Building Casper's Shadow

Introduction
A few days ago, we came across a peculiar file. It looked like some kind of builder, and a quick glance at the settings piqued our interest. It appeared to be a ShadowPad builder, probably created around 2021.
ShadowPad builders became a topic of conversation around the time of the i-Soon leak, but we had never seen the actual builder ourselves. This is likely true for most of you as well.
We were so intrigued that we carefully investigated this builder and reviewed past attack campaigns. In this article, we will share how attackers build ShadowPad, what we discovered through our investigation, and our insights.
Our investigation is still ongoing. We would love to engage in active discussions with you. If you have any opinions or comments, please feel free to contact us.
[Note] What we discovered this time is a builder. It does not include a controller. Therefore, it is not possible to control what is generated by this builder. In other words, this builder alone is not meaningful in the real world.
Background
In June 2024, we happened to read a research memo from a year ago. We often read past memos for a change of pace. In doing so, we recalled an attack on Kyrgyzstan in April 2023.
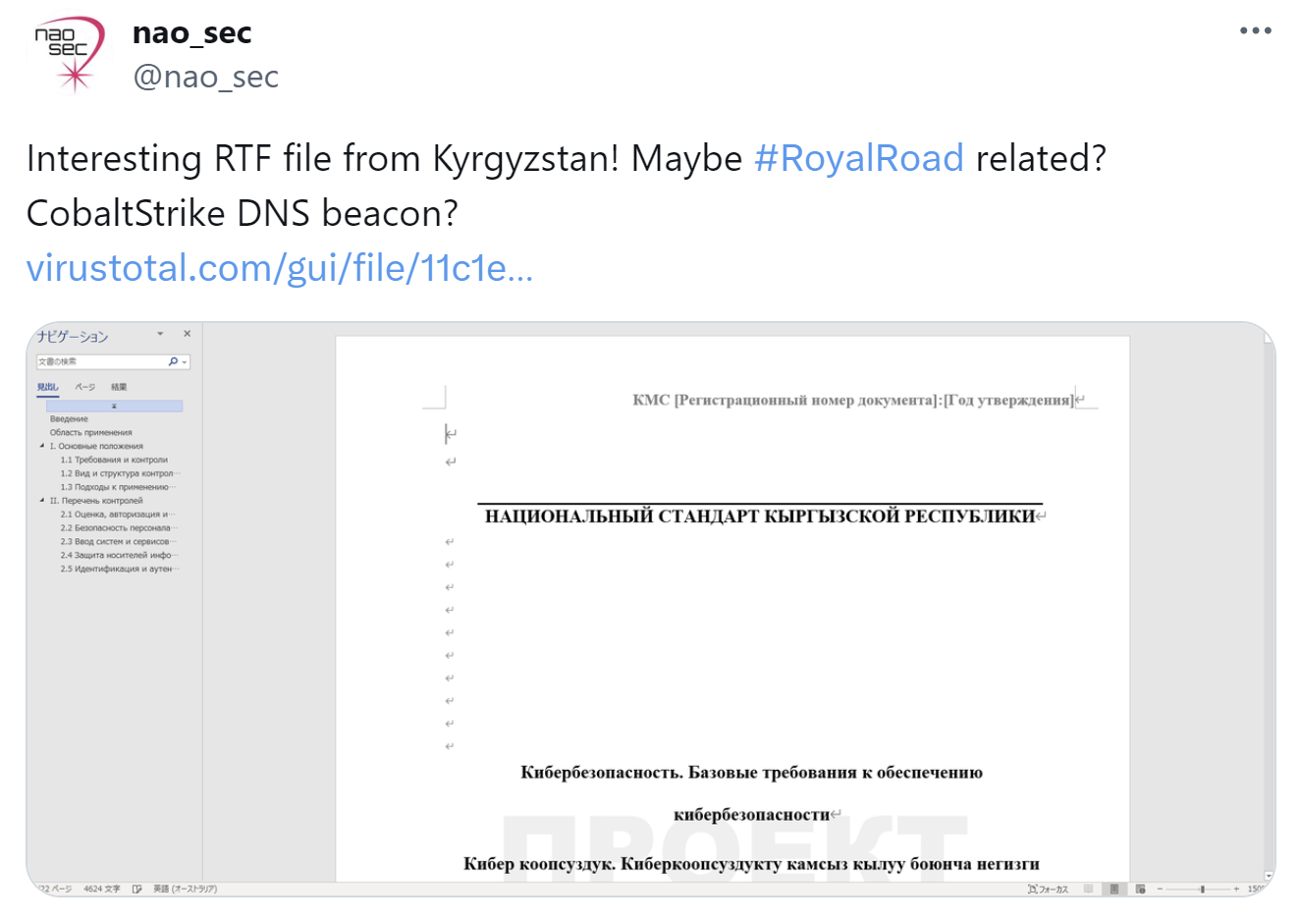
https://x.com/nao_sec/status/1648960199938707456
This attack involved a file resembling a RoyalRoad RTF, which prompted our investigation at the time. Opening this RTF file with a vulnerable version of Microsoft Word displayed a decoy file related to Kyrgyzstan’s cybersecurity, while simultaneously writing and executing several files to the disk. As a result, a CobaltStrike beacon was executed.
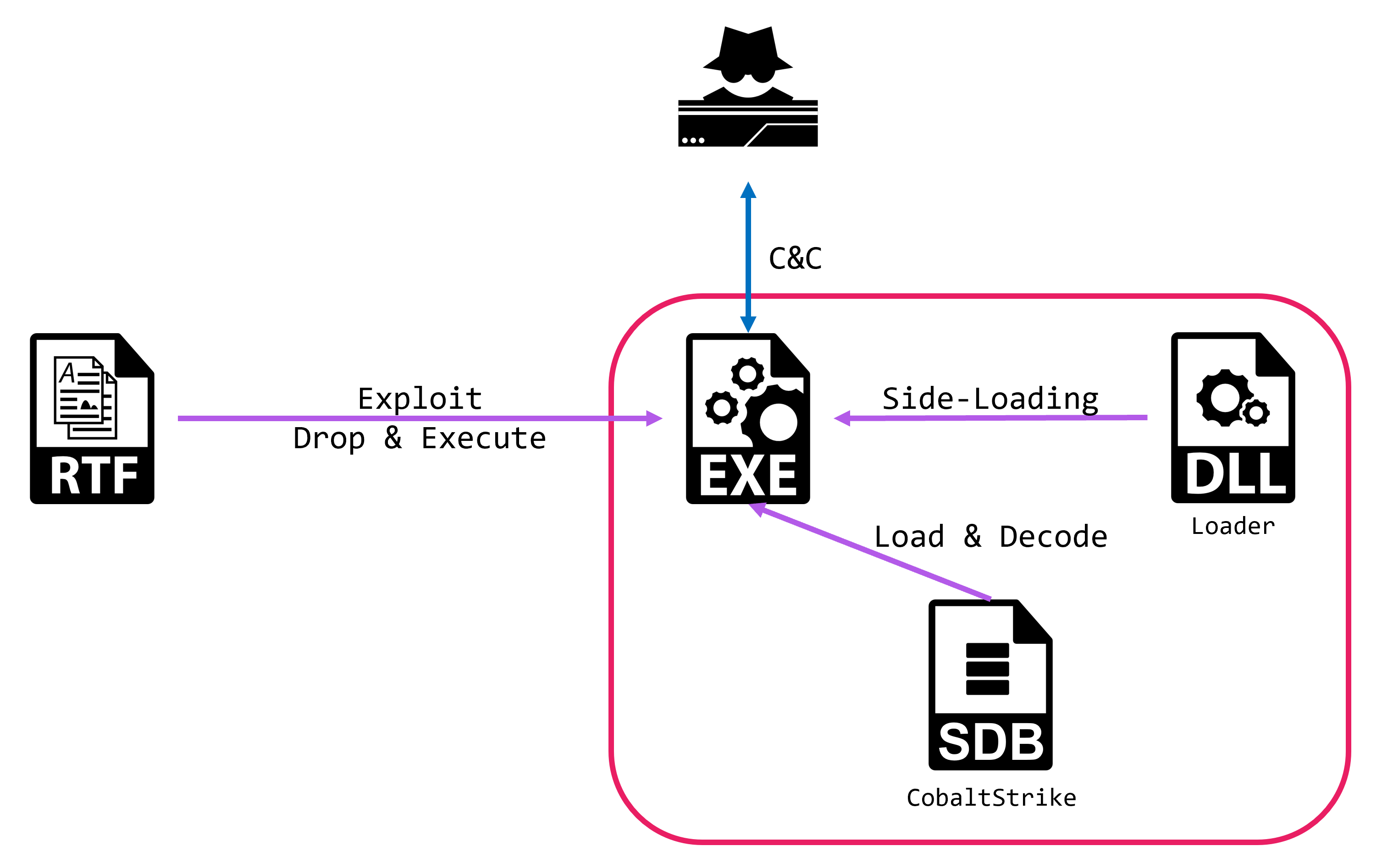
The loader that decrypted and executed the beacon resembled Casper Loader. Casper Loader is familiar to threat researchers specializing in East Asia and has been reported to be used in attacks by Tick12. Our friend @aRtAGGI conducted similar analyses at the time.
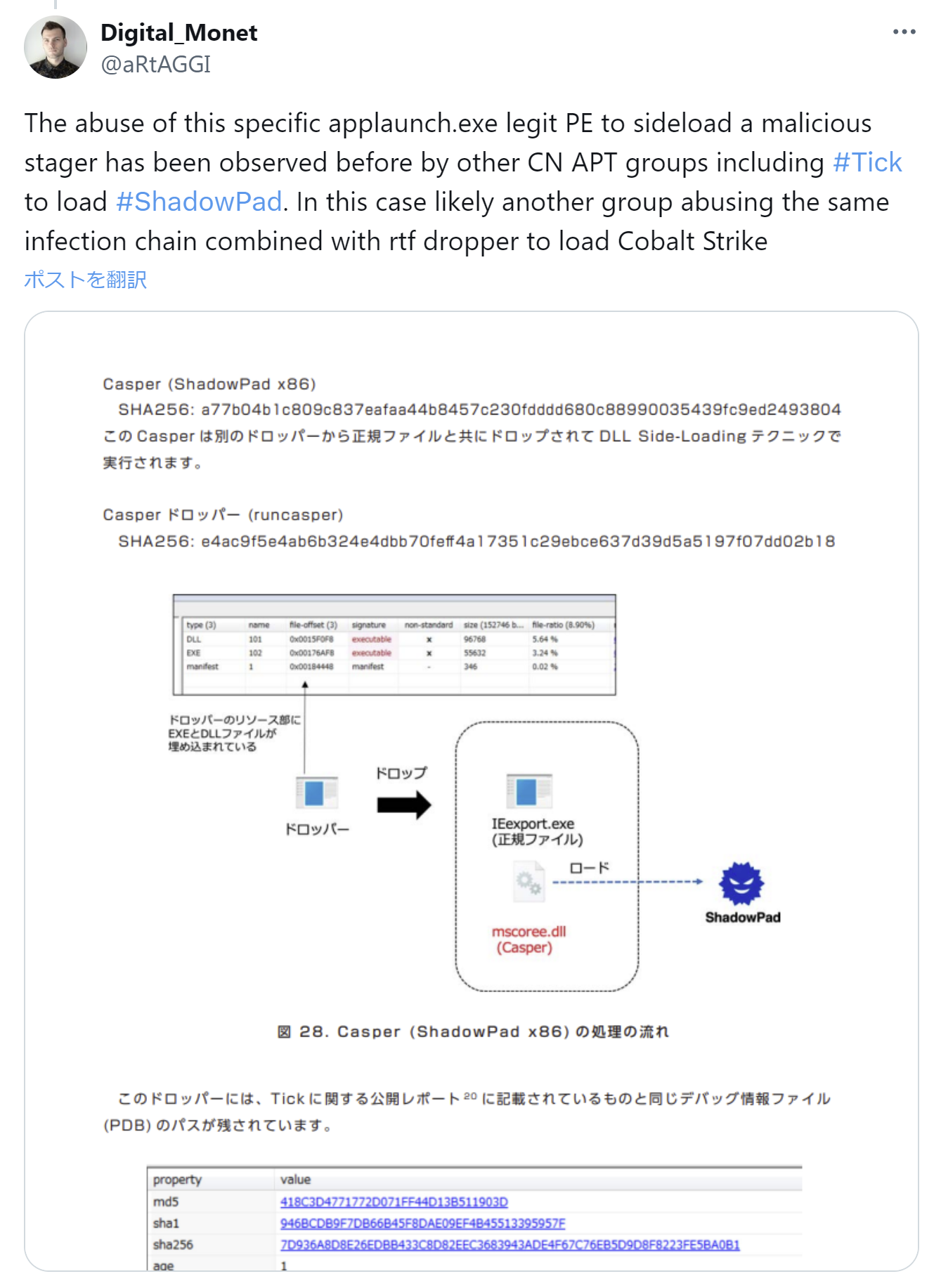
https://x.com/aRtAGGI/status/1649184131090087938
We later found that a similar attack had been carried out against Kazakhstan after searching our past database. The attack on Kazakhstan was older than the one on Kyrgyzstan, occurring around November 2022. In this case, the same loader executed from the RTF file eventually ran the CobaltStrike beacon.
Information about the RTF files used in the attacks on Kyrgyzstan and Kazakhstan is listed in the IoC sheet from our previous research on RoyalRoad RTF34. We have identified these as U-4. If you are interested, please refer to the IoC sheet.
https://nao-sec.org/jsac2020_ioc.html
Let’s return to the present. To investigate recent attack samples, we executed a search query based on the characteristics of the loader used in the attack on Kyrgyzstan.
exports:IEE2 exports:LoadLibraryShim2 exports:LoadStringRC2
We found an unusual file posted in May 2024. This data was embedded in the resource section of another file. We downloaded and executed the original file. To our surprise, it was a ShadowPad builder.
CasperVMakerHTTPx86
| MD5 | eb99580e0d90ee61b3e2e3bd8715c633 |
| SHA-1 | 706482eda6d747ca2688cdfd97399f800da9e73c |
| SHA-256 | b6d7c456423c871c7ffe418069a75c39055e4e3d023021c8b0885a02c7ce93c6 |
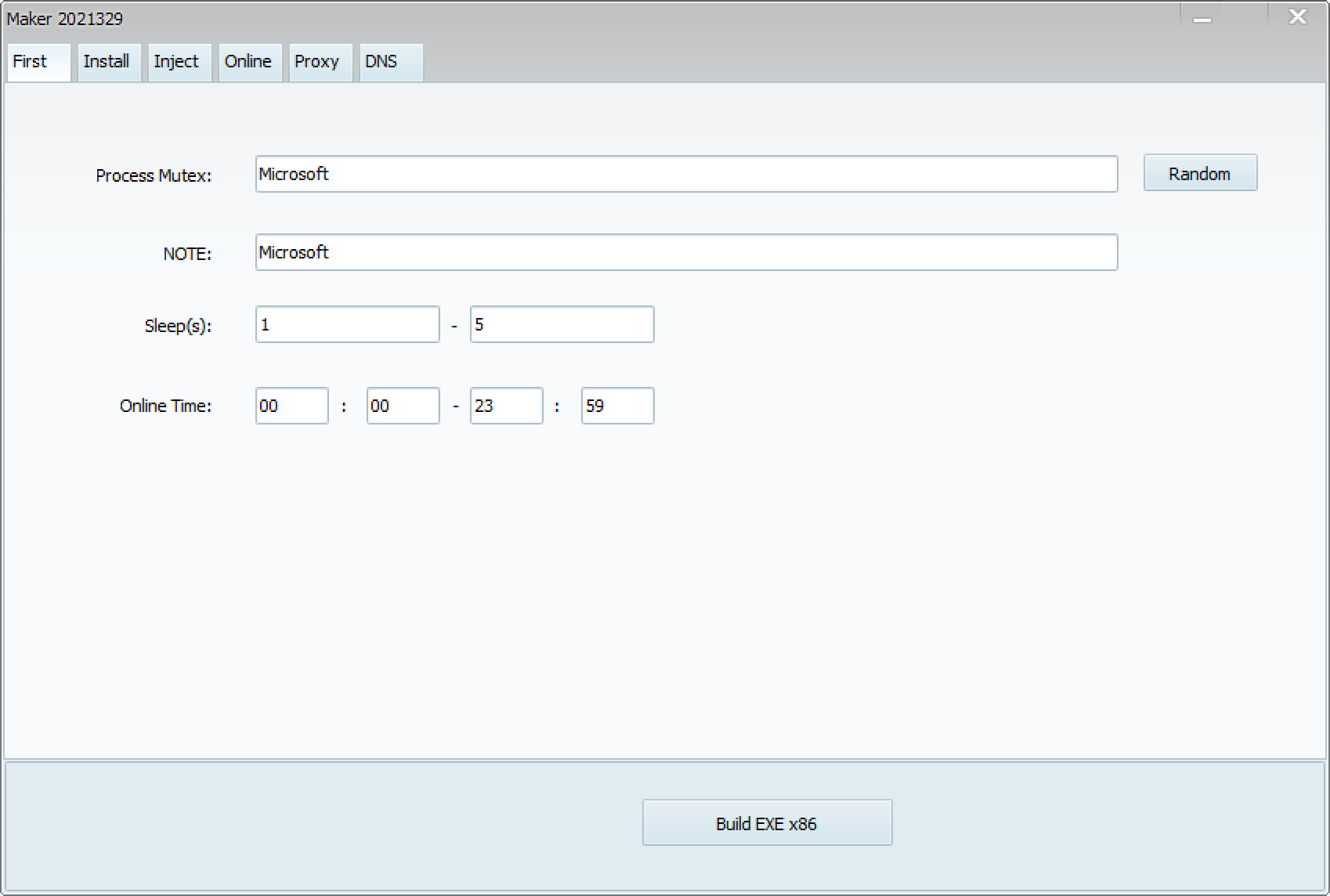
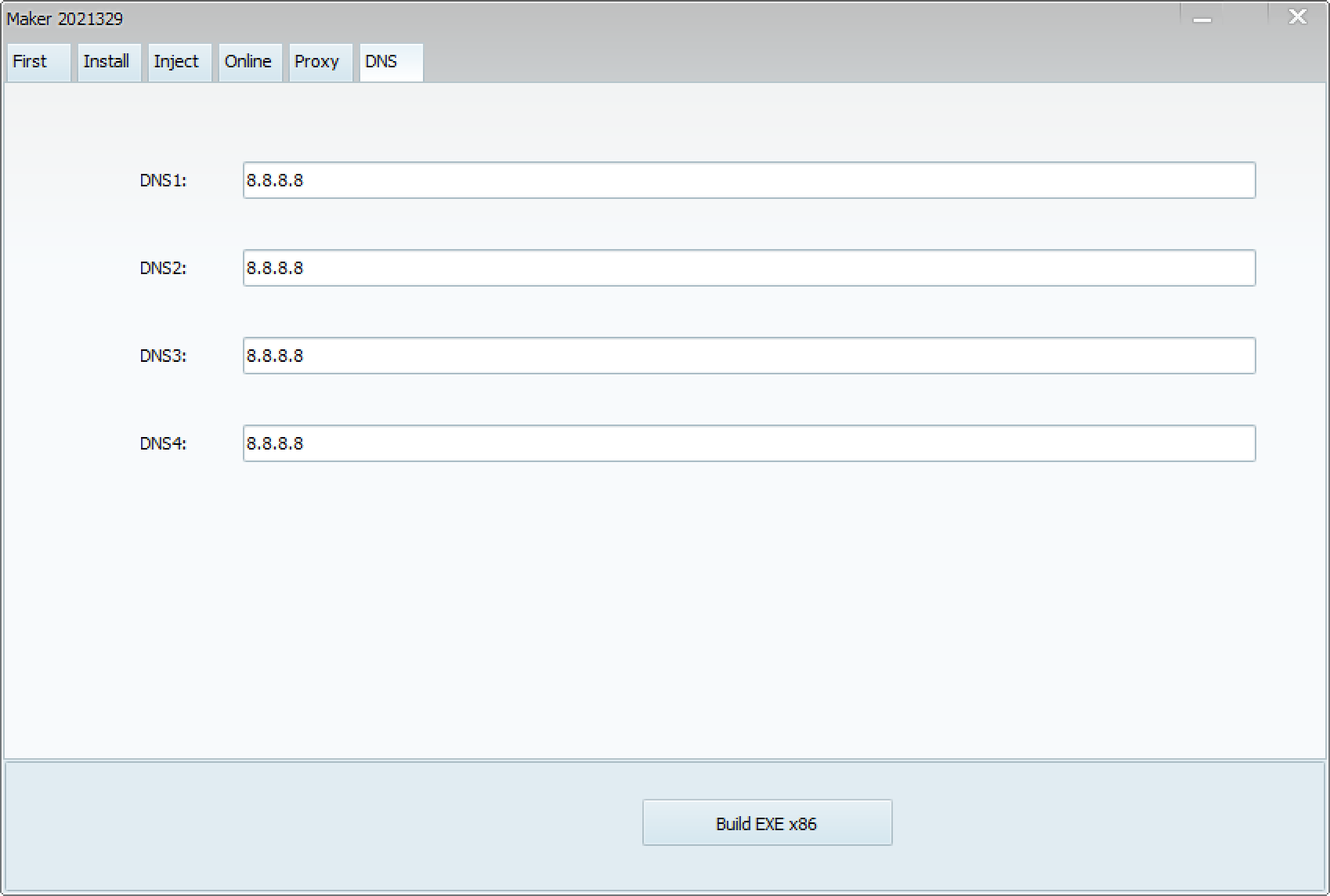
When launching the ShadowPad builder, which calls itself CasperVMakerHTTPx86, the following screen appears. There are several tabs, each with various settings.
- First
- Install
- Inject
- Online
- Proxy
- DNS
These items are very similar to the reported architecture of ShadowPad5. This suggests that these tabs are configuration items for each module. The settings for each item are as follows:
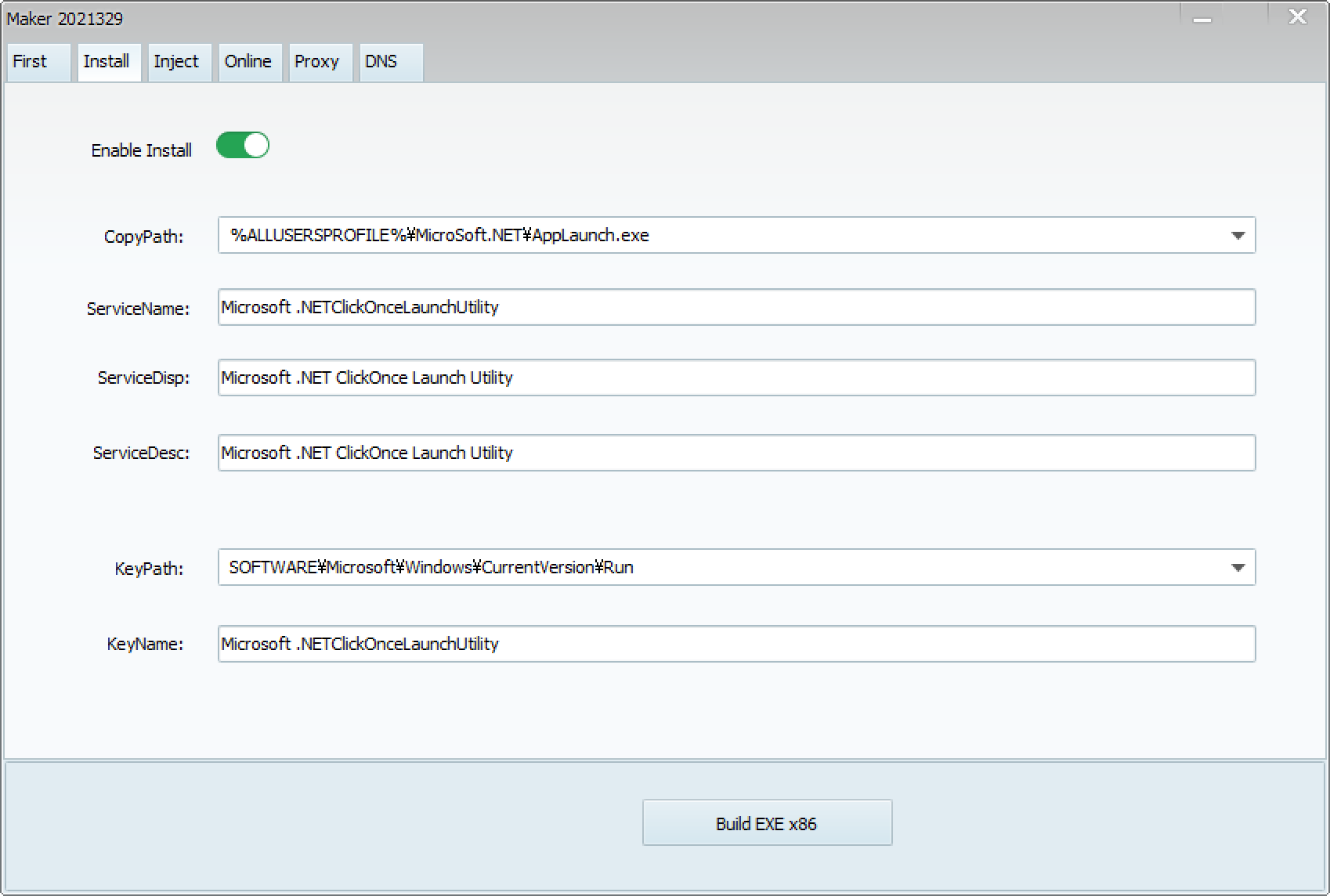
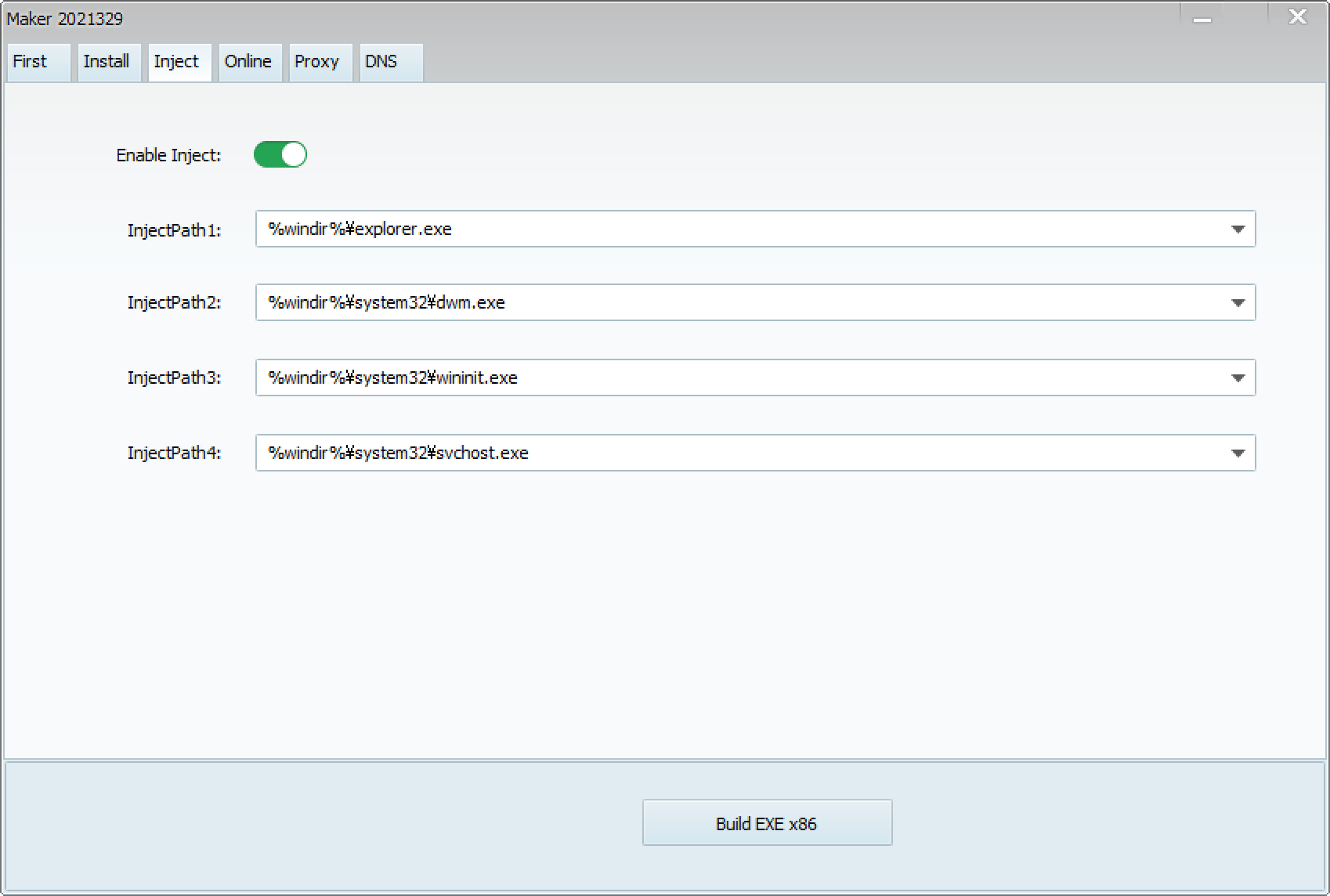
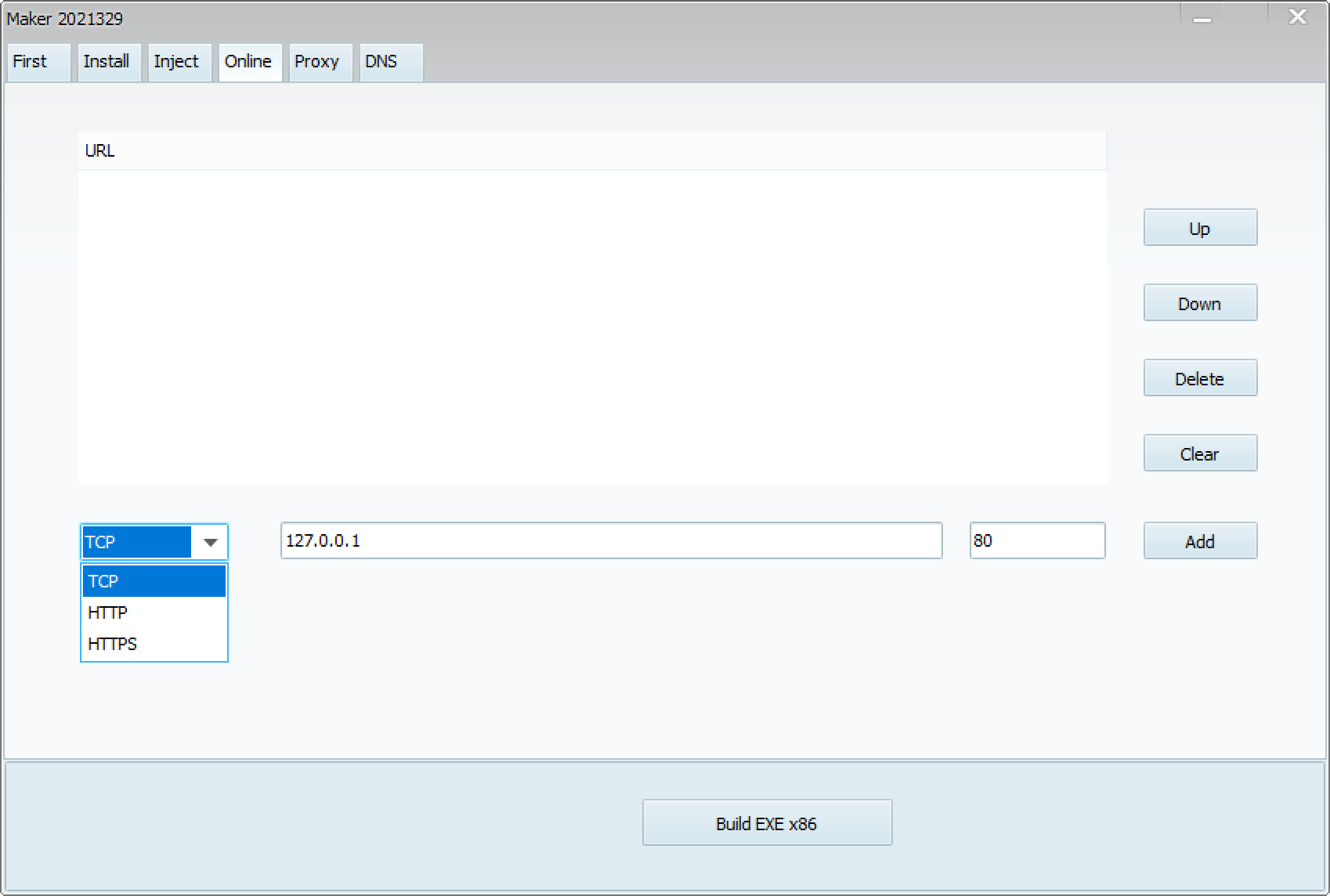
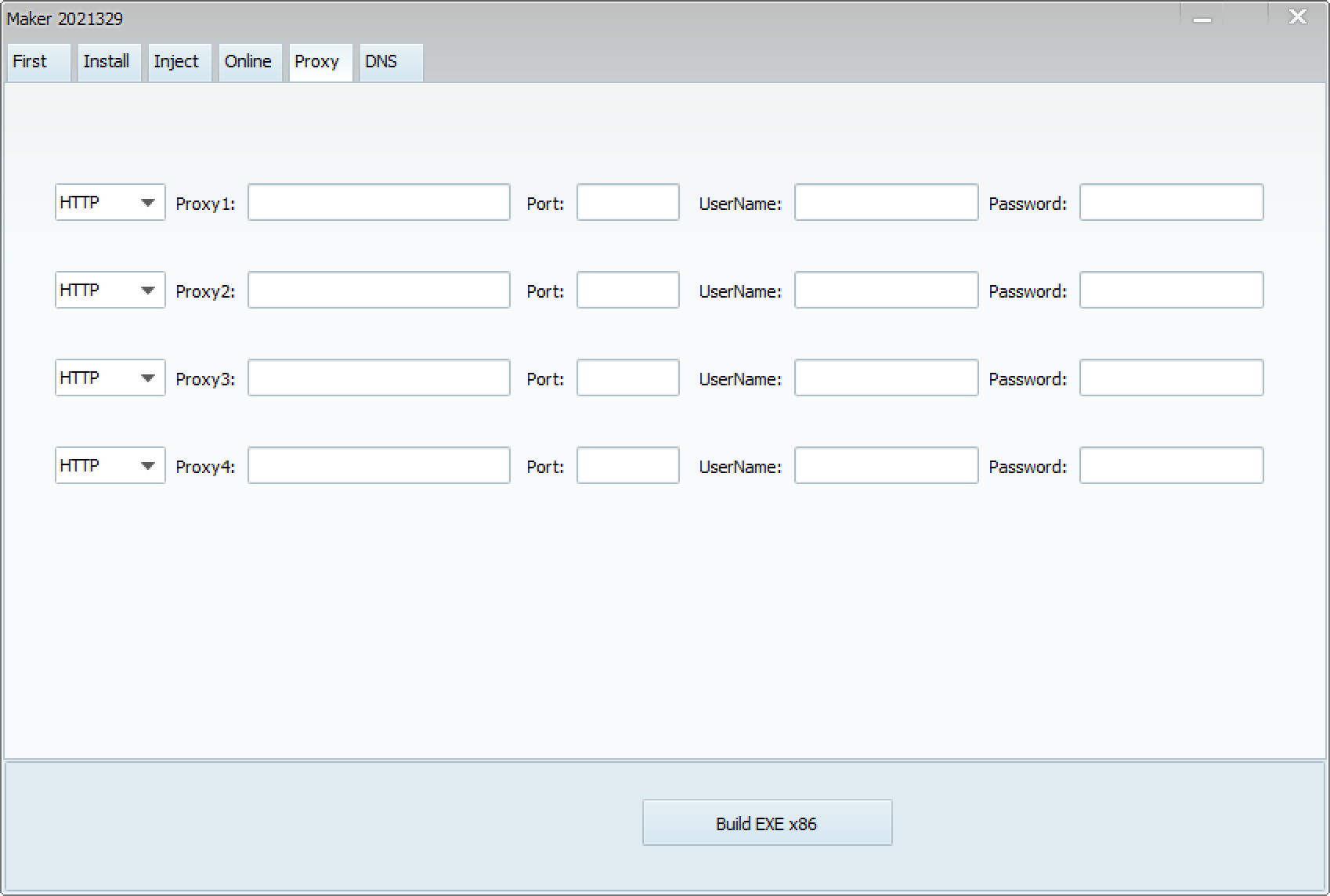
Let’s try building ShadowPad. By clicking the “Build EXE x86” button, ShadowPad is generated. If the build is successful, an EXE file and a DLL file are created.
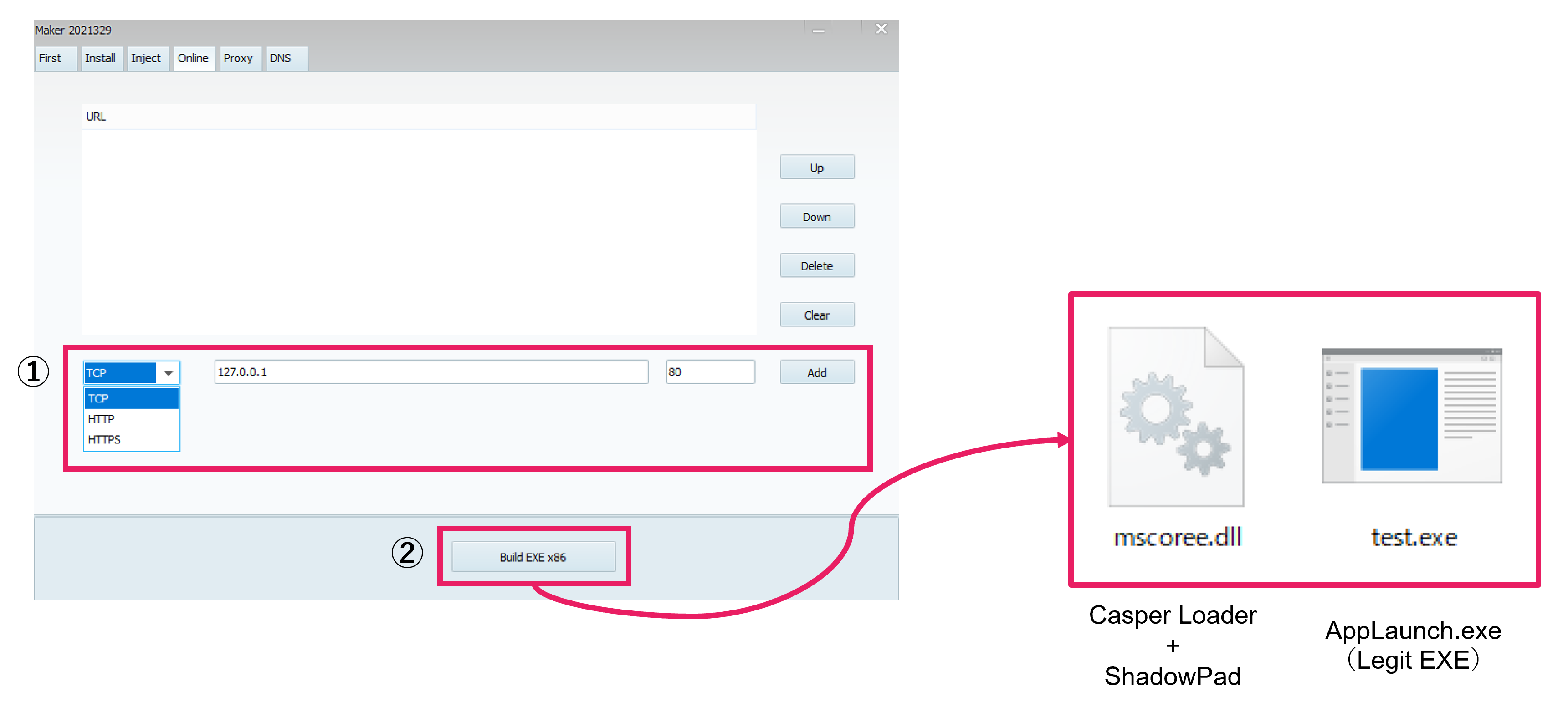
The EXE file is a legitimate AppLaunch. It loads the mscoree.dll in the same directory via DLL Side-Loading. The DLL file is the Casper Loader, which decodes and executes the ShadowPad shellcode stored internally.
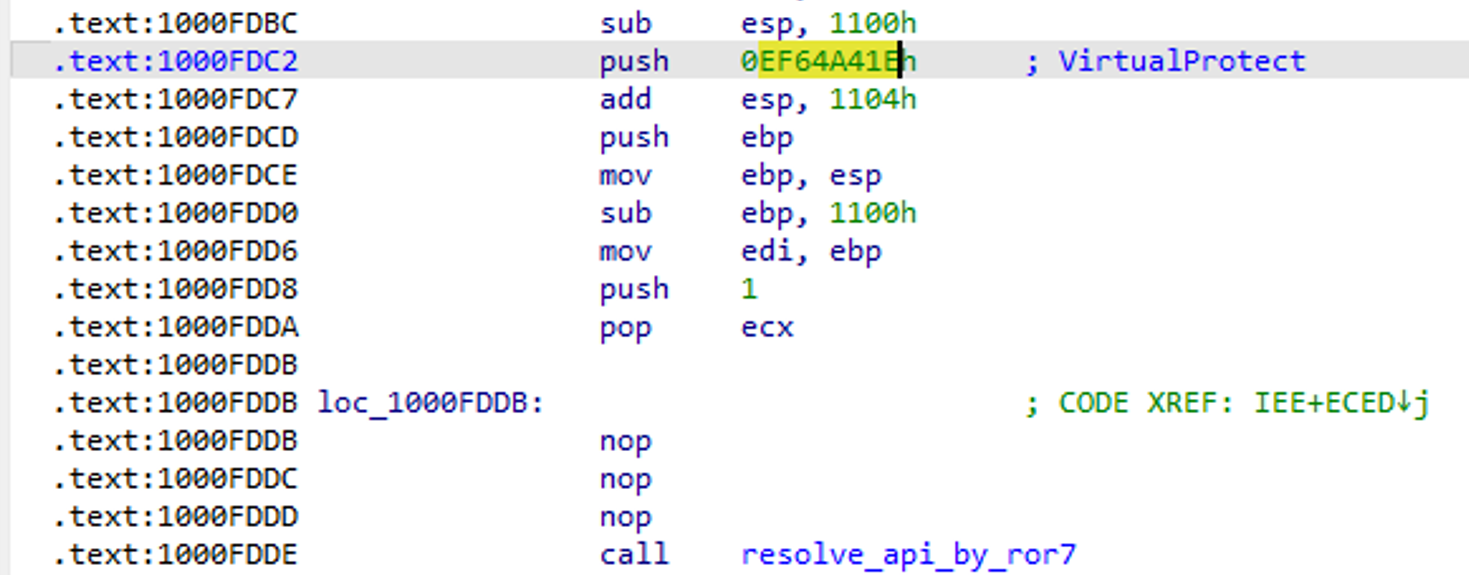
Comparison with Similar Samples
ShadowPad loaders exhibit several patterns, but those generated using this builder are decoded using a custom XOR with constants.
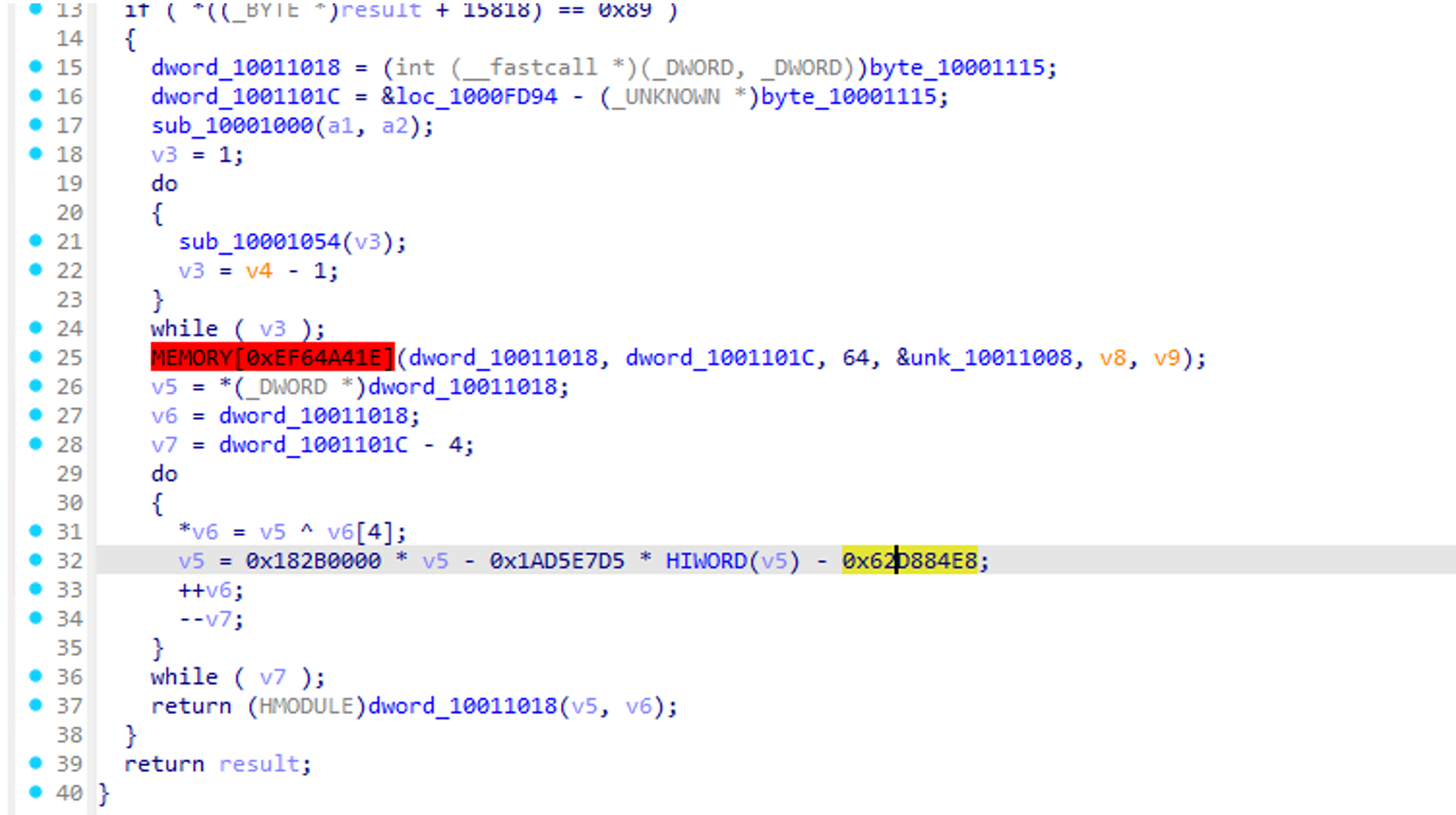
There are many samples with similar characteristics, but we will introduce two of them.
Sample-1
According to Macnica’s report2, Tick uses Casper Loader to execute ShadowPad. Comparing this Casper Loader with the loader created using the builder reveals that while the Macnica sample contains junk code and different fixed values, the algorithm is the same.
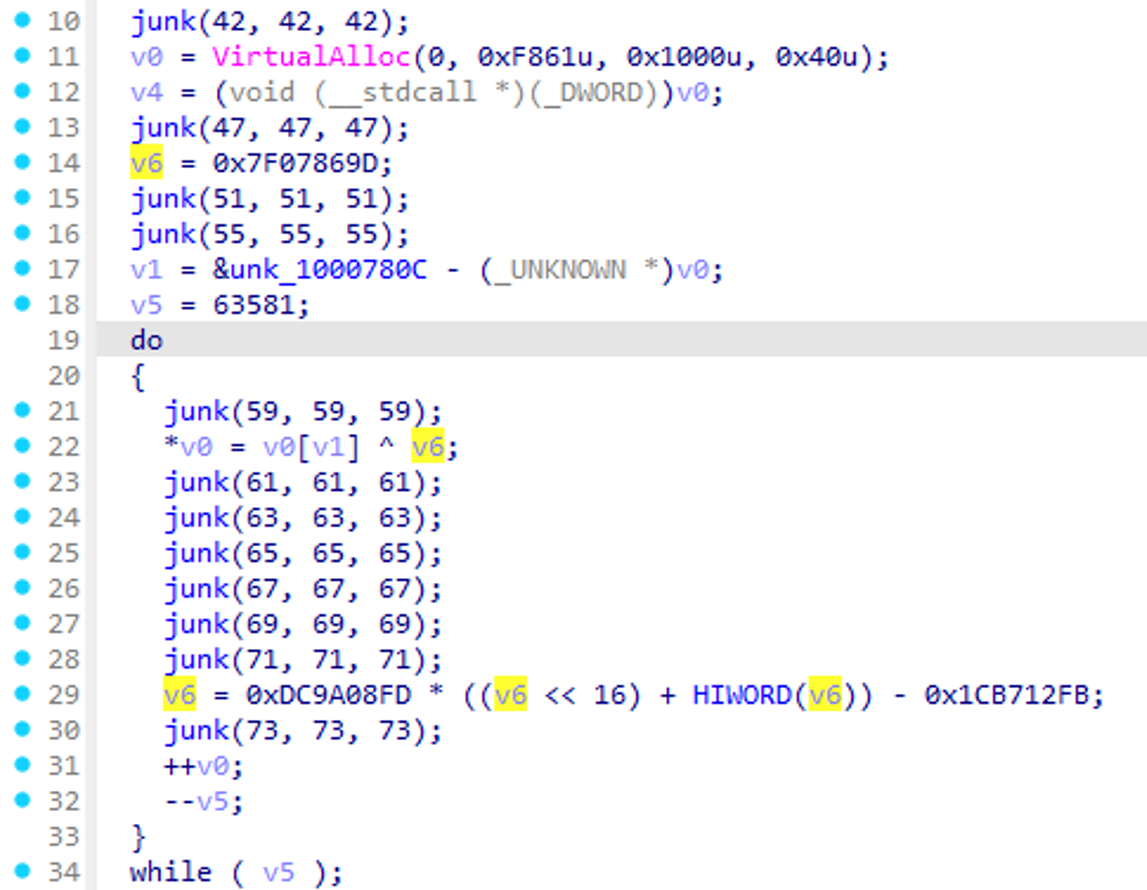
Sample-2
A report released by the FBI in December 20216 reported an attack exploiting CVE-2021-44515 where ShadowPad was used. The AppLaunch.exe and mscoree.dll in this case used Casper Loader to execute ShadowPad.
Comparing this Casper Loader with the one created using the builder shows that the algorithm and fixed values are identical. Although API Hashing is not used, it is a highly similar sample.
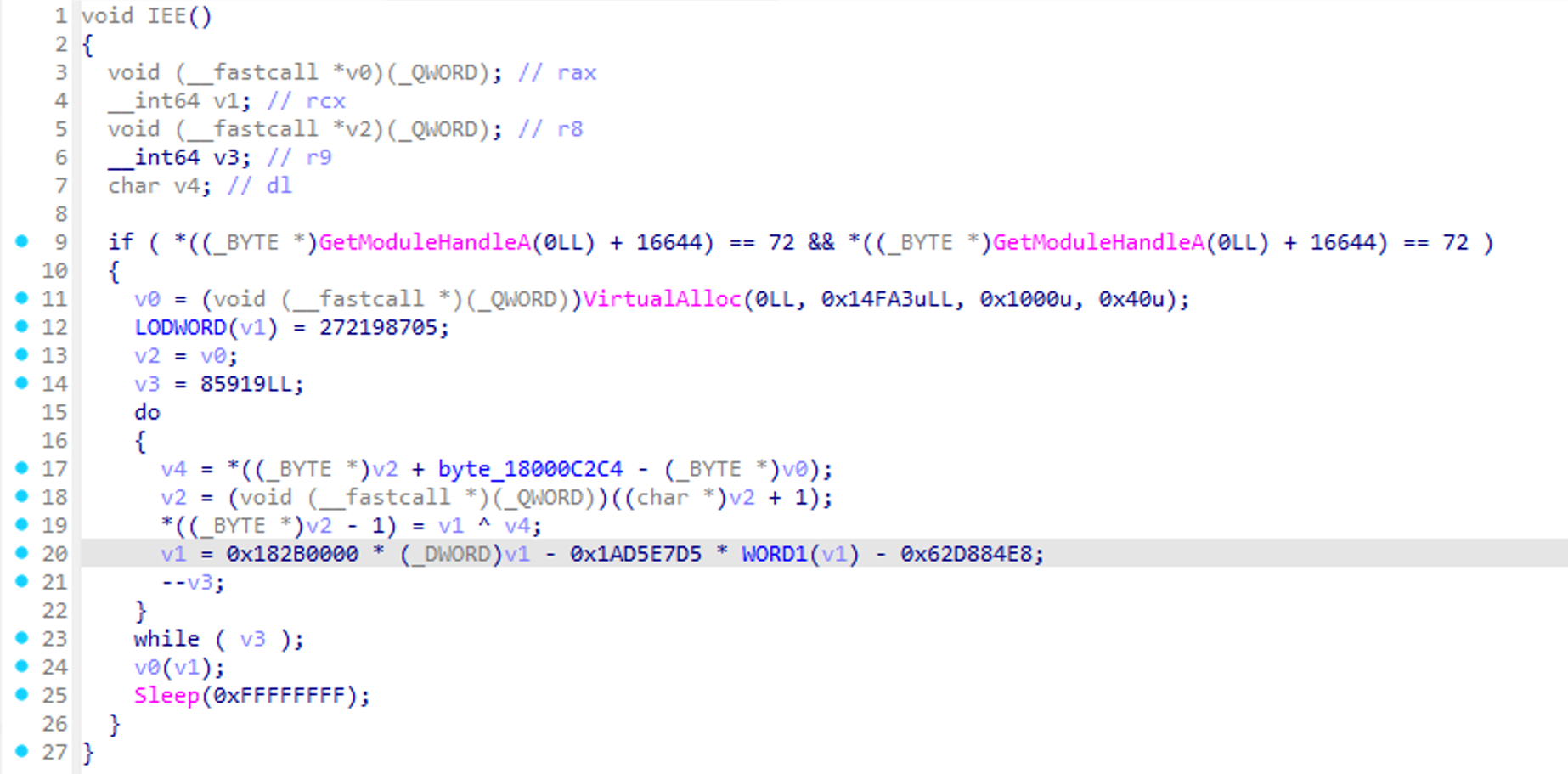
ShadowPad Community
As you know, ShadowPad is commercial software sold for profit. According to SentinelOne’s report from 20215, ShadowPad is sold to various targeted attack groups, and there is speculation that whg and Rose are involved in its development. The i-Soon leak in February 2024 reported that i-Soon was selling software that appeared to be ShadowPad (including source code and training)7.
As various researchers have reported256891011121314151617181920212223242526272829303132333435363738, many targeted attack groups use ShadowPad. These can be broadly categorized into two groups: attack groups associated with the MSS, like APT41, and those associated with the PLA, like Tick.
As previously mentioned, it is generally believed that whg and Rose were involved in ShadowPad’s development. There is no compelling reason to refute this, so we will proceed with this assumption. According to a U.S. government report related to APT4139, Rose (Tan Dailin) was involved in APT41. Seven individuals were indicted for their involvement with APT41, with Rose (and Zhang Haoran) being particularly noted for their involvement in both BARIUM and LEAD, making them key figures in APT41’s activities. This background suggests that BARIUM was the earliest adopter of ShadowPad, followed by LEAD.
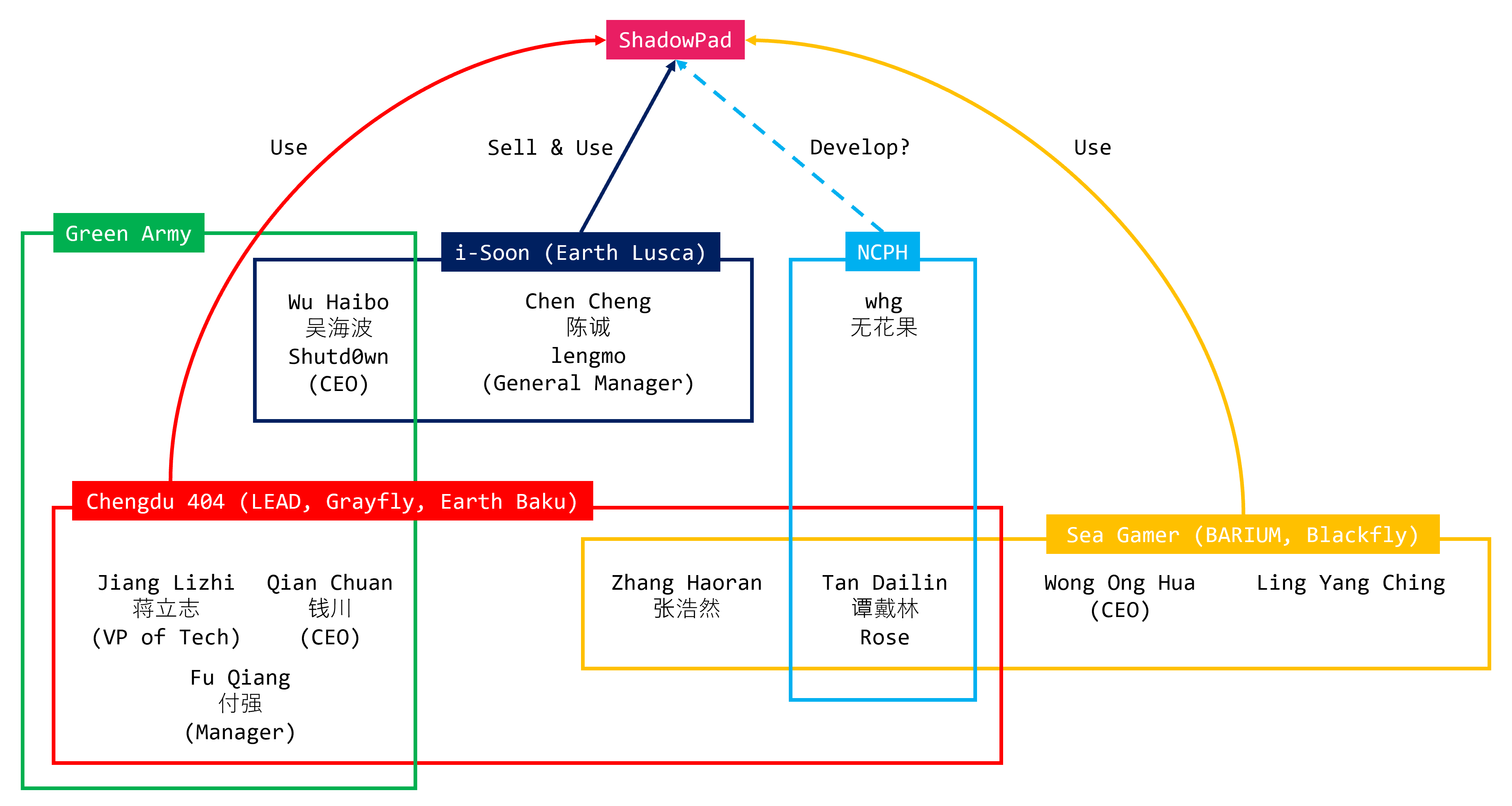
In contrast, the PLA has many more attack groups using ShadowPad than the MSS. This is generally because many researchers have given them different names, and their relationships are not sufficiently organized. If you are a researcher, you probably have more organized information in your mind (or within your organization). Of course, we understand and accept this. However, to keep things simple, we will exclude such discussions in this article and share how we organized this information within nao_sec. Interestingly, all these attack groups used the RoyalRoad RTF Weaponizer. Is this just a coincidence? ShadowPad and RoyalRoad RTF Weaponizer may be shared through the same channels.
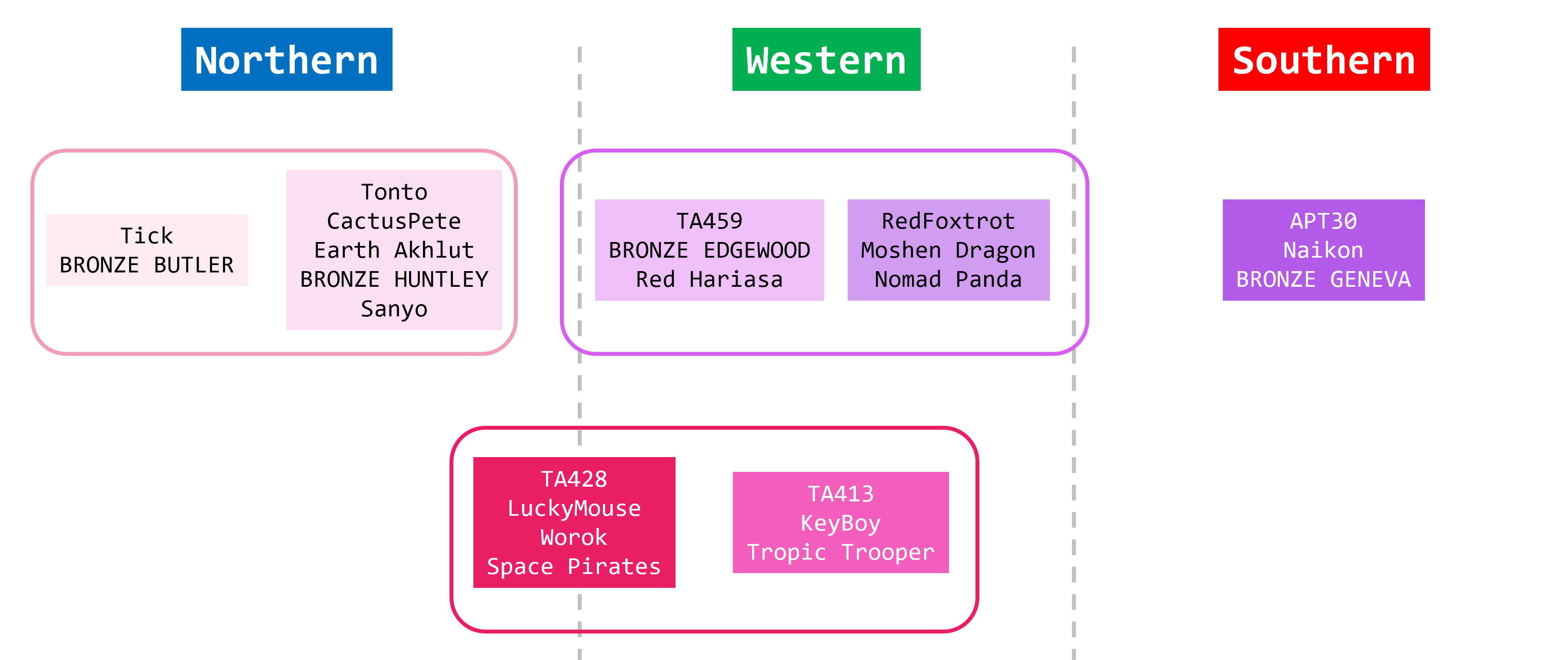
Conclusion
In this article, we introduced the ShadowPad builder. ShadowPad, widely used by various targeted attack groups as a successor to PlugX, had limited information available about its builder until now. This article sheds light on how attackers build ShadowPad.
We also organized the relationships between attack groups using ShadowPad. Our research is still ongoing. We would love to engage in active discussions. If you have any opinions or comments, please contact us. We look forward to hearing from you.
Acknowledgments
We received a lot of help from our friends in writing this article. While we won’t name individuals here, we are immensely grateful to the many supportive reviewers. We want to take this opportunity to express our deepest gratitude to you.
References
-
TrendMicro, “Operation ENDTRADE: TICK’s Multi-Stage Backdoors for Attacking Industries and Stealing Classified Data”, https://documents.trendmicro.com/assets/pdf/Operation-ENDTRADE-TICK-s-Multi-Stage-Backdoors-for-Attacking-Industries-and-Stealing-Classified-Data.pdf ↩
-
マクニカ, “標的型攻撃の実態と対策アプローチ 第5版 日本を狙うサイバーエスピオナージの動向 2020年度”, https://www.macnica.co.jp/business/security/manufacturers/files/mpressioncss_ta_report_2020_5.pdf ↩ ↩2 ↩3
-
nao_sec, “An Overhead View of the Royal Road”, https://nao-sec.org/2020/01/an-overhead-view-of-the-royal-road.html ↩
-
nao_sec, “Royal Road! Re:Dive”, https://nao-sec.org/2021/01/royal-road-redive.html ↩
-
SentinelOne, “ShadowPad A Masterpiece of Privately Sold Malware in Chinese Espionage”, https://www.sentinelone.com/labs/shadowpad-a-masterpiece-of-privately-sold-malware-in-chinese-espionage/ ↩ ↩2 ↩3
-
FBI, “APT Actors Exploiting Newly-Identified Zero Day in ManageEngine Desktop Central”, https://www.ic3.gov/Media/News/2021/211220.pdf ↩ ↩2
-
HarfangLab, “A comprehensive analysis of I-Soon’s commercial offering”, https://harfanglab.io/en/insidethelab/isoon-leak-analysis/ ↩
-
Kaspersky, “ShadowPad in corporate networks”, https://securelist.com/shadowpad-in-corporate-networks/81432/ ↩
-
Kaspersky, “Operation ShadowHammer”, https://securelist.com/operation-shadowhammer/89992/ ↩
-
ESET, “Connecting the dots: Exposing the arsenal and methods of the Winnti Group”, https://www.welivesecurity.com/2019/10/14/connecting-dots-exposing-arsenal-methods-winnti/ ↩
-
ESET, “Winnti Group targeting universities in Hong Kong”, https://www.welivesecurity.com/2020/01/31/winnti-group-targeting-universities-hong-kong/ ↩
-
マクニカ, “標的型攻撃の実態と対策アプローチ 第4版 日本を狙うサイバーエスピオナージの動向 2019年度下期”, https://www.macnica.co.jp/business/security/manufacturers/files/mpressioncss_ta_report_2019_4.pdf ↩
-
PwC, “Around the world in 80 days 4.2bn packets”, https://www.youtube.com/watch?v=YCwyc6SctYs ↩
-
CrowdStrike, “Manufacturing Industry in the Adversaries’ Crosshairs”, https://www.crowdstrike.com/blog/adversaries-targeting-the-manufacturing-industry/ ↩
-
Kaspersky, “APT trends report Q2 2020”, https://securelist.com/apt-trends-report-q2-2020/97937/ ↩
-
Positive Technologies, “ShadowPad: new activity from the Winnti group”, https://www.ptsecurity.com/upload/corporate/ww-en/pt-esc/winnti-2020-eng.pdf ↩
-
Symantec, “APT41: Indictments Put Chinese Espionage Group in the Spotlight”, https://symantec-enterprise-blogs.security.com/threat-intelligence/apt41-indictments-china-espionage ↩
-
Dr.Web, “Study of the ShadowPad APT backdoor and its relation to PlugX”, https://st.drweb.com/static/new-www/news/2020/october/Study_of_the_ShadowPad_APT_backdoor_and_its_relation_to_PlugX_en.pdf ↩
-
TrendMicro, “Earth Akhlut: Exploring the Tools, Tactics, and Procedures of an Advanced Threat Actor Operating a Large Infrastructure”, https://vblocalhost.com/uploads/VB2020-Lunghi-Horejsi.pdf ↩
-
ESET, “Operation StealthyTrident: corporate software under attack”, https://www.welivesecurity.com/2020/12/10/luckymouse-ta428-compromise-able-desktop/ ↩
-
Positive Technologies, “Higaisa or Winnti? APT41 backdoors, old and new”, https://www.ptsecurity.com/ww-en/analytics/pt-esc-threat-intelligence/higaisa-or-winnti-apt-41-backdoors-old-and-new/ ↩
-
Recorded Future, “China-Linked Group RedEcho Targets the Indian Power Sector Amid Heightened Border Tensions”, https://go.recordedfuture.com/hubfs/reports/cta-2021-0228.pdf ↩
-
Recorded Future, “Chinese State-Sponsored Activity Group TAG-22 Targets Nepal, the Philippines, and Taiwan Using Winnti and Other Tooling”, https://www.recordedfuture.com/blog/chinese-group-tag-22-targets-nepal-philippines-taiwan ↩
-
TrendMicro, “Delving Deep: An Analysis of Earth Lusca’s Operations”, https://www.trendmicro.com/content/dam/trendmicro/global/en/research/22/a/earth-lusca-employs-sophisticated-infrastructure-varied-tools-and-techniques/technical-brief-delving-deep-an-analysis-of-earth-lusca-operations.pdf ↩
-
Secureworks, “ShadowPad Malware Analysis”, https://www.secureworks.com/research/shadowpad-malware-analysis ↩
-
Recorded Future, “Continued Targeting of Indian Power Grid Assets by Chinese State-Sponsored Activity Group”, https://go.recordedfuture.com/hubfs/reports/ta-2022-0406.pdf ↩
-
SentinelOne, “Moshen Dragon’s Triad-and-Error Approach Abusing Security Software to Sideload PlugX and ShadowPad”, https://www.sentinelone.com/labs/moshen-dragons-triad-and-error-approach-abusing-security-software-to-sideload-plugx-and-shadowpad/ ↩
-
TeamT5, “The Next Gen PlugX - ShadowPad - A Dive into the Emerging China-Nexus Modular Trojan, Pangolin8RAT”, https://i.blackhat.com/Asia-22/Thursday-Materials/AS-22-LeonSilvia-NextGenPlugXShadowPad.pdf ↩
-
Positive Technologies, “Space Pirates: analyzing the tools and connections of a new hacker group”, https://www.ptsecurity.com/ww-en/analytics/pt-esc-threat-intelligence/space-pirates-tools-and-connections/ ↩
-
Kaspersky, “Attacks on industrial control systems using ShadowPad”, https://ics-cert.kaspersky.com/publications/reports/2022/06/27/attacks-on-industrial-control-systems-using-shadowpad/ ↩
-
ESET, “Worok: The big picture”, https://www.welivesecurity.com/2022/09/06/worok-big-picture/ ↩
-
Elastic, “Update to the REF2924 intrusion set and related campaigns”, https://www.elastic.co/security-labs/update-to-the-REF2924-intrusion-set-and-related-campaigns ↩
-
Symantec, “Lancefly: Group Uses Custom Backdoor to Target Orgs in Government, Aviation, Other Sectors”, https://symantec-enterprise-blogs.security.com/threat-intelligence/lancefly-merdoor-zxshell-custom-backdoor ↩
-
TrendMicro, “Possible Supply-Chain Attack Targeting Pakistani Government Delivers Shadowpad”, https://www.trendmicro.com/en_us/research/23/g/supply-chain-attack-targeting-pakistani-government-delivers-shad.html ↩
-
Recorded Future, “RedHotel: A Prolific, Chinese State-Sponsored Group Operating at a Global Scale”, https://go.recordedfuture.com/hubfs/reports/cta-2023-0808.pdf ↩
-
Symantec, “Redfly: Espionage Actors Continue to Target Critical Infrastructure”, https://symantec-enterprise-blogs.security.com/threat-intelligence/critical-infrastructure-attacks ↩
-
Palo Alto Networks, “Cyberespionage Attacks Against Southeast Asian Government Linked to Stately Taurus, Aka Mustang Panda”, https://unit42.paloaltonetworks.com/stately-taurus-attacks-se-asian-government/ ↩
-
TrendMicro, “Earth Krahang Exploits Intergovernmental Trust to Launch Cross-Government Attacks”, https://www.trendmicro.com/en_us/research/24/c/earth-krahang.html ↩
-
United States Department of Justice, “Seven International Cyber Defendants, Including “Apt41” Actors, Charged In Connection With Computer Intrusion Campaigns Against More Than 100 Victims Globally”, https://www.justice.gov/opa/pr/seven-international-cyber-defendants-including-apt41-actors-charged-connection-computer ↩
 nao_sec
nao_sec