標的型攻撃解析レポート”, https://www.nttsecurity.com/docs/librariesprovider3/default-document-library/craftypanda-analysis-report
[11] Cylance (BlackBerry), “The Ghost Dragon”, https://blogs.blackberry.com/en/2016/04/the-ghost-dragon
[12] Palo Alto Networks, “PKPLUG: Chinese Cyber Espionage Group Attacking Southeast Asia”, https://unit42.paloaltonetworks.com/pkplug_chinese_cyber_espionage_group_attacking_asia/
[13] CheckPoint Research, “Vicious Panda: The COVID Campaign”, https://research.checkpoint.com/2020/vicious-panda-the-covid-campaign/
[14] BitDefender, “A Detailed Timeline of a Chinese APT Espionage Attack Targeting South Eastern Asian Government Institutions”, https://labs.bitdefender.com/2020/11/a-detailed-timeline-of-a-chinese-apt-espionage-attack-targeting-south-eastern-asian-government-institutions/
[15] Proofpoint, “LookBack Malware Targets the United States Utilities Sector with Phishing Attacks Impersonating Engineering Licensing Boards”, https://www.proofpoint.com/us/threat-insight/post/lookback-malware-targets-united-states-utilities-sector-phishing-attacks
[16] Proofpoint, “LookBack Forges Ahead: Continued Targeting of the United States’ Utilities Sector Reveals Additional Adversary TTPs”, https://www.proofpoint.com/us/threat-insight/post/lookback-forges-ahead-continued-targeting-united-states-utilities-sector-reveals
[17] Proofpoint, “TA410: The Group Behind LookBack Attacks Against U.S. Utilities Sector Returns with New Malware”, https://www.proofpoint.com/us/blog/threat-insight/ta410-group-behind-lookback-attacks-against-us-utilities-sector-returns-new
 nao_sec
nao_sec